
Cybersecurity Awareness Month allows us to reflect on our progress in information security and the components that still need work. As the term “cybersecurity” has made its way into mainstream vernacular (not just in sci-fi movies but in everyday conversations in the workplace and home), it would be tough to argue that cybersecurity awareness hasn’t grown tremendously in the past few years.
- By Bill Bernard
- Oct 05, 2022
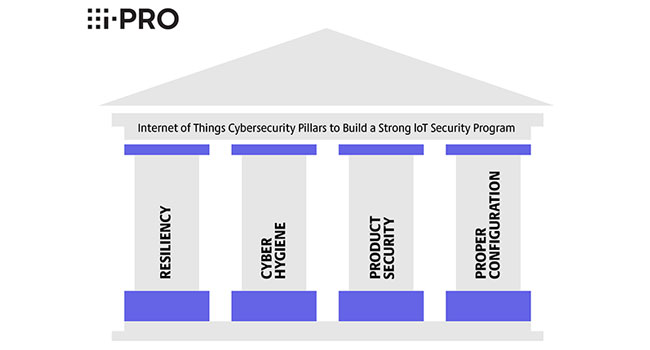
i-PRO Co., Ltd is proud to join with the Department of Homeland Security Cyber and Infrastructure Security Agency (DHS CISA) to raise awareness around cybersecurity for NCSAM (National Cyber Security Awareness Month).
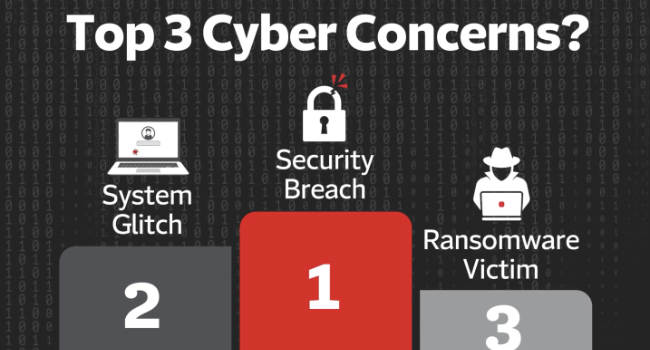
The Travelers Companies, Inc. recently released its 2022 Travelers Risk Index results, and for the third time in four years, the survey found that cyber threats were the top overall concern for business decision makers.
Commvault has announced the general availability of Metallic® ThreatWise™ an early warning system that proactively surfaces unknown and zero-day threats to minimize compromised data and business impact.
Versa Networks has announced that Gartner, a company that delivers actionable, objective insight to its executive and their teams, has given Versa Networks (Versa Operating System VOS™) the highest score for the Large Global WAN Use Case, as published in the 2022 Gartner Critical Capabilities for SD-WAN report.

We hear the term “best practices” a lot, but the truth is, there are still plenty of bad practices in use that put people and assets at risk every day. Many of those bad practices are grounded in one or more of the following myths that commonly lure people and organizations into a false sense of security.
- By Will Knehr
- Sep 19, 2022

Today’s businesses have seen increasing pressure to digitize their services, but few industries have felt this pressure more than the financial sector. Customers have grown to demand high-quality digital services, and the expectation is that these services are delivered with a high degree of security and reliability.
- By Kelly Ahuja
- Sep 09, 2022

Staring up into the sky on a clear night, you may be inclined to think that the small shining light moving gently across the black background is a shooting star or perhaps even a UFO. More likely, that tiny speck of light moving over your head is a satellite orbiting thousands of miles above the clouds
- By Patrick Shore
- Sep 09, 2022

The National Counterintelligence and Security Center (NCSC), the National Insider Threat Task Force (NITTF), the Office of the Under Secretary of Defense Intelligence and Security, the Defense Counterintelligence and Security Agency, and the Department of Homeland Security today launched the fourth-annual “National Insider Threat Awareness Month” (NITAM).

Amid increasing geopolitical tensions and consumer privacy concerns, business leaders (40%) ranked cybersecurity as the number one serious risk facing their companies. It’s not just top of mind for Chief Information Security Officers and Chief Risk Officers—executives across the entire C-suite ranked cybersecurity as a serious risk

Venafi, provider of machine identity management, today announced the findings of new research that evaluates the security impact of the increasing number of nation-state attacks and recent shifts in geopolitics. Venafi research into the methods used by nation-state threat actors shows the use of machine identities is growing in state-sponsored cyberattacks.

Proofpoint, Inc., a cybersecurity and compliance company, announced the release of its latest study, Cloud and Web Security Challenges in 2022, in collaboration with The Cloud Security Alliance (CSA).
The topic of zero-day exploits and exposed vulnerabilities is always trending within cybercriminal communities, both on clear web platforms and on the underground. From 280-character tweets circulated among cybercriminals on Twitter, to POC exploits released on clear web code repositories, to exploit kits and tools shared across the forums and markets of the deep and dark web, threat actor discourse revealing which vulnerabilities they plan to target is far from scarce.
- By Michael Angelo Zummo
- Aug 10, 2022

(ISC)² – the world’s largest nonprofit association of certified cybersecurity professionals – recently announced the (ISC)² One Million Certified in Cybersecurity℠ program, pledging to put one million people through its foundational Certified in Cybersecurity entry-level certification exam and education program for free.

IBM Security recently released the annual Cost of a Data Breach Report, revealing costlier and higher-impact data breaches than ever before, with the global average cost of a data breach reaching an all-time high of $4.35 million for studied organizations.

The potential of a cyberattack is one of the most significant threats to businesses across all industries. The increasing sophistication and complexity of these attacks can often go unnoticed, causing widespread damages and disruptions internally and externally to any of its vendors or partners.

The business of cybercrime is rapidly increasing in scope and scale. The cost incurred by companies due to data breaches increased by nearly 10 percent from 2020 to 2021, meaning if the cost incurred by attacks was measured against the GDPs of all the nations of the world, it would be third largest, just lagging behind the U.S. and China.
- By David Ratner
- Jul 30, 2022

Fewer than 30% of small businesses in the United States view cybersecurity as a priority to invest in, according to data from Tech.co. This is despite a staggering 62% of small US businesses suggesting security breaches are a significant threat to their business growth.

A global IT security and compliance survey of 800+ IT professionals found that the rate of IT security incidents increases the more Microsoft 365 security features are used. Organizations using Microsoft 365 and that use 1 or 2 of its stock security features reported attacks 24.4% and 28.2% of the time respectively, while those that use 6 or 7 features reported attacks 55.6% and 40.8% of the time respectively.

It’s no secret that cyberattacks and data breaches are on the rise. You’ve likely heard about it on the news or may have experienced it first-hand. A commonality between these attacks becoming easier and more frequent might surprise you—simple passwords.
- By Dan DeMichele
- Jul 06, 2022