It is amazing that the year of convergence from analog to IP was supposed to be 2008 but it was not until 2012 that IP-cameras started to outsell analog cameras. We sure have come a long way from those analog-oriented days.
- By Jay Jason Bartlett
- Feb 01, 2021
The explosion of IoT devices in today’s technology landscape makes a perfect storm for attackers to exploit.
- By Wayne Dorris
- Feb 01, 2021
Interface Security Systems has announced that it has entered into a strategic partnership with Ignite Prism, a developer of cloud-based business intelligence solutions. As part of this partnership, Interface will have exclusive rights to Ignite Prism’s video analytics technology in North America.

On March 25, before the full impact of coronavirus hit home and the world was still full of hope, Google News showed an eye-wateringly appealing headline: Cybercrime Gangs Promise to Stop Attacks on Healthcare Organizations During the COVID-19 Crisis.
- By Kevin Deierling
- Dec 07, 2020

COVID-19 has been with us long enough that organizations are acknowledging that home and office will combine to create the new workplace. Commonly referred to as the “Hybrid Workplace,” the expectation is that while employees may work predominantly in one place or another, over time, both the remote and office locations will play a role in enabling a productive, engaged workforce.
- By Larry Lunetta
- Dec 07, 2020

The video cameras and sensors your business has invested in provide you with the protection you need to be safe as well as the information you need to keep operations running smoothly.
- By Ralph C. Jensen
- Dec 02, 2020

The holiday shopping season is here, let’s not forget that we are in COVID-19 pandemic and health officials continue to repeat their messages about the importance of masks, adequate social distancing, and frequent handwashing.
- By Patrick V. Fiel
- Dec 01, 2020

As the Internet of Things (IoT) becomes mainstream, companies are delving into the ramifications of adoption, including its benefits, challenges, and opportunities--not least, the implications to security and cybersecurity.
- By Steven Turney
- Jul 30, 2020

Prior to the COVID-19 pandemic, the rate of cloud adoption was growing steadily. Since March, however, when “shelter-in-place” orders began sweeping the nation, we’ve seen cloud computing usage skyrocket.
- By Joe Vadakkan
- Jul 30, 2020
BriefCam has announced a significant new capability to its product portfolio with v5.6.1 of its innovative and extensible video content analytics platform.

In this pandemic of coronavirus, all organizations have shifted from office work to remote work. By saying that, you must have heard about VPNs, and how they improve security and privacy.
- By Susan Alexandra
- Jun 02, 2020

Artificial intelligence has been in the headlines a lot recently. It will help save mankind or usher in the robot apocalypse, depending on which article you read.
- By Dave Mayne
- Apr 09, 2020
Development and deployment of container-based software has become a popular movement in technology.
- By Ambuj Kumar
- Mar 01, 2020
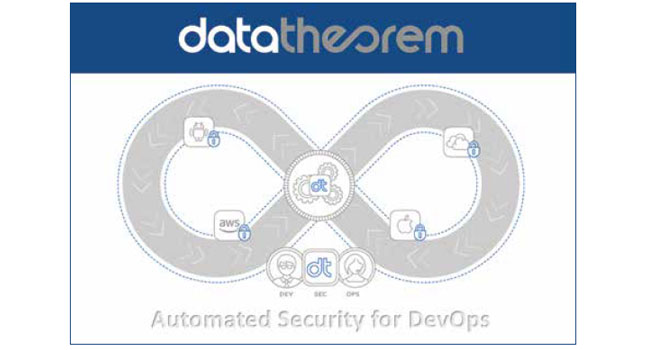
Not only does modern software architecture create a broader attack surface area, the accelerated DevOps methodology makes it harder to detect and remediate vulnerabilities.
- By Felicia Haggarty
- Dec 01, 2019
This evolution not only keeps the IT department in a constant state of change, but also dramatically changes the way the overall business must adapt to stay competitive.
- By Jorge Del Prado Lera
- Dec 01, 2019
Recent hacks into databases of some of the world’s biggest corporations and government organizations put the personal information of billions of people at risk.
- By Mohammed Murad
- Oct 01, 2019

Cloud storage is most used by small-and-medium businesses (SMBs). The reason is that it comes with many benefits for organizations in terms of flexibility and more importantly productivity.
- By François Amigorena
- Oct 01, 2019

Two of the biggest trends today, particularly in the security surveillance and IoT realms, are border security and the emergence of local governments transforming their communities into smart cities.
- By Kevin Taylor
- Oct 01, 2019

Privacy issues continue to dominate headlines as the world’s biggest companies are being challenged on the ways they collect and use people’s data. Consumers are growing more concerned about how their activities are being tracked across the web as companies sell information to advertisers for a profit.
- By Neil Huntingdon
- Oct 01, 2019

In today’s world, there are a myriad of different manufacturers that produce similar products and there are so many options available to customers.
- By Michael Stoll
- Oct 01, 2019