
SPONSORED
Your Best Project: Ten Security Design Tools You Must Try
- By Steve Surfaro
- Sep 06, 2016
Designing for the Customer; Creating with the Customer
“You can design and create, and build the most wonderful place in the world. But it takes people to make the dream a reality.”
-Walt Disney
Ask a single security designer for advice, and it's difficult to know whether we should solicit another opinion. Ask ten, though, and you'll see a clearer picture begin to coalesce.
Some may call that polling, learning diversity, or even the modern term crowdsourcing, but in any case it's one of the best ways to gather insight. No single perspective or process applied to a security use case can result in a flawless design.
Continuous Improvement in Design
The Japanese noun and verb “Kaizen,” includes some significant approaches to how design tools are used.
改 + 善 = “to change, alter or transform” + “good” = Kaizen:
An action taken to improve (n); a spontaneous change for the better (n); for something to improve on its own (v)
Place video surveillance cameras, intrusion sensors and a communications network around a physical or virtual protection path around the circumference of your soft target, and you have taken a first, important step towards perimeter defense. To verify the design integrity, the process should include improvement, formerly known as “value engineering,” today as value redesign (see figure).
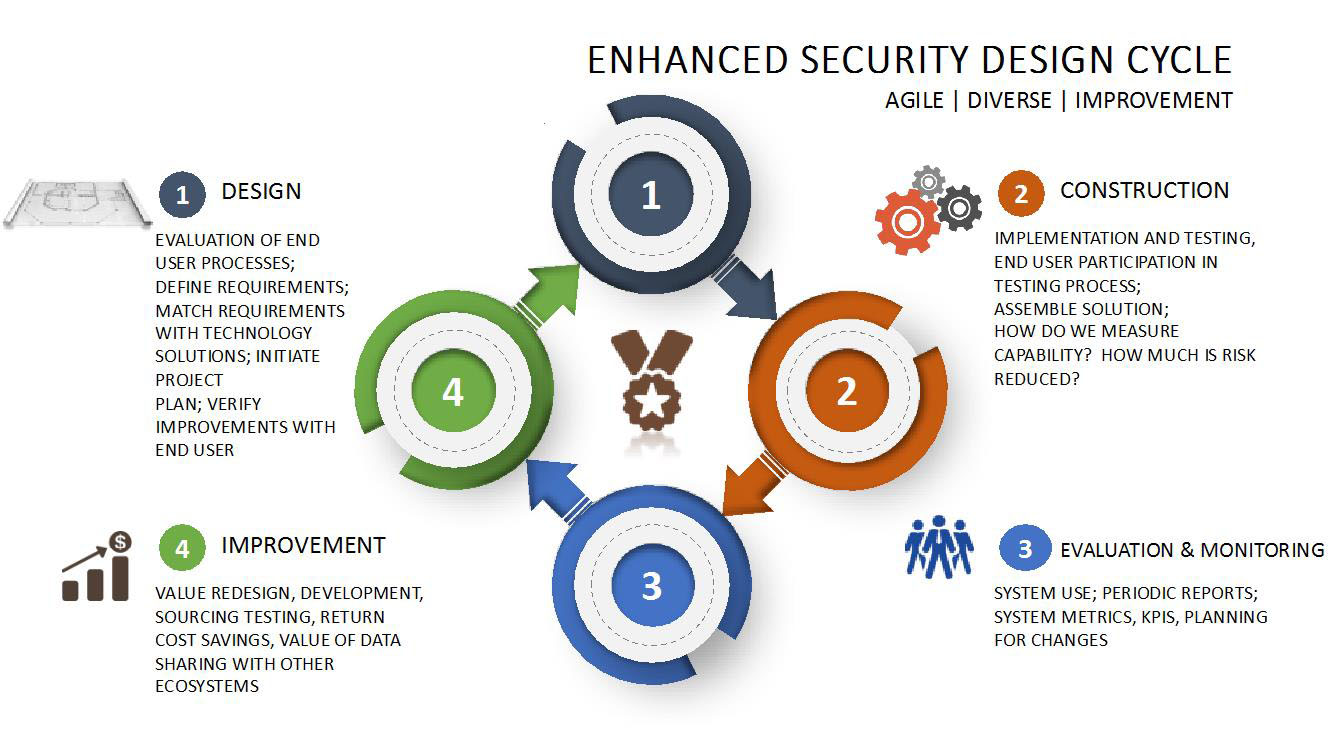
Figure 1 Using Tools to Improve your Design
Get ready for Video Surveillance: AXIS Design Tool
One useful tool, the AXIS Design Tool estimates bandwidth and storage needs for a single or all the cameras in the surveillance project. For each camera, you can pick a scenario, and select viewing, recording and compression options to get bandwidth and storage estimates that match the surveillance situation. For example, our outdoor entry camera near the reception area, when viewing and recording at 18 frames per second (FPS), with event recording 20% of the time actually yields the same bandwidth and storage by lowering the frame rate to 10 FPS and increasing the event recoding estimation percentage to 50% (see figures).
