
SPONSORED
Time, Energy, Money, Quality: Total Cost of Ownership and your security success
- By Steve Surfaro
- Nov 02, 2016
Introduction
Total cost of ownership, or TCO, is a way to assess direct and indirect costs and benefits related to the purchase of any IT component. The goal is to create a total estimate of fixed and variable costs that may be used for budget development.
The American Automobile Association (AAA) says that, on average, it costs 52.2 cents to drive one mile. To drive a Ford Focus 20K miles per year, the average cost is 37.6 cents per mile.
Based on J.D. Roth’s vehicle purchase price ($16,500), interest paid ($1,300), actual mileage (82K over 5 ½ years), fuel ($1,650, $0.0812 per mile), insurance ($765, $0.0376 per mile) and service ($507.07, $0.0250 per mile), the actual TCO/mile is 36 cents, pretty much the same as the AAA estimate.
In The Millionaire Next Door, one of the best-performing groups in terms of personal net worth were “quality used car prone” people. These folks buy a car with an excellent service record that is 3 to 5 years old and drives it for many years, contributing to very high net worth.
With security solutions, purchasing compliance, quality, efficiency and stability is not too far off from our “millionaire.” Purchasing a lower cost video surveillance camera may not be very efficient in digital storage, when compared with next generation compression technologies like Zipstream.
Significantly more efficient implementation of AVC/h.264 video encoding, and purpose-built for surveillance applications, the Zipstream compression technology analyzes and optimizes the video stream in real time to save bandwidth and storage while maintaining image quality. This technology makes it possible to even use Pan-Tilt-Zoom positionable cameras for optimum viewing on demand while reducing the storage requirements. Important forensic details such as facial features, vehicle plates are preserved, while scene elements that stay constant like walls, land and other surfaces are rendered at a higher compression.
In the figure below, the amount of storage space reclaimed by using cameras having the lower-bitrate and storage efficient Zipstream compression offers users the choice of longer recordings or adding additional surveillance cameras for enhanced coverage.
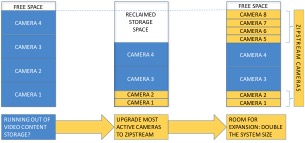
Figure 1 Zipstream savings
Also, the costs to “rip out” a non-compliant or cyber-vulnerable system can be many times greater than the cost difference of the next higher qualified bid that offers compliance.
Ransomware is a rapidly emerging and more prominently measureable cyber breach cost that targets weaknesses in networks in an effort to deny the availability of critical data and systems. According to the Herjavec Group, the amount paid out by victims of ransomware in just the first three months of this year came to a total of $209 million. The report suggests that at that rate, the total cost of ransomware is set to reach $1 billion for all of 2016.
Begin with a plan
Some questions need be asked before performing any TCO analysis:
Do you have enough security? How do you leverage technologies already in the security program and make improvements with high ROI? How do I make the program sustainable, or able to be maintained, expanded and improved within budget? How do I satisfy compliance requirements for my industry? How to I reasonably manage risk?
All of these questions lead to one significant conclusion: What you need is a Security Master Plan.
You’ll need to explore and focus on potential areas to build a Security Master Plan (SMP), keeping in mind it may be used for other emerging missions, like Cyber Strategy and Sustainability.
Application-First TCO
Would you buy a smartphone or tablet with applications only developed by the platform vendor? This is the value of solution application developer programs managed by the device or core platform vendor and offering a wide range of choices. For example, Axis Communications Camera Applications Platform (ACAP) offers video analytic solution providers like the following to offer unique processes that run right inside the camera and increase the value of its data:
- People counting – allocate staff with customer activity patterns and temporal behavior
- Vehicle License Plate recognition for remote gate control and monitoring from mobile security officer or centralized location – better staff allocation and employee security experience, increased parking revenue
- Long Range Object Detection – early warning of perimeter breaches for high risk and critical infrastructure facilities
- Perimeter Intrusion Detection alarm confirmation (two modes) for reducing the costs associated with false alarms
- Smokecatcher for early warning of potential life safety issue
- Acoustic signature detection for rapid response in active shooter scenarios
Each one of these are COTS Apps permitting the end user to leverage security solutions, collaborate with other departments or agencies and achieve lower TCO.
