Paxton Access, a leading global manufacturer of security technology solutions announced this month that construction on their new US headquarters is complete. The company’s intention has been to grow their US footprint by investing $10 million in the project in Greenville, SC.

Change Your Password Day is right around the corner. Observed every year on February 1, the day aims to raise awareness about cybersecurity and underscores the importance of keeping passwords strong and up to date.

DP World Yarimca, one of the largest container terminals of the Gulf of İzmit and Turkey, is a strong proponent of using industry-leading technology to deliver unrivaled value to its customers and partners. As the port is growing, DP World Yarimca needs to continue to provide uninterrupted operations and a high level of security.To address these challenges, DP World Yarimca has embraced innovative technological products, including FLIR's comprehensive portfolio of security monitoring solutions.
Napco Security Technologies Inc. is pleased to introduce the NAPCO StarLink SLE-MAX2-DEMO, a sophisticated but easy-to-use tool with its StarLink Max 2 Dual Sim Commercial Fire Communicators. It’s designed for two key purposes: performing site surveys or sales demos. First, it visually demonstrates the Communicator’s ability to switch between carriers quickly & second, it displays signal quality for both cell networks to the Authority Having Jurisdiction (AHJ) and more discerning potential customers.

In the artificial intelligence race powered by American companies like OpenAI and Google, a new Chinese rival is upending the market—even with the possible privacy and data security issues.
- By Brent Dirks
- Jan 28, 2025
Arrow Security is pleased to announce the addition of Jerry Clark, Ph.D. as the company’s Senior Vice President of Business Development and John Hynes as Senior Business Development Manager for its New Jersey regional office.
On Data Privacy Day (Jan. 28, 2025), the Security Industry Association (SIA) has released a set of new and updated resources and programs around data privacy for security industry professionals.

Today, Cyber Performance Center, Hack The Box, released new data showcasing the perspectives of Chief Information Security Officers (CISOs) towards cyber preparedness in 2025. In the aftermath of 2024’s high-profile cybersecurity incidents, including NHS, CrowdStrike, TfL, 23andMe, and Cencora, CISOs are reassessing their organization’s readiness to manage a potential “chaos” of a full-scale cyber crisis.
ASIS International and the Security Industry Association (SIA) – the leading membership associations for the security industry – have announced details for the 2025 Security LeadHER conference, a special event dedicated to advancing, connecting and empowering women in the security profession. The third annual Security LeadHER conference will be held Monday, June 9 – Tuesday, June 10, 2025, at the Detroit Marriott Renaissance Center in Detroit, Michigan.

DeNexus, a provider in end-to-end cyber risk management for operational technology (OT) in Industrial Enterprises and Critical Infrastructures with cyber-physical assets, today announced the results of a comprehensive analysis of 254 industrial sites across North America, Europe, and Australia has revealed that 92% of sites face significant cyber exposures related to remote services, with potential losses reaching up to $1.5 million per site.

You would think in a world where cybersecurity breaches are frequently in the news, that it wouldn’t require much to convince CEOs and C-suite leaders of the value and importance of security awareness training (SAT). Unfortunately, that’s not always the case.
- By Stu Sjouwerman
- Jan 24, 2025

Windsor Port Authority, one of just 17 national ports created by the 1999 Canada Marine Act, has enhanced waterway safety and security across its jurisdiction on the U.S.-Canada border with state-of-the-art cameras from Axis Communications. These cameras, combined with radar solutions from Accipiter Radar Technologies Inc., provide the port with the visibility needed to prevent collisions, better detect illegal activity, and save lives along the river.
Stone Security, renowned for its exceptional security integration services and unwavering commitment to its employees, partners and customers, is on track to move into the top 10 largest security integrators in North America.
- By Ralph C. Jensen
- Jan 23, 2025

Netwrix, a vendor specializing in cybersecurity solutions focused on data and identity threats, surveyed 1,309 IT and security professionals globally and recently released findings for the healthcare sector based on the data collected. It reveals that 84% of organizations in the healthcare sector spotted a cyberattack on their infrastructure within the last 12 months. Phishing was the most common type of incident experienced on premises, similar to other industries.
Genetec Inc., provider of enterprise physical security software, today announced that it has been named one of Canada’s Top Employers for Young People by MediaCorp Canada for the 2nd year in a row.

ISC West, hosted in collaboration with premier sponsor the Security Industry Association (SIA), unveiled its 2025 Keynote Series. Featuring a powerhouse lineup of experts in cybersecurity, retail security, and leadership, each keynote will offer invaluable insights into the challenges and opportunities transforming the field of security.