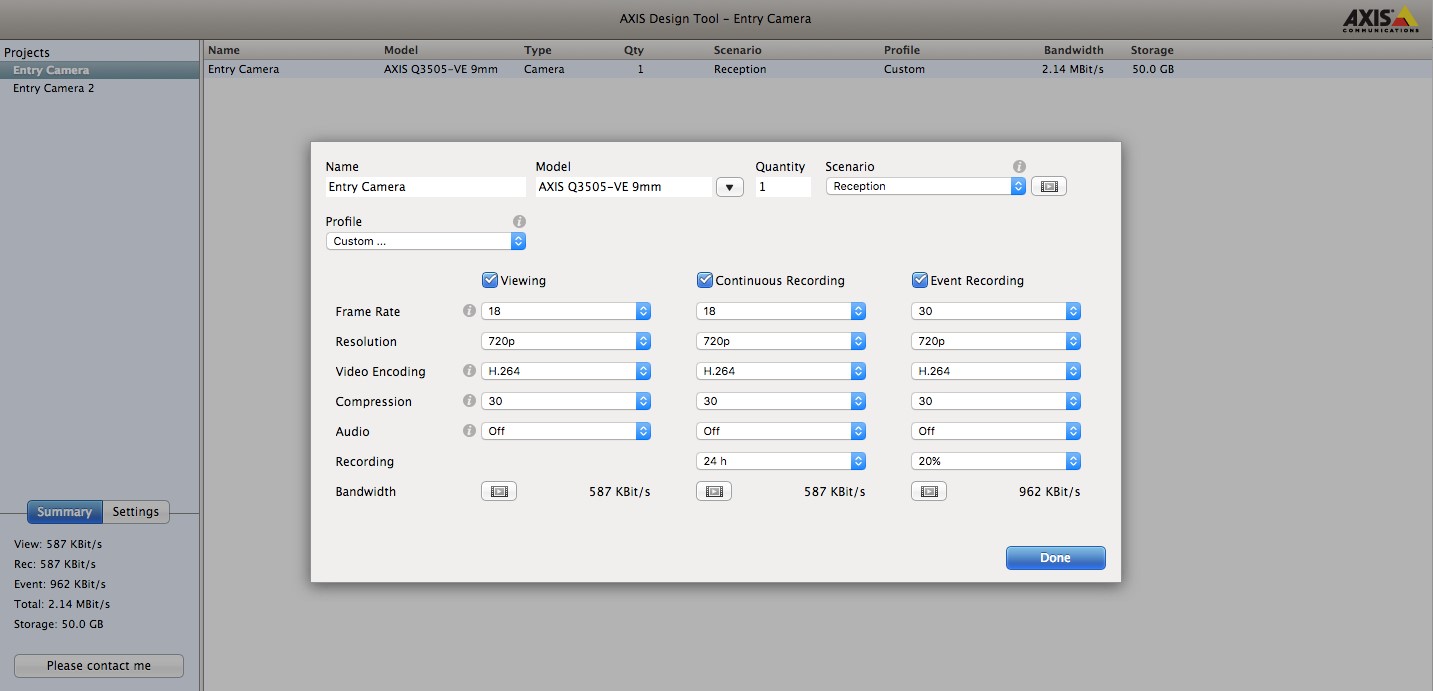
Figure 2 Design Tool Figures
Network design is challenging, requiring designers to balance user performance expectations with network-resource costs, capacities, capabilities, and use scenarios. IT Managers want to keep resource utilization high and costs low. The resulting design might produce unacceptable service levels to the Security Manager when congested links and undersized routers cause too much delay or dropped packets. The best design may be a compromise that will efficiently use your network resources and effectively serve your users. Solution, accessory, device and network design tools can closely simulate the actual field practice.
