
Think Outside the Door
There's more to security RFID than going through doors
- By Bill Nuffer, Leon Chlimper
- Feb 02, 2010
When you think RFID in security, you automatically think access control. Access control badges are ubiquitous in enterprise environments for use at entrances and exits in virtually all industries. But there is more to RFID in security applications than going through doors.
In fact, if you think outside the door, you'll find a host of RFID applications technologies.
What is RFID?
RFID is any technology that uses radio frequencies for the purposes of identifying, in some manner, a person or thing. It is the ways in which people or things are identified. The reasons for identifying them are innumerable and are what makes RFID far more useful than you might realize.
RFID was first used in World War II as a spin-off technology from radar to identify friends or foe. The technology is still used today in both civilian and military aircraft, virtually unchanged from WWII days.
RFID took a huge leap into commercial viability for use in security after the semiconductor revolution of the 1950s brought the cost of semiconductors dramatically down by the 1980s. This price drop made it possible to build a costeffective RFID credential, which became known as proximity.
RFID Goes Primetime
In the 1990s, two major RFID technology revolutions had a direct impact on the security industry. The first of these was smart cards. The use of smart cards for things like fare collections in public transit spilled over into security. Cryptography capabilities enabled more secure cards, and the ability to provide additional data storage on cards—like biometric templates and pin codes—further increased the cards' security.
For example, the most advanced application of smart-card technology is the federal government credential, PIV-II. Approved in February 2005, the personal identity verification system directive requires that smart cards be issued by all federal government employees and contractors who require access to federal facilities and information systems. The overall goal of the PIV directive is to create a common government-wide identification system to enhance security, increase government efficiency, reduce identity fraud and protect personal privacy.
The PIV card is the primary component of the system and uses cryptographic and biometric technologies to support graduated levels of security for various agencies' applications. Each card holds a PIN that is used to authenticate the cardholder. Further, the card has a cardholder unique identifier that identifies the person within the PIV system. Two electronic fingerprints are securely stored and protected on integrated circuit ships. Lastly, public key infrastructure- based cryptography is used to protect the integrity of the information stored on the card.
The PIV-II credential further details the requirements of the program and identifies the components and processes that will support a smart-card-based platform. Those components and processes call for an operations system with three subsystems:
- PIV front-end subsystem—the PIV card and card readers, biometric readers PIN input devices
- The PIV card issuance and management subsystem—the name for components used for identity-proofing and registration, card and key issuance and management, and repositories services like the PKI directory
- Access control subsystem—physical and logical access control systems, the protected resources and the authorization data
Lastly, PIV-II specifies a means to collect, store and maintain information and documentation needed to authenticate and ensure a person's identity.
For PIV-II to be effectively implemented, RFID technology is a requirement for virtually every component and subsystem used to maintain the safety and security of federal assets, including infrastructure, physical assets, data and personnel.
The second revolution in RFID technology is its use in logistics and supply-chain applications. The MIT Auto-ID Center was created to develop the Electronic Product Code, a global RFID-based item identification standard. This has given birth to the availability of low-cost identification of goods and materials in supply chain and logistics applications.
Since 2004, retailers like Target have been looking to use ePC passive tags on products with the goal of moving "from smart containers to smart cargo in smart containers," said Caroline Landwehr, former global security strategies manager for the Minneapolis-based retailer.
RFID allows for non-intrusive inspection of containers, rather than physical inspections that require the unloading of goods. This offers an average of 70 percent savings in inspection costs. Further, RFID use in supply chains helps to meet customs requirements, like the U.S. Customs rule that an electronic manifest is provided to them 24 hours prior to any ship arriving in the United States from a foreign port. The potential for reduction in, recovery of or prosecution for theft is greater, as discrepancies in product counts can be identified more quickly at each stop.
Additional supply chain and asset management uses have been made possible by advancements like:
- Great reductions in costs. Tags can cost as little as $0.20 when purchased in bulk.
- Woven antenna technologies, which can be used in textiles, turning uniforms into "personnel asset trackers" that enable hands-free monitoring of the activity of critical personnel in lab environments, mining industries, hospitals, etc.
- Fast reads and anti-collision advancements, which are used in applications like tracking fast-moving vehicles and, on the other end of the spectrum, pharmaceutical bottles.
- Long ranges—up to 8 meters depending on frequency
Real-World Applications
Making real-world application choices for RFID requires thinking outside the door, not only to maximize your access control but to ensure you are not missing key opportunities to secure staff or assets and to costeffectively reduce loss and liability and mitigate risk.
