
How to Prevent Breaches, Not Just Clean Up the Mess
- By Steven Minsky
- Apr 10, 2017
As a provider of storage for video surveillance systems, the hardest part of my job is educating end-users, integrators and consultants on the best way to purchase storage for their systems.
- By Scott Seraboff
- Apr 01, 2017
The thought of a network or individual cameras getting hacked brought cybersecurity into the security picture pretty quickly. Cyber questions also arise when discussing cameras being manufactured in China.
- By Ralph C. Jensen
- Apr 01, 2017

The live webpage will frequently update with content from the show floor.
- By Matt Holden
- Mar 23, 2017

Regardless of term, or use case, it’s well-known that cybercriminals can hack into any vulnerable device connected to the internet to remotely take control of that device and enslave it into a botnet that is part of a distributed denial-of-service (DDoS) attack.
- By Stephanie Weagle
- Mar 22, 2017

Over the weekend, Saks Fifth Ave reported that customers’ data may be exposed.

In a hearing with the Intelligence Committee, FBI Director James Comey said there was no evidence to support President Trump’s tweets claiming Trump Tower was wiretapped by former President Obama.

We have failed to focus on what’s most important: building security in.
- By Peter Hesse
- Mar 20, 2017

Samsung will finally offer monthly security updates.

The predicted increase in online fraud in the U.S. has arrived with the adoption of chip card technology.
- By Michael Lynch
- Mar 16, 2017

Four people, including two officers from Russian security services, were charged by the U.S. in the massive data breach that plagued Yahoo.
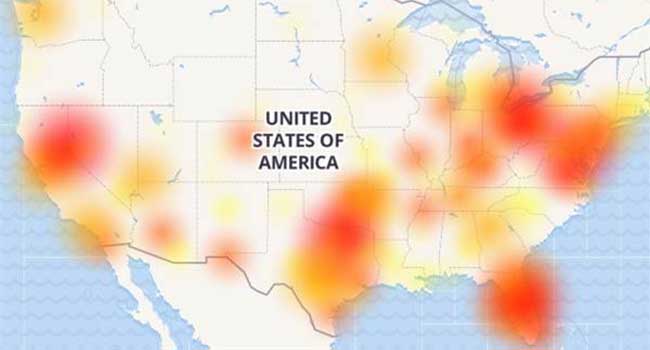
Users of AT&T’s wireless network found themselves without the ability to call 911 last night.

Today as the cybersecurity landscape continues to evolve at breakneck speed, so do the threats, and the amount of data we have sitting with the different organizations we deal with is growing each day.
- By Brett Hansen
- Mar 09, 2017
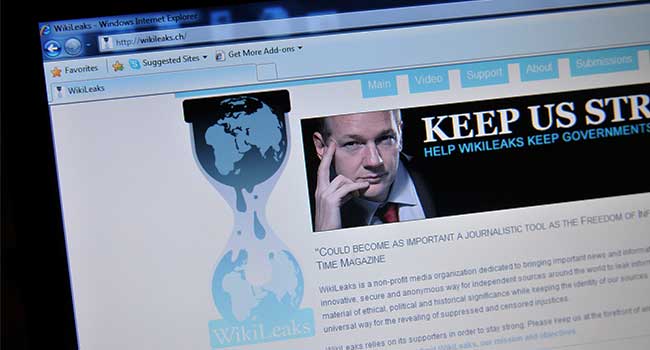
WikiLeaks released thousands of documents that it said described hacking methods of the CIA.

Milestone Systems is the number one VMS worldwide, but they are searching for more.

Software bug at an internet-service provider sparks privacy and security concerns.

Local, federal, state and private security officials are teaming up to create a security stronghold that protects a three mile area around the stadium.

Earlier in 2016, when Gartner analysts stated that by 2020, 80 percent of all software will be offered on a subscription basis—this did not come as surprise to us at Genetec.
- By Christian Morin
- Feb 01, 2017
Financial institutions have been historically slow to adopt IP video surveillance citing concerns about possibly compromising network security.
- By Stephen Joseph
- Feb 01, 2017
Security threats are on the rise and as IT security teams increase their scrutiny of all network-connected devices, it’s time for some new thinking about the design and maintenance of building security systems.
- By John Szczygiel
- Feb 01, 2017