With network-based security systems using a mix of applications, protocols, device technologies, traffic flows, and routing algorithms, there may hundreds of feasible configurations, each with different performance attributes and costs.
Challenge: do you have to sacrifice throughput and performance for high image quality?
In a word, no! Significantly more efficient implementation of AVC/h.264 video encoding, and purpose-built for surveillance applications, Zipstream analyzes and optimizes the video stream in real time to save bandwidth and storage while maintaining image quality.
A video clip contains 25 or more frames per second. Instead of sending the entire frame every time, a video codec can save a lot of data by only sending the differences between frames. The digital multimedia content (video, audio, metadata) carrying capacity of a network connection is commonly known as bitrate or bandwidth and is measured in megabits per second. A 4G mobile connection might be capable of carrying multiple megabits per second; a home broadband connection may support ten times that amount. To encode and stream video efficiently, the bitrate or bandwidth capacity of the network connection must be greater than the bitrate of the streaming media file.
Using networked video with Variable Bit Rate (VBR) allows the quality to adapt to scene content in real-time. Using Constant Bit Rate (CBR) as a storage reduction strategy is not recommended, since cameras delivering CBR video may have to discard important forensic details in critical situations due to the bit rate limit. Zipstream rendering preserves moving scene elements while static areas are rendered at a higher compression. Should movement enter the static areas, the scene rendering is adapted quickly to preserve details.
Will proposed changes in the network such as additional network cameras handle the anticipated traffic demand? Does the design require wireless links? These tools are not only suitable for presentations to customers, they can provide fast answers to “what if” questions?
Tools analyze (visually, mathematically, or by simulation) what is happening in the security network and simulate future behavior.
Some of these tools, like AXIS Site Designer and AXIS Camera Families can display results graphically, use during the course of the security solution simulation to highlight vulnerabilities, potential errors, missed surveillance coverage, imaging issues, network bottlenecks and traffic flows. In addition, the data from these tools may be used to provide comprehensive reports to Security and IT Management and summarize network congestion, load potential failure scenarios and network response times.
Who uses security network design tools?
The ideal network design tool can mean different things to different people. But whether you’re a security or network designer, security or IT manager or engineer, sales or marketing manager, there is a useful tool complete with intuitive graphical interfaces that resemble computer aided design tools.
As a designer, you not only specify and build new solutions and networks, but upgrade existing systems. Designs need to meet performance requirements without overbuilding. The ability to identify vulnerabilities, potential network bottlenecks and overloads are critical considerations. Designers need an extensive library of security technologies, devices, architectures, and protocols to build or upgrade the security solution and network and tools to accurately
predict performance.
