Poor trading conditions right across the developed world in recent years have caused physical security equipment buyers to hold back on replacing old systems unless they can be sure that the new systems improve the effectiveness of security, reduces operating cost and delivers an improved and satisfactory ROI on their investment.
There is only one way to meet this challenge and that is for manufacturers to continue with their innovation programs of delivering more effective systems at lower prices and through convergence with the business enterprise deliver value add services.
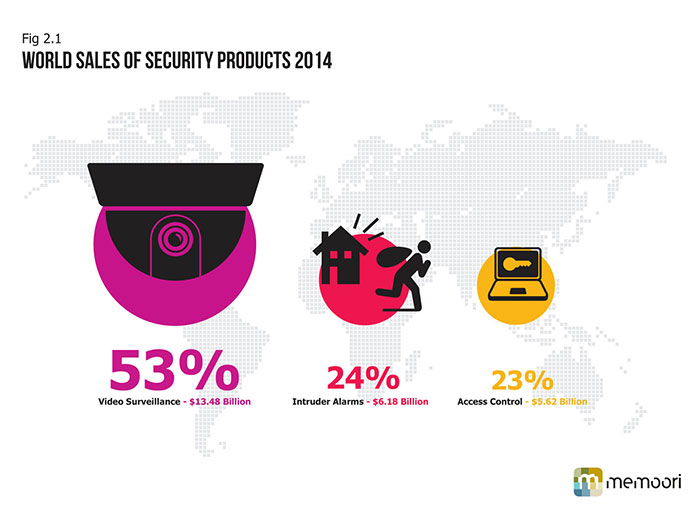
Our new research report is a complete assessment of Video Surveillance, Access Control & Intruder Alarms markets in 2014; and also analyses growth to 2018.
The focused specialist players have spent heavily on their product development programs and are now reaping the benefits of increased market share and this is one of the main reasons why the security industry has come out of the recession earlier and in a much better shape than most other industries.
This steady consistent growth since 2011 has been driven by a combination of factors including strong growth in IP Video Networking and IP Access Control products, buoyant markets in Asia and North America and higher levels of penetration in vertical markets such as transport, retail, health and education.
Access Control Moves to IP
Access control, for so long the poor relative of video surveillance, this year it has come out of the shadows and upstaged it by delivering a higher growth rate and we forecast that it will continue to increase its growth rate over the next 5 years.
This will be achieved by moving to IP Technology and integrating Access Control with Identity Management. There can be no doubt about the business case for integrating these services. Identity Management for the purpose of Access Control has given rise to a number of major acquisitions in the last 5 years. September 2010 saw a flurry of activity with the purchase of L-1 Identity Solutions by Safran for $1.1 billion, 3M’s purchase of Cogent Systems for $430m, the merger of AuthenTec and UPEK. In 2014 whilst the number of deals declined, this group accounted for 19.2% of the total number of acquisitions and 5.6% of the total value.
Physical Identity and Access Management (PIAM) is also a service that promises to deliver further growth opportunities. It enables common policy, workflow, approval, compliance automation and life cycle management of the identity / badge holder (employee, contractor, visitor, temps) across disparate physical security systems. The key benefit from PIAM solutions is operational cost reductions that can be delivered through this platform providing a bridge between the disparate systems, without stripping out and starting again. PIAM has so far failed to attracted the mainstream PACS business.
There is a steady stream of alliances and partnerships between PIAM Software companies & PACS companies but so far we have not identified any mergers and acquisitions. Information on the business is pretty sparse and most “best estimates” on the market size range around $150 million. This if accurate is quite small considering that virtually all Fortunes Top 500 companies must have installed one.
Improved Performance, ROI, and Reduced TCO
Now has to be the time to dig even deeper and for manufacturers to increase their efforts to align the motivation of security buyers to invest in better performing systems through educating and training both themselves and those in the distribution channel in order to drive out all the benefits.
Whilst technology has been the enabler of change, the driver and motivator is now clearly to channel this to deliver products and services that increase productivity and provide a better ROI and reduce the TCO. This is gradually changing the buyer’s culture from believing that physical security is a pure cost center to a profit center.
Security, sadly, is still regarded by most end users as a cost center and as such has been towards the end of the food chain for capital investment. This can be crucial when budget reductions are on the agenda. However a gradual change in attitude by buyers is taking place. Specifically that security can be a cost saver when reducing shrinkage (retail) and that when integrated with other services it can increase productivity in the business enterprise and therefore reduce operational costs. This has been made possible through IP convergence and in some vertical markets such as retail there is a growing belief that IP Video Surveillance should be treated as a profit center.
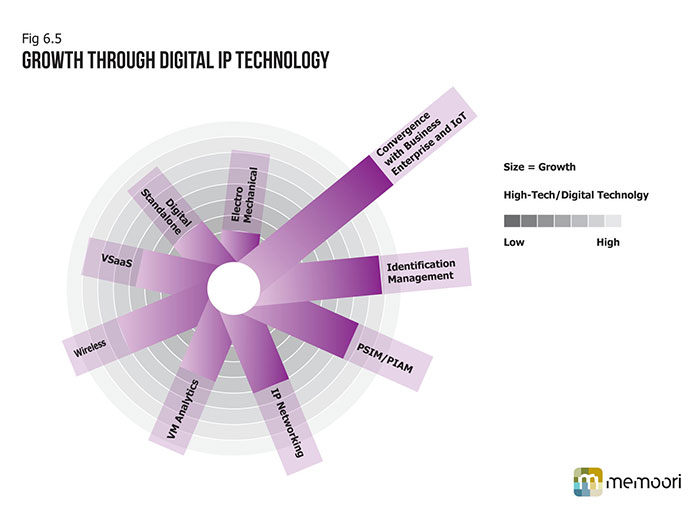
This has had a major impact on increasing the value-add on security projects. The market has not been slow to see the opportunities and changing requirements for more converged and integrated solutions. In order for companies to deliver such systems many have decided that it is necessary to acquire, merge or form alliances and partnerships with other suppliers. In order to maximize the opportunities of delivering on ROI it is vital for suppliers to have specialist knowledge and experience in vertical markets. But equally important is to have the networking skills to join all the vertical and horizontal layers of product together with the analytical software and interface with the other building services software and finally join them to the business enterprise. Video Surveillance is already on route to establishing an important role in the Building Internet of Things ( BIoT) and the wider IoT.