Sponsored
From Intelligence and Data to Dollars
Monetizing the Internet of Security Things
- By Steve Surfaro
- Jul 05, 2016
The largest device market in the world will no longer be smartphones, according to Gartner’s November 2015 study. In fact, by 2020, 28.1 billion devices, will offer connectivity and data, from smartphones and vehicles to embedded microcomputers and security devices according to an IDC forecast.� This is the Internet of Things.
Of the projected 14 billion devices in use by 2020, cross-industry and vertical market-specific devices for enterprise and small/mid-sized business are expected to grow to 35% and can no longer be considered only for use by consumers. The interesting fact is that business users often consume data from IoT devices using similar processes as their consumer counterparts. For example, the growth of “Fog” and “Mobile Edge” Computing (MEC) models can boost performance for both multimedia delivery of consumer streaming video services, as well as low latency tactical video for public safety and first responders. Both use cases leverage Digital Multimedia Content (DMC) available in networks and storage closer and capable of a shorter delivery time to smartphones and other consuming devices. One version entertains, while the other potentially delivers life-saving situation awareness.
Digital Multimedia Content and IoT
This Digital Multimedia Content delivered to IoT devices like laptops, workstations and smartphones and produced by IoT devices like IP video surveillance cameras is defined as including the video content itself, plus associated metadata (feature data) and audio. The storage location or device (i.e., network video record, server, or virtual [Cloud, Fog or MEC] storage) where digital video, digital multimedia content, or digital multimedia evidence (DME) is originally stored is significant in achieving Video QoS or the ability to acquire, render, search, disseminate, distribute DMC.
DMC may also be referred to as IP or digital video, IP video content, or Digital Multimedia Evidence (DME). Digital data representing audio content, video content, metadata information, location‑based information, relevant IP addresses, recording time, system time, and any other information attached to a digital file. DMC may be compressed or uncompressed and may also be referred to as original, copied, local, or virtual. How this data is analyzed, processed, stored and delivered efficiently, often to public safety is a significant monetization opportunity.
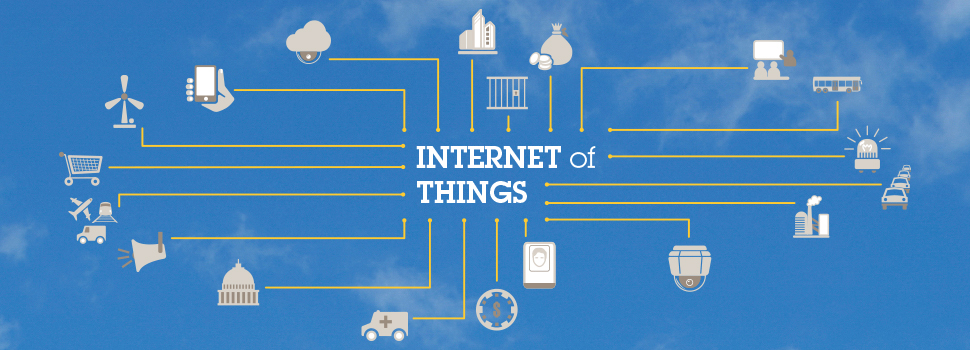
The basic framework of what defines IoT devices, includes business assets, sensors, industry devices (things) connected to each other, to humans or systems, processing data input, applying rules and models, and finally analyzing and streaming content.
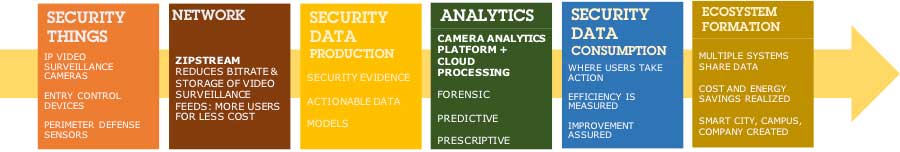
Figure 1 The Internet of Security Things
In the above figure, an “intelligent” video surveillance device streams DMC efficiently using the advanced video CODEC Zipstream, producing forensic video evidence, which is then analyzed, consumed by users, measured to create a security “model” or scenario and ultimately working seamlessly with other systems, reducing costs. In each step, the systems integrator or end user is able to offer products and services to reduce costs, improve safety and remove “silos” preventing data from benefiting other systems.
Analytics and the Internet of Security Things
Let’s look at the IoT analytics step and discover even greater monetization opportunities. Analytics is a fast growing market with IoT as the use of data creates measurable benefits. All too often, analytics of security data implies forensics or after an event occurs. This is only part of the great benefit associated with using the entire Security Data Analytics Cycle, shown below.