Match the tool to you
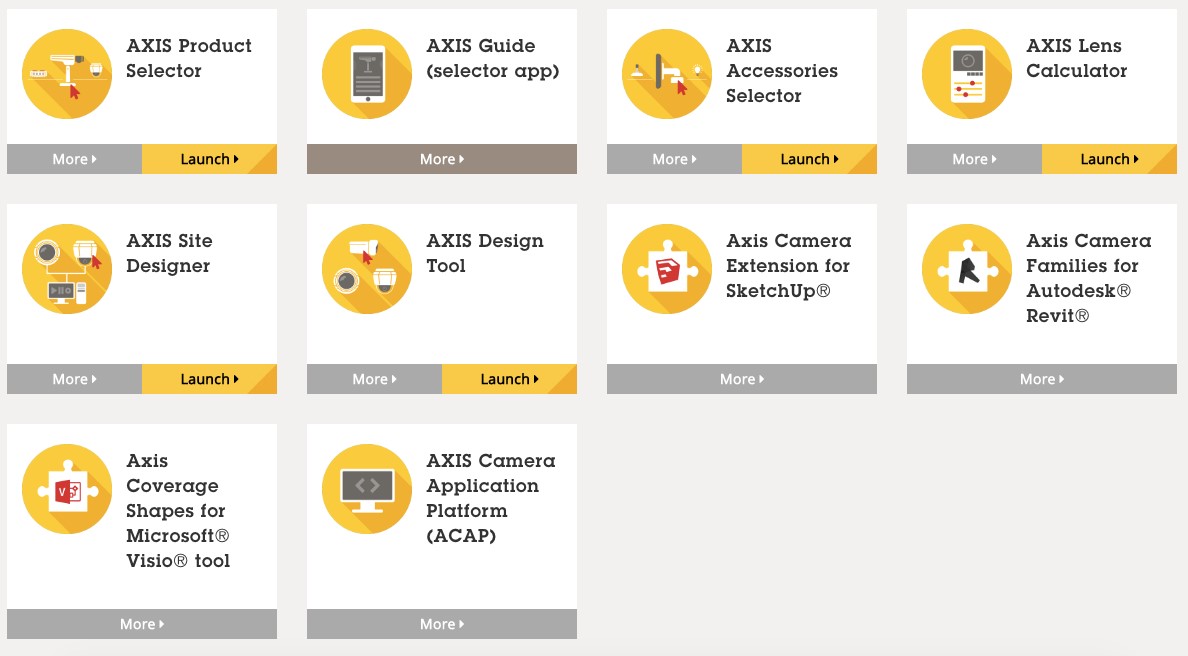
Figure 3 Axis Tool Selection
Consider which features best support you, based on the type of user you are.
|
TOOL
|
Systems Integrator
|
Security/IT Manager
|
Security/IT Designer
|
|
AXIS Product Selector
|
X
|
X
|
X
|
|
AXIS Guide
|
X
|
X
|
X
|
|
AXIS Accessories Selector
|
X
|
|
|
|
AXIS Lens Calculator
|
X
|
X
|
X
|
|
AXIS Site Designer
|
X
|
X
|
X
|
|
AXIS Design Tool
|
X
|
X
|
X
|
|
AXIS Camera Extension for SketchUp®
|
|
|
X
|
|
AXIS Camera Families for Autodesk® Revit®
|
|
|
X
|
|
AXIS Coverage Shapes for Microsoft® Visio®
|
X
|
X
|
|
|
AXIS Camera Applications Platform
|
X
|
|
|
AXIS Site Designer
With AXIS Site Designer, you’ll be able to pick just the right cameras for any surveillance scenario. Adding accessories and picking a recording solution is quick and easy. When done designing your project, AXIS Site Designer prints a comprehensive bill of materials that includes everything you need to complete your installation. Learn more about the features of AXIS Site Designer below.
AXIS Site Designer is a web application that is easily accessible on axis.com form your tablet or PC with no additional software to download or install. Once you have started the application, it can be used even when off-line.
With AXIS Site Designer, you can keep track of multiple projects. Project templates provide a quick way to get new projects started. If you log in to axis.com using your MyAxis or partner login, your work will be saved on Axis’ servers, and you can access your projects from any browser.
The all new camera selector finds the right camera for your scenario. Set up your scenario and get a shortlist of cameras that fulfill your needs.
