The network-based physical
security industry has
matured rapidly over the
past few years. As the
technology and other
components of security solutions have
advanced, so too have the customer’s expectations.
Security solution companies
must evolve in order to meet these new
expectations. This requires an understanding
of the technology, the customers’
motivators, issues and hot buttons.
Arriving at that understanding requires
taking a step back to look at
entire solutions. As video management
software (VMS) has become more sophisticated,
so have the accompanying
hardware components.
Proof of this is everywhere. Camera
technology can now provide much
higher levels of detail due to greater
capabilities with megapixel and HD.
Another example is today’s IP access
control software, which offers customers
a more flexible way to manage their
facilities. Innovative monitoring tools
can recognize security equipment that
needs repairs before malfunctions become
expensive or fail completely.
A New Approach
In 2012, Milestone recognized that
these changes were significant enough
to warrant a new go-to-market 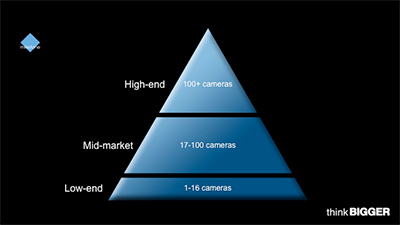 approach.
Rather than making changes
gradually, the company incorporated
the new market realities into the creation
of three new business units. Each
business unit would specialize in developing
new hardware, software and related
services to meet the accelerating
pace of changing customer security solution
requirements.
approach.
Rather than making changes
gradually, the company incorporated
the new market realities into the creation
of three new business units. Each
business unit would specialize in developing
new hardware, software and related
services to meet the accelerating
pace of changing customer security solution
requirements.
In order to effectively address all customer
segments, Milestone left behind
the old physical security market’s segmentation
model, which was based on
the number of cameras installed per
site. Instead, as the graphics below illustrate,
the company began to determine
customer needs based on whether
deployments are needed at one or many
sites and whether security/surveillance
needs are low or high complexity.
National retail chains and utility
companies provide an excellent example
of this new perspective on assessing customer
needs. Each small retail shop may
only need one or two cameras for monitoring,
but there may be hundreds if not
thousands of locations across geographies.
An electrical utility installation,
on the other hand, may be housed on a
single site but have security needs that
are highly complex and critical.
How can a single solution accommodate
customers with such different
needs? Simply put, it cannot. Such
varying needs require a diverse portfolio
of solutions to provide the features
and capabilities appropriate for each
type of organization.
Early Adopters and
Pragmatists
One of the factors driving change in the
network-based physical security industry
is a change in the buyer’s tolerance
and acceptance of technological risks.
There is a very specific type of person
who is willing take the necessary risks
often associated with using new technology.
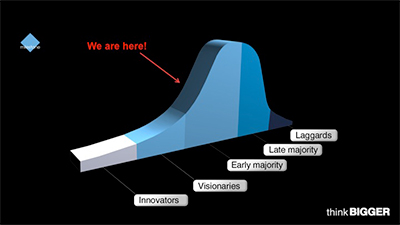
Known as the ‘early adopter’ in
Geoffrey A. Moore’s landmark book,
Crossing the Chasm, the individuals
who purchased early network-based security
products were risk takers, agents
of change and visionaries. The early
adopters tended to place comparatively
small orders and, perhaps most importantly,
sought out specialized integrators
for advice and assistance.
 After a decade-long, continuous improvement
of technology, the adoption
risks have been reduced. Evidenced by
the firmly entrenched acceptance and
usage of networked-based physical security
solutions, this transformation
has enabled the more risk-averse pragmatist
customer, or, in the parlance of
Moore, the “early majority customer,”
to start the security technology adoption
lifecycle.
After a decade-long, continuous improvement
of technology, the adoption
risks have been reduced. Evidenced by
the firmly entrenched acceptance and
usage of networked-based physical security
solutions, this transformation
has enabled the more risk-averse pragmatist
customer, or, in the parlance of
Moore, the “early majority customer,”
to start the security technology adoption
lifecycle.
It’s important to understand that
early majority customers comprise 33
percent of the overall market. As of
2014, this group has only just begun
adopting networked security. This customer
segment is considered “the next
big wave.”
There are several assumptions that
can be made when determining how to
best approach a buyer who fits into this
segment, including:
- The early majority customer, fully
aware of the evolution of the industry,
expects the technology to be
more advanced to address more complex
needs.
- The early majority customer is not
looking to invest in stand-alone
components but in an overall platform
solution.
- The early majority customer prioritizes
the technology’s functionality
and operational effectiveness.
Most significantly, this new early
majority customer is not interested in
investments that are anything less than
rock solid. There are several ways to
make sure the customer has confidence
in the portfolio he’s investing in. The
simplest way is to ensure that each and
every component has customer and
technical “reference-ability.”
Recalibration and
Best Practices
The emergence of the early majority
customer—a pragmatist—and the maturation of the network-based physical security
industry are fundamental changes.
The combination of these market changes
requires not only a new approach to
solutions but also for a much more pragmatic
way of servicing customers.
In a word, the transformations in
our industry call for a recalibration.
While the process of recalibration is
different for each organization, there are
a few tried-and-true general guidelines.
Applying these best practices is critical
to correctly identifying how to most effectively
reach today’s customers.
First, introduce risk-mitigation tactics.
These can include guarantees of
operational readiness evidenced by real
system proof-of-concept, pilots and
rollouts.
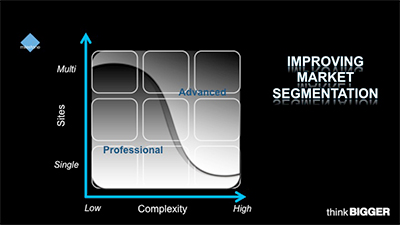
Offer a portfolio of hardware, software
and services to address every
need within the new segmented market
model, as shown in the matrix illustration
above, which speaks directly to the
needs of the early majority customer.
These customers expect manufacturers
to address high or low complexity needs
and scale within a project, rather than
just size and scope.