IoT Cybersecurity Pillars – Four Core Tenets of Any IoT Security Program
Understanding an Internet of Things security program takes careful consideration and study. We are pleased to bring you this first online post; others will follow each week, discussing the four core tenets. This is Part 1. The remainder will follow weekly.
- By Will Knehr
- Mar 10, 2023
The world has seen a significant increase in cyber-attacks aimed at critical infrastructure and security products in the last few years, with Industrial Internet of Things (IIoT) devices such as security cameras, becoming prime targets for hackers. According to a Kaspersky analysis of its telemetry from honeypots shared with Threatpost, last year alone, there were more than 3 billion IoT breaches, and that is just the recorded number, the actual number is probably much higher.
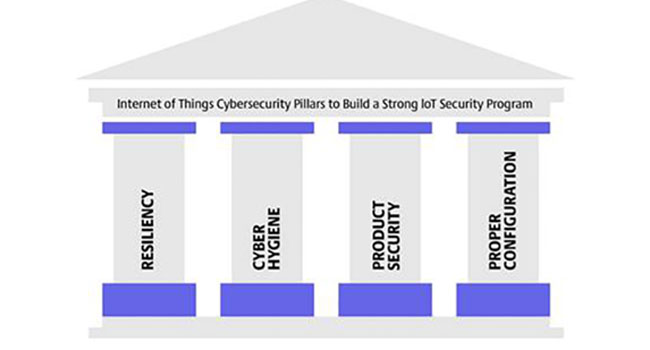
It is clear that IoT and IIoT manufacturers must do more to help secure these devices and educate the market on security best practices. To that end, I would like to share my “Internet of Things Cybersecurity Pillars” to help educate everyone on IoT Security. The pillars focus on what we believe are the four core tenants that should be the foundation of any IoT security program. The four pillars are resiliency, cyber hygiene, product security, and proper configuration.
In this article, we will briefly explore each of these pillars. I hope that you will join me on this journey and together we can work to make IIoT safer for everyone.
What is IoT and IIoT?
Since we will be using these terms a lot throughout these articles, it is probably best to go ahead and make sure that we are all on the same page. IoT is the Internet of Things, and is defined as small computing devices, sensors, or software that communicate and exchange data over the internet.
Still confused? No problem, you interact with these devices every day and maybe do not even realize it. These are devices like smart refrigerators, vacuums, dryers, thermostats, home security systems, wearable fitness and wellness tracking, light switches, and even healthcare devices like pacemakers.
Unfortunately, most of these devices were not made with security in mind, they were just made to function and provide convenience to the consumer. IIoT is just like IoT but developed for an industrial market. IIoT includes devices used in manufacturing, heating and cooling of commercial facilities, smart fire control systems, commercial security systems, and smart farm devices. These devices automate many commercial processes, which increase efficiency and often help to reduce costs, but they have also introduced a new set of vulnerabilities to organizations. To alleviate any confusion, for the rest of the article we will use the terms IoT and IIoT interchangeably.
Without any further ado, let us jump into the first two pillars in detail and see what we can do as a team to make our IoT devices better.
Resiliency
Resiliency refers to our ability to withstand, recover from, and prepare for potential issues in our environments. Simply put, will your devices be there when you need them the most? Will your security system work when the power goes out? Will your cameras survive high winds and severe storms? How quickly can you bring manufacturing or services back online in the event of a cyber-attack? These questions will help you determine your organization’s resiliency.
Today’s organizations rely on Industrial Internet of Things (IIoT) devices to control power, security, fire suppression, Heating Ventilation and Air Conditioning (HVAC), manufacturing, and much more. Our businesses, our security, and sometimes even our lives rely on these devices to function properly. As security professionals, we must make sure that we build resiliency and redundancy into these systems, and in the networks that surround them.
One of the ways that we can help build resiliency into our systems is to imagine the worst-case scenarios and tabletop those scenarios. What is a tabletop exercise? A tabletop exercise is where an organization gathers its key stakeholders and imagines something terrible like a severe weather condition (hurricane, tornado, and floods), loss of power, loss of communication, or cyber-attack.
For example, a tabletop exercise might include key stakeholders from IT, HR, Sales, Finance/Accounting, Engineering, Development, Customer Service, and Operations department – all sitting at one table. Then we ask those stakeholders to tell us what happens to their customers, employees, equipment, etc. in the event of a catastrophe. Doing these, tabletop exercises frequently, will help your organization identify gaps in resiliency.
Some of the actions that you can take to make your organization’s IIoT devices more resilient are:
Build or Purchase Devices with Strong Protection
a. Purchase devices from companies that do vulnerability testing and fix issues in devices. Many IoT/IIoT devices are developed quickly and cheaply, so consider how long the company has been around and what their reputation is for maintaining their products after they have been released
b. Look for IIoT devices that use encryption to protect data in transit and data that is stored on the device
c. Devices should support secure protocols and standards like 802.1x integration
Build Secure Network Topologies to Protect the Devices
d. IIoT devices should be carefully controlled through physical, technical and administrative controls set by an organization. NIST is a great free resource to help get you started
e. IIoT devices should never be publicly accessible and should be properly segmented to ensure that they are protected from hackers
Purchase Devices that are made to Withstand Your Unique Conditions (salt, high winds, dust, explosion proof, lightening, high temperature)
f. Take weather and atmospheric conditions into consideration when purchasing IIoT devices and be sure the device is rated or tested to withstand your unique conditions. For example, if deploying a device to coastal Florida, you may want something rated for salt exposure, high winds, and lightening
Backup Device Configuration Data
g. Having backups can ensure that if a device breaks or becomes corrupted that you can easily restore it or bring in another device
Consider Redundant Devices with Secure Failover
h. Redundant devices provide backups in case a device fails for whatever reason
i. Failover refers to what the system does when a device fails. By using failover systems, the function that the IIoT provides will continue to work while the failed device is being replaced or fixed. For example, what happens to your electromagnetic lock when the power fails? Does the door remain locked, or will it unlock?
Consider Battery Backups or Generators
j. Devices that supply critical functions should at minimum have an uninterruptable power supply (UPS) to help protect against short power outages
k. Generators may also be a good idea if the device needs to continue to function during a prolonged power outage
In summary, building resilience in IoT/IIoT requires a partnership between the manufacturer of the device, the physical security expert at the organization, and the cybersecurity expert. Manufacturers are responsible for producing quality products that meet security standards. They must be willing to update their products in a timely fashion when vulnerabilities.
Physical security experts must ensure devices are adequately installed and protected. Cybersecurity folks must make sure the devices have the proper technical controls in place to protect from cyber-attacks.
When most people think about hygiene, they think about taking showers or brushing their teeth, the things that we do to keep ourselves clean to prevent diseases or other illnesses. Cyber hygiene is a similar concept but applied to computers, networks, and security. It is the things we do on a routine basis to help protect our networks from attackers.