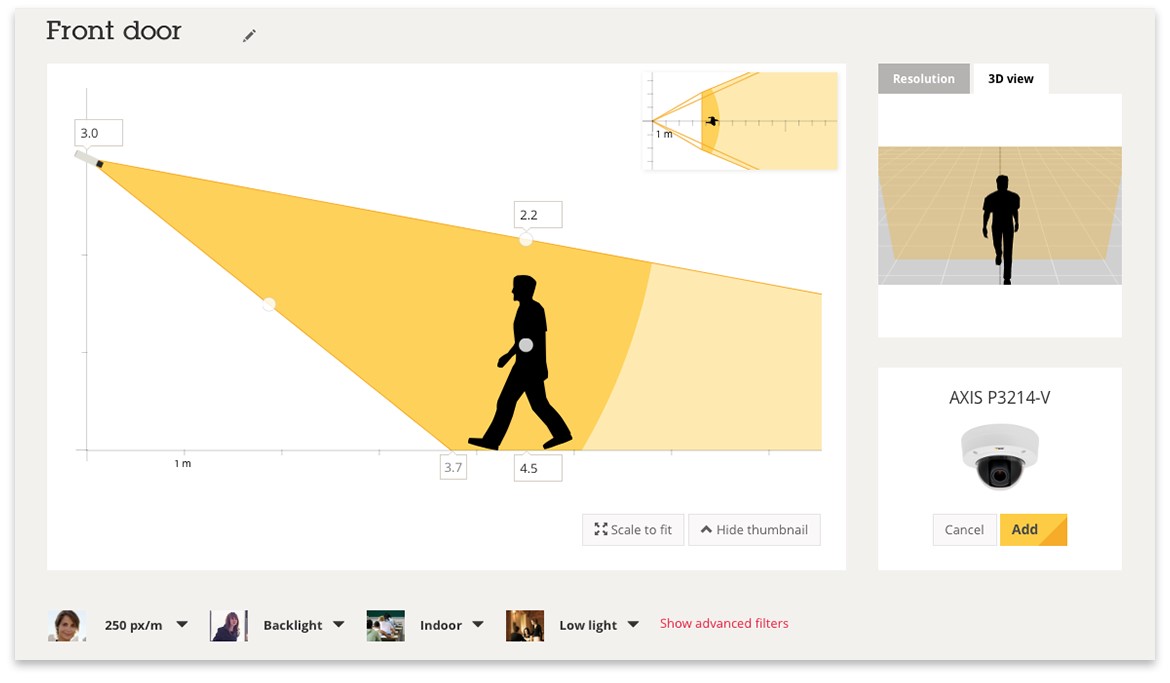
Figure 4.1 AXIS Site Designer
AXIS Site Designer knows which accessories work with your selected camera. This takes the effort out of finding the right mounts and other accessories for your needs.
AXIS Site Designer recommends the storage solutions that fit your project and video recording requirements. For maximum convenience, pick one of the AXIS Camera Station S10 Recorder Series models.