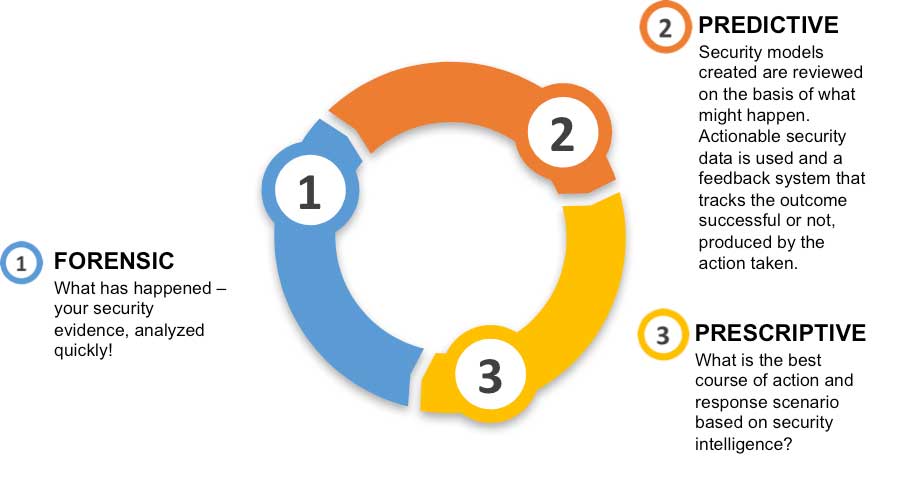
Figure 2 Security Data Analytics Cycle
This Security Data Analytics Cycle, when related to actual solutions illustrate a significant amount of applications that can run as an embedded process inside a qualified camera. These processes or “agents” may be paired together with a more scalable analytics solutions running as a service or cloud-based application. The innoVi solution from Agent Vi is an example of such a solution, offering systems integrators to install an AXIS camera running an embedded process that delivers actionable data to a cloud service that may be used by central monitoring stations to detect breaches and reduce false alarms. This unified solution is itself monetized as it represents significant cost savings through loss prevention, improved process and potential insurance premium reductions. A suite of potential Security Video Analytic Application Categories and Examples are pictured below:
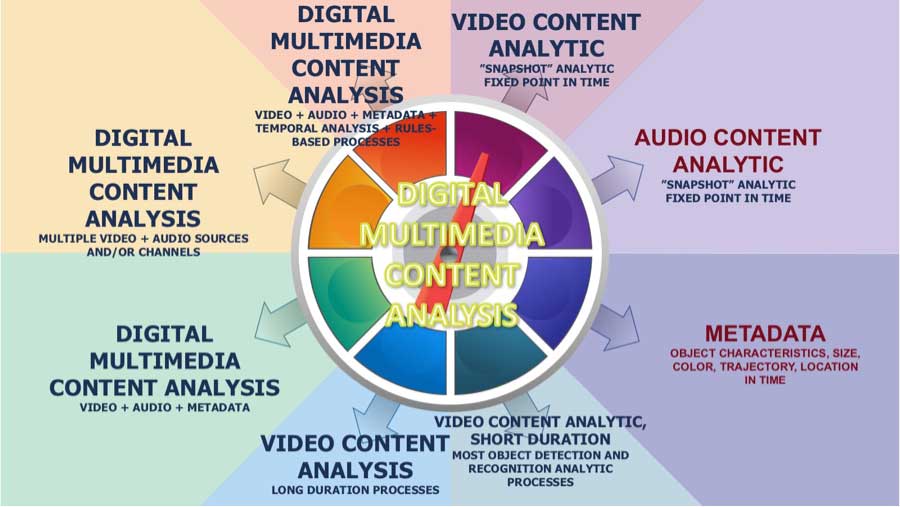
Figure 3 Security Video Analytic Application Categories
Data and usage analysis leads to numerous monetization opportunities for OEMs, as vendors can supply customized offerings with software-enabled features on demand. Some of these features are in the application examples below:
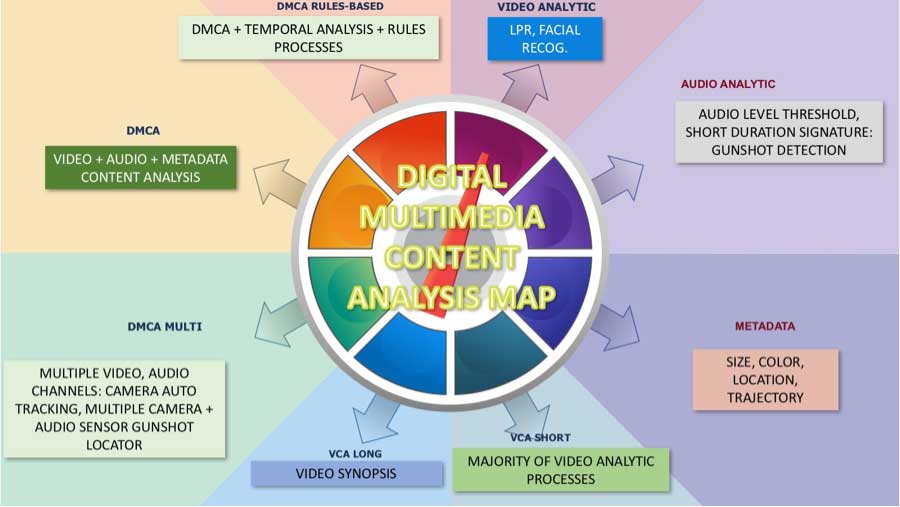
Figure 4 Security Video Analytic Application Examples
Public Safety IoT in action!
