
The New World of Surveillance
Technology advancements leverage actionable information

We have entered a new realm in the world of video surveillance. Gone are the days of the security guard tethered to a dedicated desktop monitor, reacting to unfolding events within a closed environment. With today's advancements in IP-based network infrastructures, management of video surveillance can be a much more valuable endeavor.
Remote video monitoring and surveillance is defined as the ability to view, monitor, manage and react to video security information—all from a remote location. This enables a new paradigm of thinking in terms of how video surveillance is used to protect people and assets. By leveraging today's technology advancements, high-quality, actionable information can be pushed to the edge of the network with impressive velocity and reliability. The result is a much more agile management infrastructure that can allow more efficient coverage, rapid communication and proactive management that lowers overall security risk.
Regardless of the underlying technology, a well-designed video surveillance system can accomplish a variety of goals, including the deterrence of undesirable behaviors and the ability to respond to an incident with rapidity and effectiveness. Today's technology revolution, driven by a number of industries, is providing a helping hand to the security industry and allowing security experts to excel in risk mitigation by introducing the concepts of mobility and remote monitoring into the security lexicon.
The Technology
At the heart of this revolution are technologies developed for other applications that are finding their way into the security industry. The standardization that has occurred in the IP world now makes the installation, configuration and deployment of advanced video surveillance and access control products a breeze.
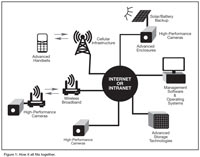
Click here or on graph to enlarge Fig. 1.
Those accustomed to plain old telephone service, also known as POTS, are familiar with the reliability that was engineered into the legacy telephone infrastructure. This inherent reliability made POTS ideal for mission-critical applications— as long as users didn't have to take a communications device with them. As cellular technology was rolled out, users traded ultra-high reliability for the convenience and economic benefits of mobility. But years of evolution have provided reliability in the cellular domain that can rival cellular's POTS predecessor.
This means the mobility that made cellular technology so popular can now be leveraged to manage video surveillance. Assets and properties can be protected while on the go, and the information collected can be rapidly pushed to law enforcement agencies or other stakeholders. Not only do these highly reliable networks enable the rapid transport of real-time video to a variety of edge devices, they also are ideally suited for voice/data communication that will accompany the video assets.
Wireless broadband also contributes to this revolution of portability. Whether inside or outside a building, today's high-bandwidth solutions are allowing the placement of cameras in locations that were once unreachable by wireline installations. We can now develop proactive environments where the propensity to remove risk dramatically increases. The result is better coverage and ease of deployment, both of which contribute to the improved value proposition for IP technology.
Advanced Storage Architectures
The explosive popularity of video for a variety of applications continues to drive innovations in storage technology. Applications such as video conferencing and video training and popular Web sites such as YouTube and Hulu have required network architects to rethink how their IT infrastructures manage traffic.
Video requires large amounts of network bandwidth and is latency sensitive. It also consumes huge amounts of storage capacity, and it is in part due to the popularity of online video clips that innovations in storage capacity, flexibility and reliability have been realized.
With today's advanced storage products, large amounts of video assets can be stored reliably and efficiently on a system network. Network-attached storage lowers the cost per byte of storage capacity by consolidating storage needs across multiple applications. And, most importantly, the redundancy and reliability that are common in these highly evolved solutions ensure the protection of potentially critical video surveillance assets.
Computer Processing Power
Moore's Law describes the long trend in computing hardware whereby the number of transistors that can be placed on an integrated circuit doubles every two years. This trend has held since the late 1950s and is not expected to be challenged until 2015.
The capabilities of digital electronic devices are strongly linked to Moore's Law. As processing capabilities increase, cameras, recording devices, servers and management software used in video surveillance all increase accordingly. The result is a network-wide expansion in terms of performance and reliability.
IP cameras allow huge amounts of processing power at the edge of the IP network. Each IP camera is actually a computer itself, and the onboard communications and analytics capabilities of today's IP cameras are truly astounding compared to just a few years ago. Couple this processing power with a reliable network infrastructure, and remote video management not only becomes a reality, it becomes downright simple.