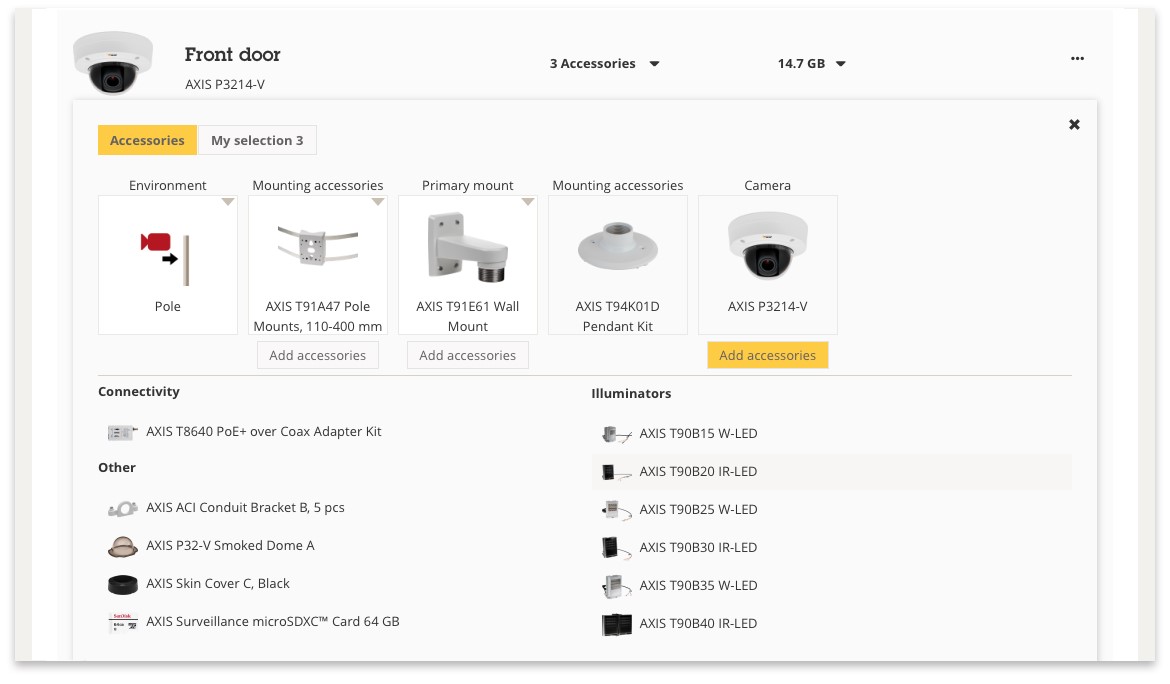
Figure 4.2 AXIS Site Designer
You can add any Axis product to you project, and enter your own selection of networking and other components to create a complete bill of materials that includes everything needed to complete the project.
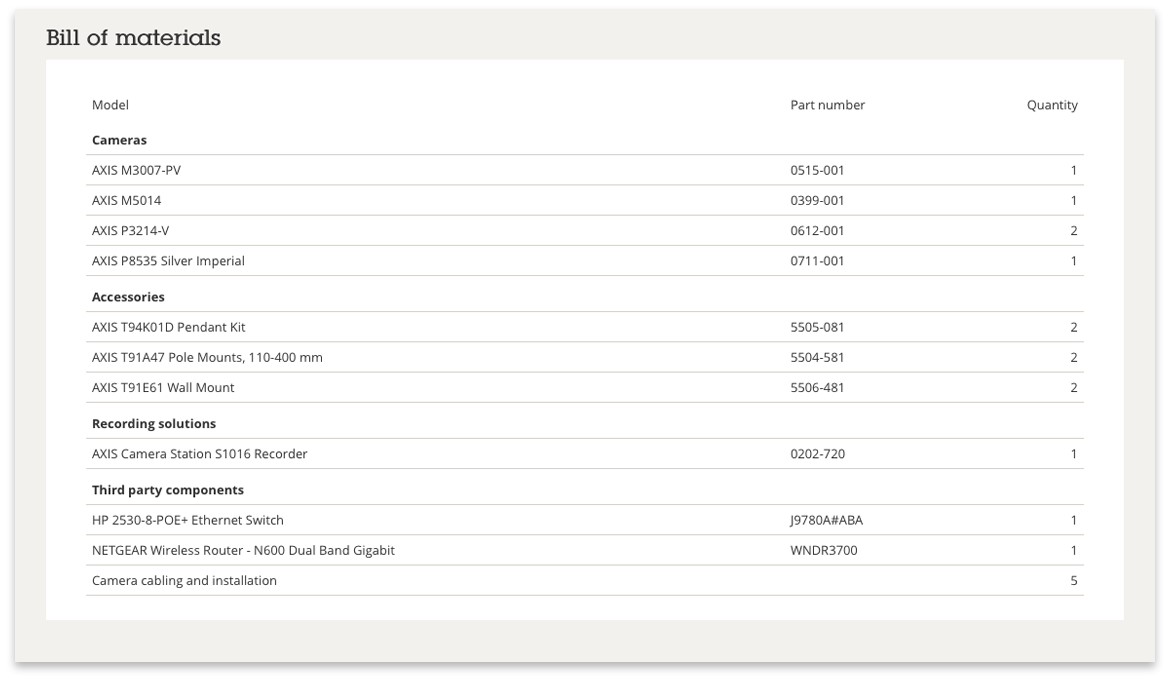
Figure 5 Bill of Materials
Tools for Collaborative Security Design
Whether you're designing a new product, improving your site, or just seeing if more people like low light cameras than 360∞ cameras , your best bet is to collaborate. To do so, you'll need a framework to generate a unique and innovative design (see figure). As we have seen, many of these tools come from AXIS, are used by third parties, allow accurate technology matching and generation of bills of materials.
