
Passengers on the Santiago Metro system can travel more safely to their destinations due to a new security monitoring system from IndigoVision. More than two million passengers a day travel on the Santiago metro, the backbone of the Chilean capital’s public transport system.
In a series of blog posts, Unisys Corporation announced offering its enterprise technology predictions for 2012. Based on its work with clients around the world, Unisys expects that disruptive technologies cloud computing, mobility, social computing, big data and smart analytics, IT appliances, and cybersecurity will become more tightly woven into mission-critical systems and processes as organizations look for ways to innovate and operate more cost efficiently
Sandia National Laboratories computer scientist Casey Deccio has developed a visualization tool known as DNSViz to help network administrators within the federal government and global IT community better understand Domain Name System Security (DNSSEC) and to help them troubleshoot problems.

Navarre Corp., a distribution and retail support operation in Minneapolis, previously relied on an analog-based surveillance system as a way to increase security and aid in investigations, but the company found the system unreliable for capturing high-quality video when incidents occurred.
- By Peter Jankowski
- Dec 01, 2011
Instead of current authentication systems that force humans to adapt to computers, consider computers that adapt to the humans that built them in the first place.
University of Alabama at Birmingham researchers helped the Federal Bureau of Investigation and NASA Office of Inspector General identify seven foreign nationals arrested for a massive, sophisticated Internet fraud that infected more than 400 million computers in 100-plus countries and scammed $14 million.
For many businesses, maintaining a competitive edge requires a collaborative line of communication, but sharing highly sensitive documents without the proper security can be dangerous if the information falls into the wrong hands
- By Adi Ruppin
- Oct 14, 2011
Organizations of all sizes are migrating from analog to IP-based physical access control solutions, drawn by increased security, increased operational efficiency and better availability.
- By Dan O’Malley
- Oct 01, 2011
Over the last decade, the alarm industry has spent millions of dollars and thousands of hours addressing the issue of preventing unnecessary police dispatches from alarm systems.
- By Stan Martin
- Oct 01, 2011

To help comply with industry regulations, boost security and improve operational efficiencies, Associated British Ports (ABP) needed a flexible HD surveillance system that could easily integrate with the port operator’s existing analog system.
- By Keith Marett
- Oct 01, 2011

In this autumnal month of witchery, trickery, and general tom-ghoulery, there comes a Halloween-worthy tale disturbing enough to haunt the mind of any business owner or information technology professional.
- By Ronnie Rittenberry
- Oct 01, 2011
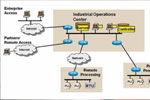
Industrial security has always been a challenge, with often vast areas needing coverage that is effective—and efficient. As with many other technologies, advances in electronic security and surveillance, both physical and cyber, have created new challenges as they have addressed and conquered earlier problems.
- By Jim Krachenfels
- Sep 01, 2011

A group of Microsoft researchers announced recently that they had cracked a version of the Advanced Encryption Standard (AES), the world’s toughest encryption mechanism.
- By Laura Williams
- Aug 29, 2011
A report forecasts that the EV cybersecurity market will increase from just $26 million in 2011 to $144 million by 2015, with a cumulative investment of $432 million during that period.
The Security Products New Product of the Year Award honors the outstanding product development achievements of security equipment manufacturers whose products are considered to be particularly noteworthy in their ability to improve security.
Juniper Networks recently released a report on the impact of data center consolidation on the Federal government.
While the world is distracted with the continuing reports of phone hacking practices and other corporate data breaches,a new survey reveals that hundreds of organizations are now vulnerable to internal threats.
Clerity Solutions, a full-service provider of migration, modernization and optimization solutions, recently introduced Clerity Healthcare, a business unit of the company that provides turnkey hardware and software solutions, as well as specialized consulting services, for the healthcare market.
For the past three years, Alloin, a member of the Kuehne + Nagel Group, has been using an array of ultra-high resolution cameras to provide anti-intruder protection for 33 courier depots as well as monitoring the smooth flow of pallets and packages.
Exercising its large-scale security integration capabilities, Diebold, Inc. is managing the installation, integration and maintenance of a complex security software system for the new World Trade Center (WTC) site in New York City.