
The department announced the sanctions Friday after it said that North Korean intelligence groups targeted American critical infrastructure, particularly the financial system.
- By Haley Samsel
- Sep 17, 2019

Lawmakers are working to find a solution that will help counter ransomware attacks, which are affecting school districts and municipal governments.
- By Sherelle Black
- Sep 13, 2019

Google is working to keep unwanted and malicious content from its users.
- By Sherelle Black
- Sep 11, 2019

Security management systems for businesses large and small were the talk of GSX exhibitors.
- By Haley Samsel
- Sep 10, 2019

Phishing scams continues to be a widespread problem for businesses and individuals alike. But there are several ways to recognize that you could be getting scammed.
- By Susan Alexandra
- Sep 09, 2019

A database that was left without password protection was discovered by a security researcher, who said 419 million records of Facebook user phone numbers were exposed.
- By Haley Samsel
- Sep 06, 2019

Information mishandling, snooping and location tracking are often the ways in which users find their privacy violated online.
- By Susan Alexandra
- Sep 03, 2019

Facing criticism over low voter turnout and barriers to caucusing, party officials planned for remote caucuses in 2020. But the national Democratic Party said the methods would expose the process to high cybersecurity risks.
- By Haley Samsel
- Sep 03, 2019

The number and breadth of devices that make up the Internet of Things (IoT) continues to grow rapidly, with everything from kitchen appliances to video surveillance and access control systems offering the ability to connect to a network.
- By Ryan Zatolokin
- Sep 01, 2019

We know by now that there is an abundance of business advantages in the cloud — it’s agile and cost-efficient, and, with little to no hardware maintenance, it’s easier to update and perform maintenance on than traditional on-site servers.

Do you want the real bottom line in providing cloud services for video, access control and other integrated services?
- By Martin Renkis
- Sep 01, 2019

Security professionals face many challenges in selecting video surveillance systems that address their unique needs.
- By Jeff Whitney
- Sep 01, 2019
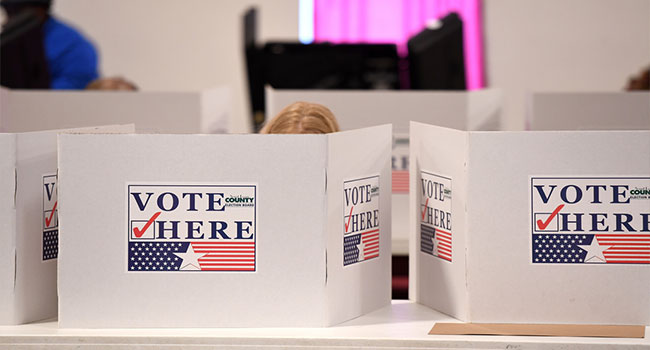
The Department of Homeland Security is preparing to launch an education program on the potential of ransomware attacks targeting voter databases, some of which were compromised by Russian hackers in 2016.
- By Haley Samsel
- Aug 30, 2019

A ProPublica investigation found that the decision by insurers to pay hackers instead of encouraging victims to recover files by themselves is helping fuel a surge in ransomware.
- By Haley Samsel
- Aug 28, 2019

The leader of the Cybersecurity and Infrastructure Agency, which works within DHS, is concerned primarily with risk management, Chinese threats to supply chains and election security.
- By Haley Samsel
- Aug 27, 2019

Two Nigerian citizens are accused of leading a massive fraud scheme that transferred at least $6 million in fraudulently-obtained funds, much of whom was taken from elderly people.
- By Haley Samsel
- Aug 26, 2019

The impact of GDPR, the increasing number of issues with shadow IT and the more advanced solutions for IoT devices are among the most surprising trends.
- By Michael Volkmann
- Aug 23, 2019

A new report predicts a new frontier of cyber attacks for healthcare organizations, including ransomware, international espionage and the hacking of biomedical devices.
- By Haley Samsel
- Aug 22, 2019

Only eight breaches were responsible for the exposure of 3.2 billion records in the first half of the year, according to new research.
- By Haley Samsel
- Aug 22, 2019

The state suspects that the attack, which took place Friday morning and targeted small local governments, was coordinated by “one single threat actor.”
- By Haley Samsel
- Aug 20, 2019