There are numerous software costs to be considered in our project and the details grow in just the application category. Security applications at the start have a number of complex costs:
- Software licenses: consider group and per-user models
- Server and infrastructure costs: yes, consider eliminating this by leveraging the cloud
- Customization to meet needs: do you really want to do this? You may be in for both a shortened application lifecycle if customizations prevent upgrades to the base product, more expensive upgrade costs or worse yet, full replacement.
- Professional services make the software functional in your environment
- Training costs
- Thin client and other user software user interface needs
Recurring costs:
- Annual software maintenance costs
- Internal costs to support the application
- Planned upgrade costs for enhanced functionality (usually every 2-3 years)
Productivity savings
- Improved productivity and metrics
- Reports
- Mobile alerts and functionality
- Collaborative interdepartmental tools
- Matching solution provider innovation to the organization’s success trajectory
Cloud-First TCO: meet the millionaire next door
So much is discussed about “migrating to the cloud,” that many organizations do not realize that many simple services your security solution depends on, are already there!
Companies use COTS apps to meet IT requirements while avoiding costs. Through COTS, maintenance expenses may be reduced without cutting back on necessary features. Investing in a COTS solution may lower the initial cost and include cost-effective new upgrades with new features. Nonetheless, you need to do a gap analysis to see what features you need that are not provided by the COTS package.
The following are ten considerations to evaluate; you may just leverage Cloud-First to lower TCO:
- The benefits lie in optimizing the security processes you support; can you lower the existing investment in hardware, software, and facilities, yet still comply with laws and regulatory pressures?
- IT can react much faster and more effectively to changes in the business
- How much do you have invested in a data center? Moving to a cloud solution won’t leverage investments already made in servers. Putting cloud first, before these costs, is far more efficient at lowering TCO.
- Will your team require new skills with the cloud-based solution?
- What’s the cost of migrating Apps to the cloud? In many cases, more superior features for your existing security solution are already there. Look at Microsoft’s Office365, for example, which consistently delivers improved features and streamlined upgrades.
- What are the actual subscription costs? Do these change with your increased security operation?
- Let’s measure the Elasticity (shrink and grow) and Agility of your cloud-based security app. Where will it benefit your organization? Will this reduce on-site security cost for new facilities?
- What capital costs will you avoid? Traditional servers are costly and cloud-first has “virtually” eliminated them!
- The Risk and Cost of compliance and non-compliance, especially with healthcare or finance markets.
- The money’s in the data – do you have the right cloud partner to analyze?
Especially with items 1,6 and 8, there are numerous cloud infrastructure cost analysis tools available. The figures below show several TCO details for the Amazon Web Services (AWS) model.
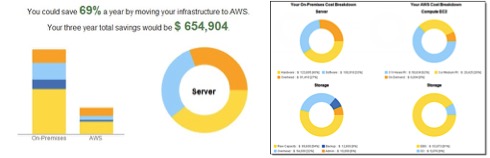
Figure 1 Example TCO Analysis using AWS Calculator
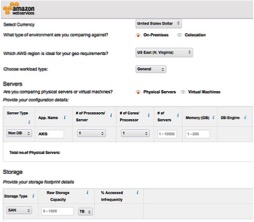
Figure 2 Server and Storage Estimator using AWS TCO Calculator
What have you done for your IT manager today?
The path to accurate IT TCO estimation begins with “benchmarking” yours or your customer’s operational spending levels by comparing them with similar business by size and industry sector.
Consider IT support metrics, such as IT budget as a percent of revenue and IT spending per employee, allowing IT executives to highlight opportunities to reduce IT costs and optimize IT expenses:
- Measure your IT capital budget spend levels
- Analyze your IT staffing levels.
- Evaluate your IT key performance indicators. Compare your IT use and infrastructure metrics with your company peers, using measures such as new initiative spending, software mix, virtualization ratios, users per server and per printer, Client performance and other KPIs.
Are you a Small or Medium-Sized Business (SMB) or are you supporting this growing category using security solutions? Have you considered using commercial off-the-shelf (COTS) software delivered by a cloud solution? Many logistics or IT executives have thought their operations were unique, and therefore needed some degree of customization. Other companies felt that they should customize the software to fit the way they conducted business rather than changing processes to fit the configuration workflow. Both are mistakes.
