
Beyond the core functionalities of recording and displaying video, one of the most important capabilities of modern Video Management Software platforms is the ability to reduce bandwidth required for transmitting live video.
- By Brian Carle
- Feb 01, 2017
Financial institutions have been historically slow to adopt IP video surveillance citing concerns about possibly compromising network security.
- By Stephen Joseph
- Feb 01, 2017
Security threats are on the rise and as IT security teams increase their scrutiny of all network-connected devices, it’s time for some new thinking about the design and maintenance of building security systems.
- By John Szczygiel
- Feb 01, 2017

The abundance of networked solutions and devices—both security and nonsecurity— has exploded in recent years, providing unparalleled convenience and efficiency.
- By Ken LaMarca
- Feb 01, 2017
Physical identity access management (PIAM) solutions have changed the way leading organizations approach security.
- By Don Campbell
- Feb 01, 2017

Several routers, including those in the popular “Nighthawk” series, are affected.
Latest all-in-one NVR offers advanced embedded enterprise video management features for small and medium business users.

Now, the understanding of cloud technology and its value are clear, but safety often comes into question for security professionals.
- By Steven Turney
- Dec 07, 2016
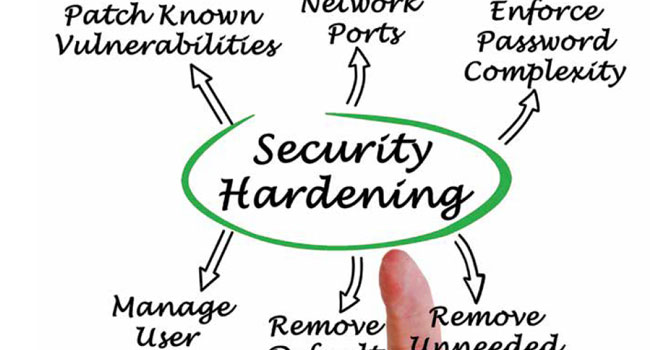
It is an understatement to say that IP networks have been a game changer for specifying, installing or managing video security and surveillance systems.
- By Bjørn Eilertsen
- Nov 01, 2016

Remember the Jurassic Age of organizational security? You built the stronghold, hardened the perimeter, established a set of rules and walked away. Security? Done.
- By Tom Gilheany
- Nov 01, 2016
As physical security technology continues to advance in both complexity and capability, it is increasingly bumping into and being influenced by other technology segments.
- By Dr. Cahit (Jay) Akin
- Nov 01, 2016

With cyber-attacks on the ascent, the need to strengthen the security posture and be responsive is top of mind for CIOs, CEOs and CISOs. Security is closely interlinked to all aspects of the business and has a direct bearing on business reputation, privacy and intellectual property
- By Shashi Kiran
- Nov 01, 2016
Manufacturing companies are placing increasing emphasis on data security throughout their operations to protect confidential data and to validate their systems are protected against unauthorized and unwanted changes.
- By John Stamos
- Nov 01, 2016
Megapixel technology has been a tremendously disruptive force in the security industry, as the superior image quality made possible by high-resolution imaging has led to increased capabilities and effectiveness of video surveillance.

Cloud environments give companies a cost-effective, easy-to-use data store solution. In fact, analysts predict that cloud spending will cross a $200 billion tipping point in 2016.
- By Paul Fletcher
- Oct 03, 2016

Network design is challenging, requiring designers to balance user performance expectations with network-resource costs, capacities, capabilities, and use scenarios.
- By Steve Surfaro
- Sep 06, 2016

Cloud environments give companies a cost-effective, easy-to-use data store solution. In fact, analysts predict that cloud spending will cross a $200 billion tipping point in 2016.
- By Paul Fletcher
- Sep 01, 2016

Today’s security leaders must present solutions to enterprise organizations that meet the needs of these diverse organizations.
- By Simon Morgan
- May 01, 2016

CEZ recently faced several challenges, including a large increase of IT devices to be monitored, pressure to increase work efficiency and reduce the number of employees at the same time.
- By Gábor Marosvári
- May 01, 2016
Cybersecurity isn’t the sexiest topic for presidential candidates right now, but controversial legislation, massive security breaches and increasing tension with China are keeping media attention on the issue.
- By Dwayne Melancon
- May 01, 2016