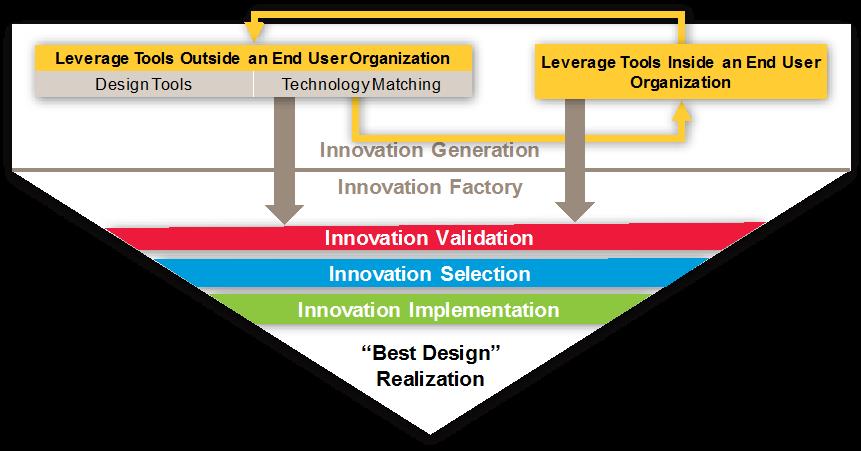
Figure 6 The Design Tools Framework
For Designers and First Responders in Law Enforcement, Fire, EMS, HAZMAT, Search and Rescue, Explosives and Communications disciplines, there are also tools within agencies to support these specialties. One such tool is the Digital Video Handbook by the US Dept Homeland Security Science and Technology Directorate.
A list of topics covered by the Digital Video Handbook are below:

Figure 7 Digital Video Quality Handbook (Place to the right of the bullet points)
- Digital multimedia content analysis
- Entry screening queue line video analytic system
- Trends
- Technology expansion in public safety: IoT, sensors and analytics
- Case study: HD and network video: moving public safety and schools forward in security
- Navigating the security and public safety industry: from associations to standards
- UltraHD and the video surveillance industry
- UltraHD resolutions
- Next generation video codecs in action
- Tactical video and situation awareness advantages
- First responders and tactical video
- Crime fighting tactical video intelligence
- Encoding for the surveillance industry
- Bit rate reduction
- Comparison of HEVC bit rate savings over AVC
- Next gen codec design considerations
- IoT, sensors and analytics
- Cyber security of IoT sensors
- IoT and cyber security FAQ
- ASIS international security applied sciences facility model
- Forensic video program readiness
- Digital multimedia content — more than just video data
- Forensic review
- Video content analysis
- Digital multimedia evidence
- Checklist: preparing for digital forensics
- Checklist: implementing a forensic video readiness program
- Top technology considerations in forensic video
- Criminal pattern identification and security/video data
- Linking DMC to policy
It is a great challenge to tell a customer what they want. However, you may be able to approximate and even predict what they want before they realize they want it. When you think about it, IT and Physical Security Managers often have to predict their users’ needs even before they know what they need - they are in a reactive mode. Tools like the AXIS Design Tool and the Digital Video Handbook help our first responders get ahead of the threat.