Let’s look at the Internet of “Security” Things in action. A team of law enforcement professionals just received intelligence of gang operations nearby, where illegal narcotics and weapons are being stored and sold. Two members of the city’s gang violence reduction unit start a tour and soon receive a “hit” off a fixed surveillance camera with a built-in license plate recognition (LPR) application and connected to the NCIC�.
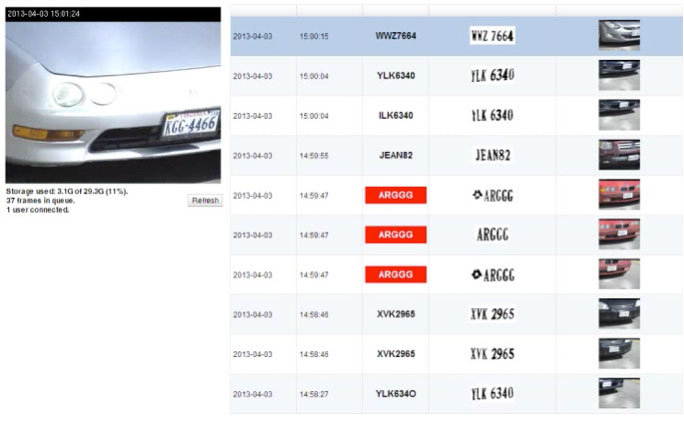
Figure 5 Vehicle License Plate Capture (Image courtesy IPConfigure)
The AXIS detecting camera has an embedded application running on its analytics platform and a nearby microcomputer, such as a Razberi Pi running a fully featured video management system called Orchid Fusion� connected to a NAS (network attached storage).
A “hot list” was recently uploaded to the NAS device after the city’s crime analysis software related the vehicle registration of a known gang associate to the primary suspects.
A “beacon” application notifies the team nearby, as well as the Command Center of the alert. The camera is equipped with a “next generation” codec called Zipstream� that reduces the bitrate required for streaming video, so a clip of the vehicle passing by the camera is pushed to law enforcement on site. The camera is capable of rendering details through forensic capture, an image processing feature of the AXIS camera, and the team sees the vehicle occupants are armed with automatic weapons.
Knowing the location of their law enforcement assets, Command automatically pushed out notifications of the filtered social media chatter to the nearby detectives and tactical response team. The cloud-based social media app has been listening for known gang language, keywords and locations, focusing the intelligence to just what is most vital in this operation.
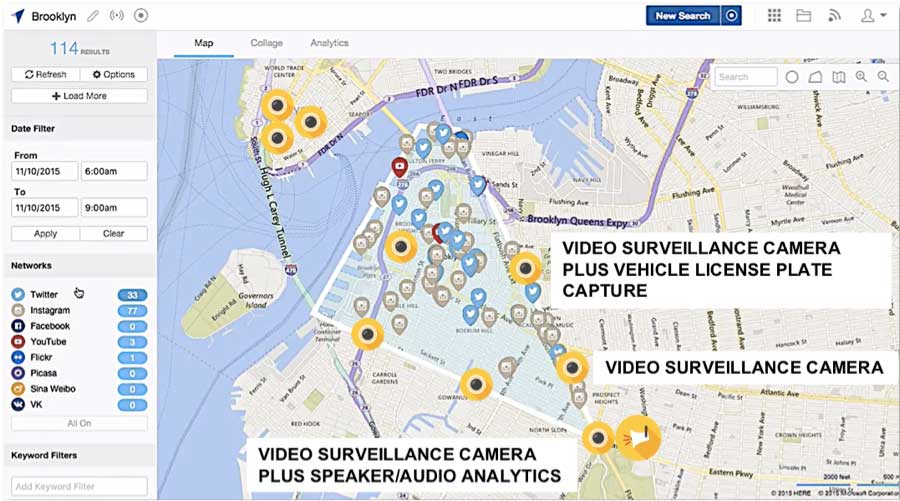
Figure 6 Social Media Alerts and Video Surveillance Assets (Image courtesy Geofeedia)
A warrant is obtained and the unit leader requests the “go-ahead” for the operation from Command. A traffic management application creates a protective radius around the site operation, re-directing traffic safely around the operation’s area and dispatching EMS for potential injuries and HAZMAT should there be toxic drug production onsite. The team executes the warrant and takes key gang members into custody.
