
Yahoo officials made a statement regarding a bug that was discovered by hackers looking to exploit the system.
- By Matt Holden
- Oct 07, 2014
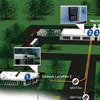
The objective: to create an additional network throughout the park as a back up to aging fiber network.

A test version of the government’s health insurance site was hacked.
- By Matt Holden
- Sep 08, 2014
With the introduction of IP cameras, system integrators have experienced big improvements in the quality and performance of video systems that can be offered to their customers.
- By Richard L. Malstrom
- Sep 01, 2014
Jane and Jake work for the same company. This week they’re on one of those dreaded road trips—three cities in four days—and are, as we all are, completely dependent on their tools of choice while on the move.
- By Scott Goldman, Robert Foster
- Aug 01, 2014
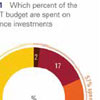
Compliance with increasingly stringent regulations for organizations providing outsourced IT services, particularly in regards to data protection, is becoming more difficult.
- By Gábor Marosvári
- Aug 01, 2014

Distributed Denial of Service (DDoS) attacks are some of the oldest Internet threats and continue to be the top risk to networks around the world.
- By Mark Byers
- Aug 01, 2014

While businesses will spend thousands of dollars on cameras and recording systems, alarms, intrusion detection, emergency communication and theft prevention, many overlook the need for systems’ power protection.
- By Samantha Wade
- Aug 01, 2014

Here is a list to help develop an all-star team of employees that will protect your information.
- By Matt Holden
- Jul 28, 2014

6 steps on predicting the future of your network's security: process, enhance, cross-correlate, baseline and analyze information.
- By Benjamin Powell
- Jul 14, 2014

Throughout Mexico, residents trust Presta Prenda de Banco Azteca for short-term, secured loans on jewelry, electronics and other valuables. Much like the pawn shop business model in the United States, Presta Prenda customers obtain immediate cash with various repayment options.
- By Mig Paredes
- Jun 30, 2014
When a successful European toy manufacturer outgrew its facilities, it built a new, three-facility campus that included an office along with manufacturing and warehouse space.
- By Susan Stanley
- Jun 01, 2014

Ensuring the safety and security of patients and employees is critical to healthcare organizations of any size. For larger facilities, the task can seem monumental, leading many in the industry to turn to IP network surveillance technology to help take control of the process.
- By Greg Peratt
- May 01, 2014

Philosophical and physical shifts in intelligence and management at the edge are remaking corporate networks.
- By Vince Ricco
- May 01, 2014

“Banks Heap Suits on Target over Breach,” read a recent headline of a Wall Street Journal story. By that time, seven financial institutions had already filed class action suits against the retail giant alleging it did not sufficiently protect its customer’s data.
- By David Rizzo
- May 01, 2014
When most people consider cybersecurity, they think about protecting the information that resides on their computers—sensitive emails, folders or files.
- By Mauricio Chacon
- May 01, 2014

Datacenter traffic is predicted to triple by 2017 with the cloud as the biggest traffic source, according to a recent Cisco Global Cloud Index study.
- By Charles P. Williams
- May 01, 2014

Wireless transmission is usually a topic that raises many concerns in the security world. It seems common knowledge nowadays that a wireless network can be easily hacked, and private information can end up on the Internet or someone’s identity can be stolen.
- By Cosimo Malesci
- Apr 01, 2014

When properly constructed, a cloud infrastructure can offer greater security than a legacy system; however, when poorly constructed, a cloud-based infrastructure introduces risk across the enterprise.
- By Sumeet Sabharwal
- Apr 01, 2014

Atchison Frazer, CMO for KEMP Technologies, talks hackers and other security attacks being a source of server downtime and how you can use ADCs to protect your network(s.)
- By Atchison Frazer
- Mar 05, 2014