Parks Associates recently announced a new white paper, Consumer IoT Product Development: Managing Costs, Optimizing Revenues, which provides companies with a business-planning blueprint to evaluate how a consumer IoT solution will perform across its lifetime. Subscription services, such as video storage and professional monitoring, can be critical for covering ongoing cloud and support costs
HID, a worldwide provider in trusted identity solutions, today announced that MediaStorm, a leading media and content creation company in China, has adopted HID Mobile Access to offer employee badges in Apple Wallet, enabling employees to seamlessly access their office building’s corporate spaces with just their iPhone or Apple Watch. The initiative underscores MediaStorm’s mission to integrate leading-edge technology to support a modern and agile workplace that is flexible, secure and convenient, and this announcement makes them one of the first companies in China to implement employee badge in Apple Wallet.
NAPCO Access, a division of NAPCO Security Technologies and a leader in access control solutions since 1969, announces its new Unified Power Solution, developed in partnership with LifeSafety Power. This streamlined chassis integrates NAPCO Access Panel components and LifeSafety Power modules, delivering a space-saving, labor-efficient solution for professional security integrators.

To combat persistent retail crime and deliver peace of mind to workers in the bustling North Leroy Street business district, the City of Fenton Police Department has deployed a new AI-powered video surveillance system with camera-sharing technology to accelerate response time during retail heists or other emergencies.

During 2024, the Transportation Security Administration (TSA) intercepted a total of 6,678 firearms at airport security checkpoints, preventing them from getting into the secure areas of the airport and onboard aircraft. Approximately 94% of these firearms were loaded. This total is a minor decrease from the 6,737 firearms stopped in 2023. Throughout 2024, TSA managed its “Prepare, Pack, Declare” public awareness campaign to explain the steps for safely traveling with a firearm.
NAPCO Security Technologies, Inc., based in Amityville, NY, is proud to announce Peter Lowenstein’s promotion to head up sales for Napco Access, a newly unified group combining the company’s three access control divisions: Alarm Lock, Marks USA, and Napco Access Pro (formerly Continental).
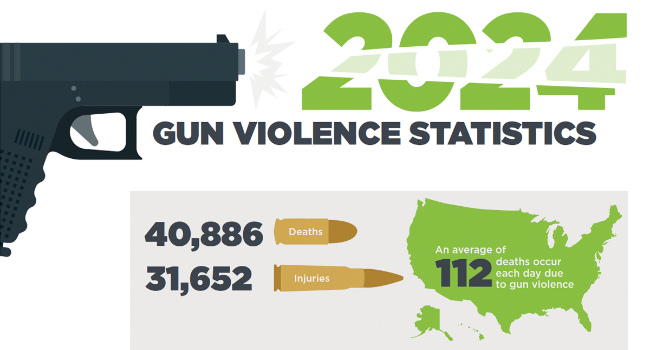
Omnilert, provider of gun detection technology, today released its compilation of Gun Violence Statistics for 2024 summarizing gun violence tragedies and their adverse effects on Americans and the economy. While research showed a decrease in overall deaths and injuries, the rising number of school shootings and fatalities and high number of mass shootings underscored the need to keep more people safe in schools as well as places of worship, healthcare, government, retail and commerce, finance and banking, hospitality and other public places.

A new survey from Pro-Vigil looks at video surveillance trends, how AI is impacting physical security, and more.

Axis Communications, provider of video surveillance and network devices, today announced the implementation of a custom surveillance solution developed in collaboration with the MetLife Stadium security team. This new, tailored solution will help the venue augment its security capabilities, providing high-quality video at unprecedented distances and allowing the security team to identify details from anywhere in the venue.
As the physical security industry looks toward 2025, i-PRO Co., Ltd. (formerly Panasonic Security) is highlighting four interlinked trends that are set to redefine how businesses, integrators, and security professionals approach security in the next year. These insights highlight the transformative role of edge computing, artificial intelligence (AI), the expansion of cloud computing, and how companies will integrate the wealth of available data.
As residential and commercial surveillance technology continues to advance, Snap One, now part of ADI, is evolving and investing in Luma by adding a new line of Luma 4K Hybrid cameras that deliver enhanced performance features and versatile designs.
Per Mar Security Services, a provider of total security solutions based in Davenport, Iowa, has acquired Accu-Com Security Solutions, an Oshkosh, Wisconsin-based company specializing in burglar, fire, video, and access control systems.
RapidFire Safety & Security (RapidFire), the multi-regional “Buy & Build” experts for fire, life safety, and security industries, announced the acquisition of Kane Fire Protection (Kane) in the St. Louis, Metropolitan area. The acquisition of Kane Fire Protection expands RapidFire’s service offerings with the addition of Kane’s fire sprinkler services. This represents RapidFire’s second acquisition in the St. Louis market, where they are also headquartered.
Mission 500, the security industry's nonprofit charity dedicated to supporting children in need across the US, Canada, and Puerto Rico, is pleased to announce several key updates to its Board of Directors. Jason Lutz, previously Treasurer, has been named Chair, succeeding Co-Chairs Tracy Larson and Janet Fenner. Board member John Nemerofsky is named Treasurer, and Garrett Savage, Secretary, succeeding Sarah Flanagan.