This scenario is not only possible with a running IoT ecosystem, it represents a ubiquitous development of social and technology fusion. What really makes this work? An even better question is, can this scale, or can hundreds of these scenarios be running simultaneously and continuously in many locations? The Internet of Things links sensors like advanced IP cameras, together with communications, storage, infrastructure, analytics and quality of service. With the Internet of Security Things, today’s systems integrators can close the loop on edge devices, data processing, transmission, dispatch of first responders and mining of the event’s intelligence for even faster response in the future.
Tactical IoT profiles may be identified and potential response scenarios generated, with the most confident automation by analytical processes performed repeatedly. First responders become safer through intelligence; families stay informed and involved.
The Cyber IoT factor
 Cyber hardening is another monetization opportunity. Energy management solutions, process control and industrial machines perform high risk operations and have a high level of embedded intelligence for visualization. There is a great need to protect such solutions and secure the associated intellectual property from theft or manipulation. The large number of connected sensors also create a huge amount of big data which also needs to be protected. The cyber framework for defining and protecting IoT devices is shown below and in this figure:
Cyber hardening is another monetization opportunity. Energy management solutions, process control and industrial machines perform high risk operations and have a high level of embedded intelligence for visualization. There is a great need to protect such solutions and secure the associated intellectual property from theft or manipulation. The large number of connected sensors also create a huge amount of big data which also needs to be protected. The cyber framework for defining and protecting IoT devices is shown below and in this figure:
The situational awareness of IoT industrial Applications and Devices as requiring three capabilities:
- DETECT, the ability to know what IoT devices and components are connected to a given network or system
- AUTHENTICATE, the ability to verify the provenance of IoT components and prevent and detect spoofing
- UPDATE, IoT security programs must include the ability to securely maintain and upgrade these components
Monetization options also can be found in condition data monitoring of IoT devices which ultimately leads to predictive maintenance services. End users benefit from improved availability of their applications and a reduction in total cost of ownership. Software license management and version compatibility are another opportunity to build recurring revenue and reduce potential costs for end users due to incompatible systems.
Safe and Smart Cities
Globally, more people live in urban areas than in rural areas, with 54 per cent of the world’s population residing in urban areas (2014 data). The number of megacities has nearly tripled since 1990 and by 2030, 41 urban “super-regions” are projected to house at least 10 million inhabitants each. Urbanization places extraordinary stress on both environmental resources and physical security. Resilience and operations management are necessary to keep pace with this growth.
In potential answer to the urbanization trend, the birth and evolution of the smart city has contributed to reduce security investigations, increase energy management, increase parking resource efficiency and improve traffic safety. The following framework can be applied to campuses and corporations as well:

Figure 8 Smart City Security Framework
The monetization of Security Device IoT extends into a rapidly growing market, smart lighting. There is great potential in unifying an intelligent IP Camera and various sensors on a lighting solution. LED lighting upgrades often lead to impressive energy savings, often measured in hundreds of thousands of dollars per year for cities and corporations. In addition, vehicle and pedestrian traffic flow outside and inside buildings may be analyzed.
The move towards smarter urban management does not happen without the deployment and measurement of the solution opportunities. With urbanization rates potentially reaching 70% by 2050 in rapidly growing regions like the Middle East, these solutions are essential. Applicable to virtually any global urban area, problems such as traffic congestion and increased energy use can be eased with the following goals in the figure.

Figure 9 Safe and Smart City/Corporate Goals
The opportunities for monetization in the Internet of Security Things is great for all ecosystem members. However, deployment abilities may not be readily available, requiring collaboration and project management. For the city or corporation using IoT, becoming safe and smart is a journey, not a destination.