U.S. Central Command Twitter Account Hacked by ISIS
- By Ginger Hill
- Jan 12, 2015
After a series of unusual tweets were published from the U.S. Central Command Twitter account, it was soon discovered that the account was in fact hacked. This Twitter account has since been suspended but not without some very revealing Tweets going live.
Around 11:30am, CST, the first tweet was published in all caps: “AMERICAN SOLDIERS, WE ARE COMING WATCH YOUR BACK. ISIS.”
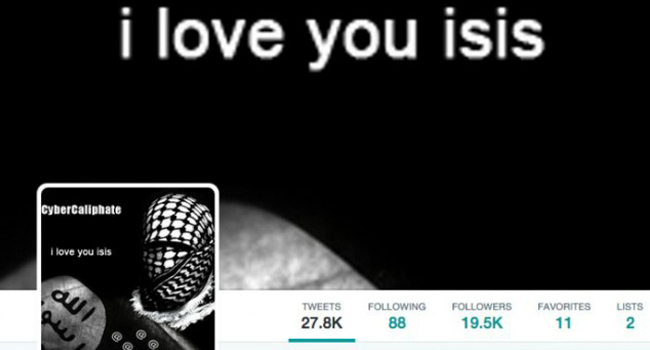
Then, the U.S. Central Command’s Twitter account profile became a black-and-white image of a persona wearing a scarf around their head. In white lettering against a black background, “CyberCaliphate” and “I love you isis” was prominently seen at the top of the page.
About an hour later, it was discovered that U.S. Central Command’s YouTube page was apparently hacked as well because it contained ISIS propaganda videos with militant fighters.
About the Author
Ginger Hill is Group Social Media Manager.