New advances in RFID provide enterprise and government solutions that are becoming more necessary in this changing economy.
- A major systems company has made numerous acquisitions of other major companies in the sector. Each company had its own enterprise security system and system of credentials.
- A government contractor is faced with the provision of PIV-II credentials under the mandate of HSDP-12. But the mandate for these expensive credentials only applies to the 10 percent of staff with government facility access.
Some of today's RFID vendors offer readers that can read multi-frequency, multi-modulation and multi-protocol cards, such as mifare, ISOI5693, HID, Indala, deister, PIV-II, 125 kHz and 13.56 MHz smart cards. This provides enterprise companies freedom from proprietary card and reader technologies, allowing integration of virtually any multiple credential enterprise. In the case of the systems company, replacement with one of these readers allowed for the quick integration of new staff into all PACS systems without the costly and debilitating mass replacement of cards. For the PIV-II solutions, the firm was able to retain existing credentials for the majority of its staff and upgrade to government requirements while maintaining existing PACS systems.
Considering the number of company laptops, handheld devices and other high-value items walking into and out of an office daily, by tagging assets, a company can prevent theft, track keys and know the comings and goings of assets intended to leave and return. The advancement of RFID technology and reduction in costs makes tracking these assets affordable. In addition, RFID advancements now include omni-directional tracking over long distances, audible alarms at access points, hidden asset detection messages that are sent out if the tag is manipulated by metallic shielding, easy installation and more.
Like others around the world, the prison system in the United Kingdom requires a complete rekeying of facilities if any key becomes compromised. An innocuous mistake can result in huge costs in both time and money. The use of RFID asset tagging allows individual prisons in the system to scan all staff prior to departure for unintentionally retained keys. This results in a total annual savings of £30,000 (approximately $50,000) per prison in the system.
Today's RFID products can provide automatic vehicle identification to track vehicle assets and cargo. Further, these products can be used for driver identifi- cation in applications like parking management.
In one such long-range application, a heavy materials company tried manual clipboards and advanced license plate reading technology to track trucks as they passed through weight scales. RFID microwave tags and readers were ultimately chosen as the solution to provide fast, accurate weighing and accountability.
Looking Ahead
In the real world, keys are still used. Not every door is controlled by smart cards and readers for many reasons—one of the most prevalent is cost. But using RFID to amp up the effectiveness of key management systems creates new possibilities.
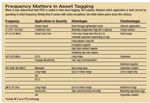
When it was determined that RFID was useful in item-level tagging, the industry debated which application is best served by operating in what frequency. Noting that it comes with many exceptions, the table below pares down the choices. Click to enlarge.
New key management systems are being developed that fulfill three key traits that make investment in these systems deliver an effective ROI: scalability, open-interface options and robustness. This combination ensures the system's longevity; as the enterprise grows, a scalable system will grow with it. Open-interface software allows for easy integration no matter the changes over time to the enterprise's other software systems. And, of course, physical robustness ensures the product will stand up to use, abuse and the elements.
But why not just use a key to access a lockbox full of keys? There are dozens of reasons in application.
For example, the European Organization for Nuclear Research in Geneva must ensure that its thousands of scientists— including the world's leading physicists—are out of range of the organization's $4.4 billion particle accelerator. Standing inside the particle accelerator enclosure during experiments would be deadly.
Inner regions of the LHC are secured by the combination of badge access and keys using an RFID-secured key-management system. To obtain a key, a CERN scientist must badge in to the system and remove his or her designated and tagged key, which allows access to the tunnel. This way, the system knows by electronic means who is in the tunnel at any given time.
The system also performs a far more critical function: it knows who is out of the tunnel at any given time. In less life-threatening situations, effective key management systems using RFID can not only track key activity, but can track other data, like the mileage on a vehicle at check-out and return.
In one such situation, a major automobile manufacturer has to control test track vehicles and secure the highly vulnerable IP that results from testing. This company uses an RFID key management system to perform control functions and secure the IP. They secure, control and gather data on both vehicle keys and laptop test beds. Lost keys have been reduced by 70 percent. Test start times have now increased from 20 to 80 percent on schedule due to the rapid and secure access of test bed data platforms.
Maximizing the Use of RFID
Thinking outside the box isn't only your job as a security professional. Look for product vendors and distributors who can best assist you by offering a wide range of RFID that includes asset control, smartcard readers and products operating in various areas of the spectrum.