
Security Operations shifts security to the left to ensure that security is met at every level, making it both a necessity and a challenge.
- By Gilad David Maayan
- Aug 06, 2019
A special word of caution needs to be emphasized when changing over to mobile systems. Many legacy access control systems require the use of backend portal accounts.
- By Scott Lindley
- Aug 01, 2019
For many companies, deploying security information and event monitoring (SIEM) technology to strengthen the ability to identify potential security threats has been an unreachable goal.
- By Mike Sprunger
- Aug 01, 2019
The shipping industry is being tasked to improve productivity, increase speed of operations and mitigate risk from new and potentially devastating forms of attack from both external and internal potential threats.
- By Aluisio Figueiredo
- Aug 01, 2019

Cybersecurity and physical security no longer exist in two different worlds. Each now supports and depends on the other as part of a comprehensive risk and liability management program.
- By Greg Schreiber
- Aug 01, 2019

There are a number of common misconceptions about endpoint security.
- By Jerry Young
- Apr 29, 2019

Learn about the key factors to pay attention to when selecting a provider of network vulnerability assessment services.

Back when IT was dominated by on-premises data centers, storage options were fairly straightforward and securing storage resources was relatively simple compared with today’s far more complex storage landscape.
- By Richard Diver
- Mar 01, 2019

As key stakeholders look to implement AI into their workflow, many find that security and safety is a commonsense place to begin.
- By Brent Boekestein
- Mar 01, 2019

From simple photo IDs of the past to 2D barcodes and the now ubiquitous use of video cameras, businesses, schools and venues are constantly looking for better ways to protect people and property.
- By Denis Petrov
- Mar 01, 2019

Millions of video surveillance cameras around the world are losing money.
- By Scott Seraboff
- Mar 01, 2019

The Internet of Things (IoT) promises greater connectivity, which, when properly leveraged, can provide invaluable insight into our organizations and our operational environments. In the security sector, increased connectivity between sensors and systems gives us access to more data than we thought possible even just a few years ago.
- By Jimmy Palatsoukas
- Feb 01, 2019
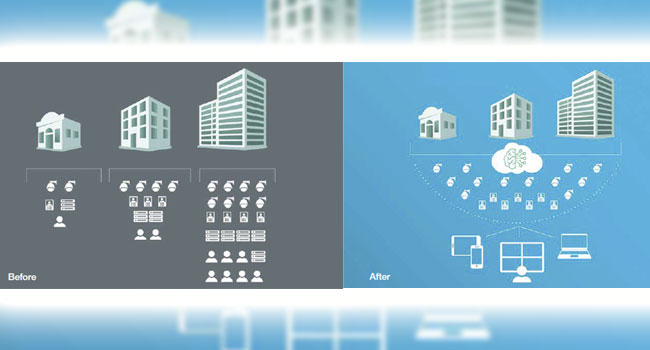
There’s enormous opportunity for all enterprises in the cloud, and those in the middle market are taking note.
- By Andreas Pettersson
- Feb 01, 2019

Smart city initiatives are growing across the globe, as leaders look to increase security and intelligence across metropolitan environments.
- By Brandon Reich
- Dec 01, 2018
Hardware Security Modules, or HSMs, protect against insider and external threats by delivering confidentiality for encryption keys in a physically hardened appliance.
- By Anand Kashyap
- Dec 01, 2018
Technological advancements are resulting in trends and movements that improve the quality of life and business.
- By Abhishek Iyer
- Dec 01, 2018
No one will argue that the network has been one of the greatest evolutions in time. Think of it, everything that you used to do by hand, you can now do via computer. Well, almost everything.
- By Ralph C. Jensen
- Dec 01, 2018

Video surveillance has dramatically changed in recent decades. Open, IP-based network technology has largely replaced the closed, proprietary world that long dominated the security industry.
- By Jeff Whitney
- Dec 01, 2018

Security firm Armis has discovered two vulnerabilities in Bluetooth Chips from several networking industry leaders.
- By Sydny Shepard
- Nov 05, 2018
Cloud technologies are giving people access through their mobile phones and other devices to a variety of new experiences, while making their workplaces smarter and more data-driven.
- By Hilding Arrehed
- Oct 01, 2018