
How Tall is That Building
- By Ralph C. Jensen
- Apr 25, 2013
All of Chicago knows the building as the Sears Tower, but some residents inside the tower have paid a fee to rename it the Willis Tower. Don’t tell a Chicagoan it’s the Willis Tower, however, you’ll just get a smirk and laugh.
 The Sears Tower is 1,450 feet tall without the antennae, which is a serious “moneymaker” in its own right. The building has 4.3 million square feet of rentable space, of which 3.8 million square feet is occupied. Overall, that’s 17 city blocks that need to be accounted for in terms of safety and security.
The Sears Tower is 1,450 feet tall without the antennae, which is a serious “moneymaker” in its own right. The building has 4.3 million square feet of rentable space, of which 3.8 million square feet is occupied. Overall, that’s 17 city blocks that need to be accounted for in terms of safety and security.
Security is a pre-eminent duty for U.S. Equities Asset Management, who oversees the management and leasing of the building.
Keith L. Kambic is very pleased and proud of his security from the ground floor up, as he should be. It begins at the front doors of the building where security staff actually greet tower workers and visitors before they enter the doors. Their goal is to get to know those people who work in the building, even open a door for them. Inside, security officers continue the greetings and engage the public to make sure people know where they are going and to ensure they are going in the right direction. This is, after all, 106 floors of offices and businesses.
“We work to foster a relationship with our security officers,” said Kambic, who is the director of security and life safety at Willis Tower. “Our security team, including myself, are contract employees. We want to make them feel like they’re family. What it comes down to are people, policy and procedures.”
Kambic’s goal is to help the tenants feel comfortable, because workers spend so much time in the building. There are more than 100 different tenants; United Airlines, for instance, occupies 750,000 square feet of space for their 4,500 employees.
More than 12,000 employees stream into the facility on a daily basis, and building officials believe that nearly as many visitors and guests arrive on a daily basis as well. More than 125 trucks use the buildings loading dock on a daily basis, and the 104 elevators are powered by two locomotive engines.
Building the skyscraper was done by using a different design, meaning that Willis Tower is actually nine buildings all tied together. At the very heart of the security are the turnstiles, still in use, that have at best guess allowed more than 150 million workers to come and go.
“We look at everything and train for everything,” said Kambic, who works with and trains 65 full-time security officers. Training is a key point with the tower managers, who also conduct annual drills with the Chicago Fire Department and employ evacuation drills for building workers.
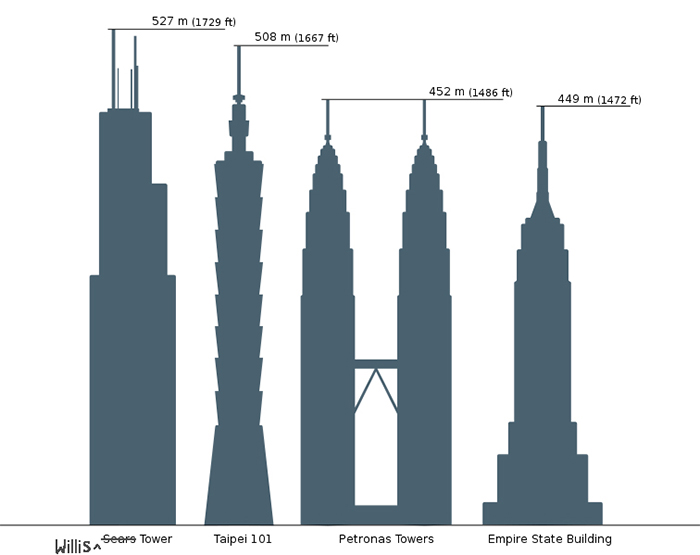
**Interesting graphic by Mason Currey of Metropolismag.com:
About the Author
Ralph C. Jensen is the Publisher/Editor in chief of Security Today magazine.