Robust Software Platforms
Anyone who uses a personal computer can appreciate the value that well-designed software and operating systems provide. Reliable operation, powerful features and ease of use through a friendly user interface can all contribute to an experience that improves productivity and lowers cost. Combine this with the standardization that has occurred in IP and users have access to very reliable solutions that provide a gateway to the Internet.
Available video surveillance software packages that capitalize on this processing power and standardization allow management of cameras across broad networks, including wireless, and provide advanced analytics that can allow predictive, simultaneous management of multiple locations. And software provides the promise of a common control plane where all physical security applications can be managed concurrently—a huge benefit to the security industry.
Video Compression Techniques
As video has become increasingly popular as a means of communication, the impact on network infrastructures has become significant. There are two ways to address the situation: build bigger pipes by expanding the network bandwidth or transport video more efficiently by shrinkage the size of the video files. Video compression tackles the latter by using software processing power to reduce the amount of network bandwidth and storage required to manage video assets.
Compression technologies, originally devised to manage entertainment-grade videos, have been embraced by the video surveillance industry to allow the transport and storage of video security assets.
Megapixel and High-Definition Cameras
Camera buffs have a never-ending desire for higher resolution, in both video and still formats. This desire has driven advancements in processing technology that has made its way into the security industry.
Available IP camera technologies provide resolution and clarity that can allow positive identification in mission-critical settings, and the entertainment and consumer industries continue to propel this technology forward.
Innovative Power
The ability to deploy video surveillance technologies was once limited by the need for local power. Today, high-efficiency battery and solar technologies fueled by the green movement are providing a platform upon which remote surveillance outposts have become a reality. Couple these power technologies with wireless capabilities and the capability to install video surveillance in locations once deemed inaccessible. This bodes well for homeland security, border control and other remote applications where coverage should not be optional.
Summing Up the Benefits
All this talk about technology is great, but what does it mean? How do these advancements really benefit a company that relies on video surveillance and access control to lower risk? The answer is summed up by lowering the total cost of ownership.
There are many factors that contribute to lower cost. First is the use of an existing IP network. In most cases, video surveillance end users have already invested substantial amounts of capital in robust and reliable network infrastructures that include all or most of the aforementioned advanced technologies. The stage has already been set for a cutting-edge physical security infrastructure. Leveraging the installed network lowers capital costs and enables the network to be managed by existing IT personnel—a potential workforce benefit.
Since the ability to rapidly push video to many people simultaneously has become a reality, regardless of physical location, the potential exists for improved response times in the event of an incident. By combining the capability with advanced analytics, systems can often predict events before they happen. In cases where this occurs, system return on investment is immeasurably high.
Easy to Learn
One concern in the security industry is that the underlying technologies enabling the IP revolution are daunting. This is simply not the case. These solutions have been evolving for decades, and there is a wealth of training information available to get even the most devoted technophobe up and running in a short period of time. Available information and coursework on networking technology often covers all of the technologies required to hit the ground running.
Additionally, there is substantial overlap between the technologies used in traditional CCTV video surveillance and those of the IP generation. A welltrained technician who understands cameras, DVR storage technology and cabling will have no problem coming up to speed on IP networking technology. IP networking technology is driving the convergence between the security and information technology industries. This convergence makes sense in most cases because it offers an increase in performance and provides stakeholders with the actionable intelligence they need to safely manage their environments.
Remote monitoring is a reality today. Leveraging several technologies that were originally devised for different applications means a large market of opportunities for these technologies— many borne of consumer or commercial need—warranted trillions of dollars of investment from which the security industry is now benefiting. While remote monitoring seems to be new and unproven, it is actually built upon time-tested technologies that have been validated in other mission-critical applications.
Now that the technology foundation is in place, the next step will require the security industry to devise new and innovative ways to capitalize on these technologies to lower cost, lower risk and maximize the value of future deployments.