Deadly Response
Early detection and remote response might have de-escalated police incident at Texas car dealership
- By Katie Merluzzi
- Dec 01, 2015
Recently, a police officer shot and killed
a man who smashed his car into the
Classic Buick GMC auto dealership
in Arlington, Texas.
Car dealerships present a complex
security challenge because they stock high-end models
for the public to see, placing high-value assets out
in the open where theft and damage can occur. For security
professionals, one thing is clear from this tragedy—
security cameras and monitoring might detect,
but can’t prevent a crime from taking place.
Auto dealership owners must strike the right balance
between serving customers and operational costs
associated with protecting their assets, property and
business. On-site security guards may seem like an effective
option, but the added costs of paying salaries,
benefits and providing the necessary equipment to effectively
respond can add up quickly. Furthermore,
human error, constant monitoring and personnel risk
add to the cost of this approach.
In the case of the Arlington dealership, they relied
on surveillance cameras monitored remotely by
a security company. It appears the trigger for the security
monitoring was not at the perimeter, so when
the suspect drove his car through the showroom glass
window, no doubt setting off motion detectors, it was
too late. Significant damage and a crime had already
occurred—with a tragic outcome.
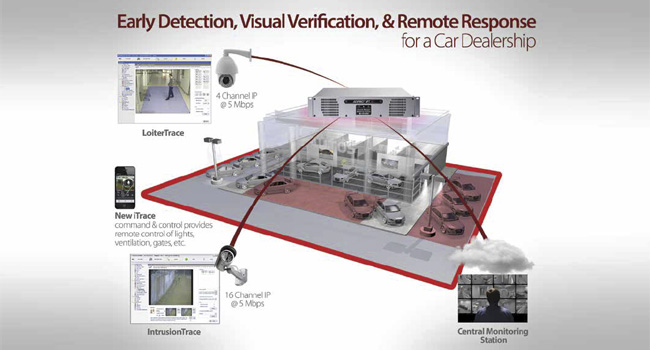
Car dealerships need a solution for perimeter
protection to provide early and reliable detection at
the edge of a property with innovative intrusion detection
technology. Using few security cameras and
advanced video content analytics (VCA) running on
a Remotely Managed Multi-service Gateway (RMG)
will accurately detect and alarm for perimeter intrusion
threats with great reliability to allow for preventative
action. This type of detection solution is a true
electronic first responder; with audio talk-down from
a remote location many threats can be eliminated before
they escalate. In extreme circumstances, like that
at the car dealership, these solutions can also assist
police and first responders with real-time visual situational
intelligence.
Protecting car dealerships is complex as the system
has to be immune to false alarms associated with
swaying vegetation, flags, clouds, animals, insects and
more. Car dealerships should look for intrusion solutions
that deliver the highest rate of detection combined
with the lowest rate of false alarms.
In addition to a perimeter protection, car dealerships
should consider video analytics to detect unauthorized
loitering in a protected zone. In the case of
Arlington, prior to the intrusion alarm, the security
monitoring company could have received a loitering alarm as the suspect approached
or entered certain areas of the car lot
and building.
Early detection isn’t enough. Once
the intruder has been detected by intrusion
detection technology, reliable
transmission of the alarm and visual
verification is imperative to establish
the threat, evaluate the situation and
deliver the appropriate response.
The first responders in this incident
were dispatched to a developing situation
where they relied on the information
verbally given to them by the security
company. They didn’t know if the
suspect was armed or had accomplices,
and did not have any remote visual
verification capability that could assist
with an effective response. A tragic loss
of life was the result.
A leading security company and
central monitoring station that protects
many car dealerships throughout
the United States uses a system that
provides early detection, visual verification
and remote response. This type of
system enables operators to act as soon
as a potential threat is detected. Each
operator can support multiple dealerships,
because they don’t need to constantly
view surveillance cameras waiting
for a threat event to occur.
They use alarms that direct them to
the appropriate site and camera viewing
the scene. The operators can visually
verify the threat and remotely warn
off the intruder with audio talk-back.
Potential intruders can be notified in real-
time that they are being watched and
that the police have been informed and
are en route. In the majority of cases,
the intruders leave the premises upon
hearing the audio warning—preventing
the crime from ever taking place. In the
case of the car dealership tragedy, the
security company could have de-escalated
the threat and avoided the altercation
between the suspect and police.
Another aspect to consider is the
benefit of remote monitoring and situational
awareness. Car dealerships should
look for providers that have applications
for smartphones and tablets to monitor
and manage a site from anywhere in the
world. These tools could have been additional
“eyes” into the situation developing
at the car dealership, providing first
responders better situational awareness
prior to taking action.
A perimeter protection prevention
solution, with loitering detection and
smartphone applications, has proven
to be more effective than standard
CCTV system, even with on-site security
guards. It is an innovative, reliable
and cost-effective solution for protecting
car dealerships and preventing
theft and vandalism. This prevention
solution delivers the highest detection
capabilities with the lowest false alarm
rate while offering the lowest cost per
monitored channel, and 24/7 reliable
remote monitoring.
This article originally appeared in the December 2015 issue of Security Today.