
How to Set Up Your Twitter Profile as a Security Professional
- By Ginger Hill
- Oct 17, 2014
As the security industry slowly embraces the use of social media, more and more professionals like you are seeking to learn about the various platforms. One such platform is Twitter, a free communications tool that provides a quick, 140-character snapshot of your thoughts. This is a great way to communicate with end users, integrators and manufacturers within the security industry. Plus, as Security Today gears up to offer Twitter chats related to the industry, you’ll want to be fully involved in these discussions! You have a lot to learn, but first you must set up your Twitter profile to reflect you as a security professional.
Here’s how to set up a Twitter profile:
- Go to www.twitter.com.
- Look for the box that has “New to Twitter? Sign up” in it.
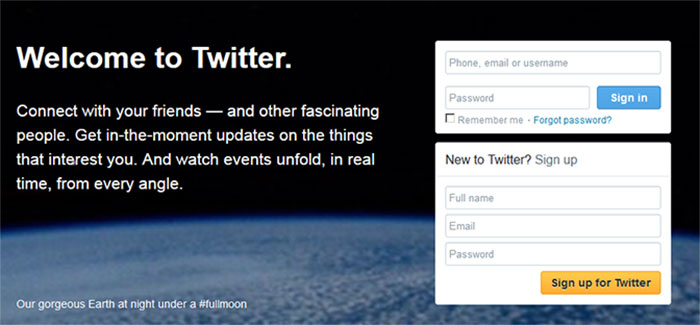
- Enter your full name, email and a unique, hard-to-guess password using letters, numbers and symbols.
- Click the gold color “Sign up for Twitter” button.
- When you click that button, you will be directed to a page that looks like this:
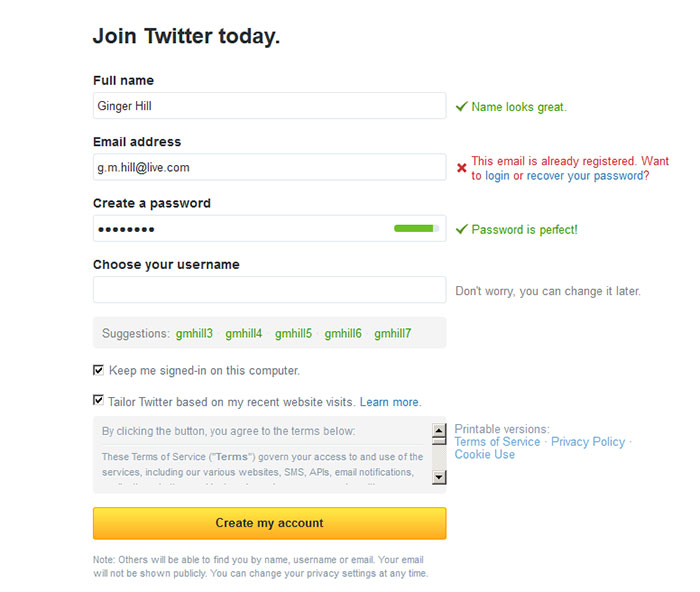
- Now it’s time to choose your username. This is known as your Twitter handle and it has the “@” symbol in front of it. It’s okay to be a little creative with your username, but take into consideration that you only have 140 characters per tweet, counting your username. Also, you are representing yourself as a professional, so avoid using anything that could seem improper.
- For security purposes, make sure the little box in front of “Keep me signed-in on this computer.” and “Tailor Twitter based on my recent website visits.” does NOT have check marks.
- Finally, click the gold “Create my account” button.
And, there you have it…your very own Twitter account! Congratulations!
Next, I’ll be explaining how to spruce up your Twitter profile to enhance your image as a security professional. Stay tuned!
About the Author
Ginger Hill is Group Social Media Manager.