The Information Technology and Innovation Foundation (ITIF) released a comprehensive analysis of how privacy advocates trigger waves of public fear about new technologies in a recurring “privacy panic cycle.” ITIF urged policymakers to recognize these panics and not allow hypothetical, speculative, or unverified claims to distort the policy process or inhibit new innovation.
In a new report released today, “The Privacy Panic Cycle: A Guide to Public Fears About New Technologies,” ITIF outlines the stages of public panic and the factors and trends influencing these stages, along with examples of how the panic cycle has repeatedly played out throughout modern history—from the first portable camera to search engines to drones.
“People have a remarkable ability to see through clever marketing hype about ‘revolutionary’ new technologies. But most lack the same healthy skepticism when it comes to overheated rhetoric about privacy threats that those same innovations allegedly pose,” said Daniel Castro, vice president of ITIF and a co-author of the report. “We’ve seen it time and again. A technology is introduced, privacy advocates claim that the sky is falling, and then the media and others fan the flames of fear. Eventually, though, people understand the technology, discover that the supposed privacy nightmare has not come to pass, and embrace the benefits of new innovation. Everyone then moves on—until the next technology comes along and privacy advocates initiate the panic cycle all over again.”
ITIF’s analysis finds that this privacy panic has four stages:
- Trusting Beginnings: In the “Trusting Beginnings” stage, the technology has not been widely deployed and privacy concerns are minimal. This first stage ends when privacy advocates raise alarms, creating a “Point of Panic.”
- Rising Panic: In the “Rising Panic” stage, the media, policymakers, and others join the privacy advocates to further spread concern until fears hit their peak at the “Height of Hysteria.”
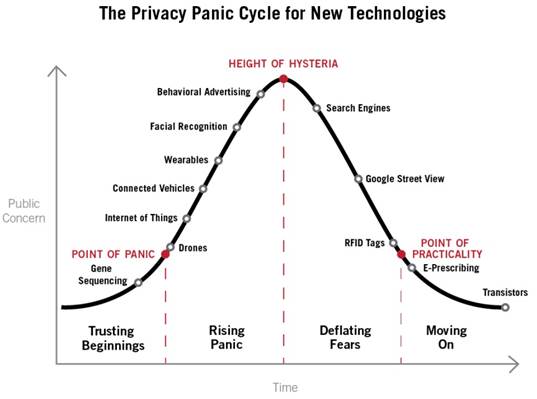
- Deflating Fears: As the public comes to better understand the technology and its benefits, the panic starts to dissipate in the “Deflating Fears” stage until it eventually hits the “Point of Practicality.”
- Moving On: The public reaches the “Moving On” phase when the vast majority of consumers no longer believe the privacy claims espoused by the privacy advocates because they understand the technology, appreciate its benefits, and no longer fear its misuse.
ITIF’s report provides examples of the panic cycle throughout U.S. history, including the first portable camera in the late 1800s, transistors in the mid-1900s, and radio frequency identification tags in the early 2000s. ITIF also suggests the panic cycle is playing out today with new technologies, including drones, wearable technology like Google Glass, and even search engines.
“Privacy is an important issue to consider as new technologies are developed,” said Castro. “But given that in case after case, we’ve seen wildly exaggerated privacy claims never fully materialize, these panics should be taken with a grain of salt. We don’t want to bog down innovation and progress just because a group of privacy advocates stokes fears out of proportion. Policymakers should keep the privacy panic cycle in mind when they are making policy decisions, especially when the public has been whipped into a fury by overwrought—and ultimately fleeting—privacy concerns.”
Read an infographic summary of the report here.
Read the full report here.