Even companies that have had fairly successful implementations, when they finally get around to doing the first upgrade, admit that many of those customizations were a mistake. They subsequently spent time and money to eliminate customizations they initially thought their company just had to have. Consider all these costs and savings, then compare with the competition, both internal and external, illustrating the savings (see figure form).
|
Business Lines/Domains
|
Domain 1
|
Domain 2
|
Domain 3
|
Domain 4
|
|
Total Security Solution Budget of your customer
|
|
|
|
|
|
Total IT Budget spent in-house by your customer
|
|
|
|
|
|
Total IT Budget for you in this domain
|
|
|
|
|
|
Total IT Budget of your competition
|
|
|
|
|
Figure 4 Sample worksheet form for comparing IT costs
The City Surveillance Project Case Study: your best TCO model
Imagine you are responsible for a safe city project, and you are tasked with deploying a multi-million-dollar video surveillance system. Where would you start? How would you evaluate solution proposals? How would you assess upfront costs in relation to the long-term operating costs? And which areas of the system should you focus on to optimize its total lifecycle cost?
These are just some of the questions you need to ask to minimize risk and avoid unpleasant surprises once the system is deployed.
The total cost of ownership for a hypothetical 1,500 camera system over a ten-year period amounts to approximately USD 17,000,000. The majority of the solution costs include total cost of acquisition: USD 11,400,000, or around 67%, together with the Total operating cost: USD 5,200,000, or around 31%.
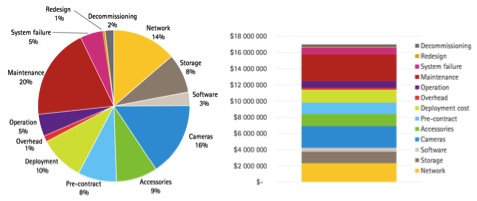
Figure 3 TCO Cost Distribution (Percentages) and Currency (USD)
Should the end user deploy a non-compliant or poor performing surveillance system there are significant security costs due to system downtime. Security costs that appear from downtime of a surveillance system are also not included in the above.
For example, in an airport, if the surveillance system fails, it could lead to very high costs as extra security guards may need to be dispatched, or flights might be delayed. In a retail store, a failed surveillance system may impact the ability to prosecute perpetrators for fraud and shrinkage, leading to substantial losses. In the city surveillance system, inoperative cameras could miss a critical event impacting public safety.
The surveillance industry is constantly innovating to improve product and image quality, optimize video compression, speed up installation, and simplify maintenance. With Zipstream, an award-winning compression technique that lowers bandwidth and storage requirements by an average 50% or more for many common 24/7 surveillance use cases, and an assumption of 25% savings on storage, the impact of Zipstream on the TCO amounts to approximately $450,000 of savings in total.
I've done my TCO analysis, now what?
Today’s powerful microcomputing platforms can run entire video management systems on a lower cost device that can be distributed and located closer to the cameras. IT departments currently do not consider these devices to be servers, requiring significant maintenance and lowering TCO. In a distributed platform video could be recorded without streaming continuously over a city-wide or corporate network. The result is improved quality for evidence and significant reduction on bandwidth, scalable cost savings.
What’s next and how do you stay ready with your plan to reduce TCO?
Ask questions. What is happening at your business that may increase costs or improve your processes?
Define targeted use cases by examining your key business problems. These are the things that cost your company the greatest; by taking ownership of a program to leverage your security plan and reduce these “time suckers,” you’re on the way to lower TCO.
Critical Infrastructure facilities require both physical and virtual perimeter protection. Reducing false alarm costs is one opportunity that comes up in conversation over and over. With the previously described Axis Communications Camera Applications Platform (ACAP), video analytic devices can work together and “confirm” alarms before transmission, decreasing the amount of work for security staff.
Cyber protection against intrusion and exploits is critical; DDoS attack prevention vital. With healthcare, it may be customer PII, retail, credit card data, etc. Help your team develop a sense of ownership with the employee, visitor and contractor community; potential predators will perceive your facility as a non-viable and non-vulnerable target and may move on.
Using early warning tools like gunshot detection, vocal aggression, social media and location-based solutions can potentially reduce the ultimate TCO: you might be shortening the time first responders need to save a life at your facility.