The transition is the culmination of the September 2016 merger

After the summer rush, TSA may change up their security procedures.
Full and Half Day Sessions Scheduled in More than 25 Cities

The Cubs plan to spend $1 million on security cameras near Wrigley Field.

While there is no credible or specific threat to the United States at this time, police will increase security at popular tourist spots and arenas.
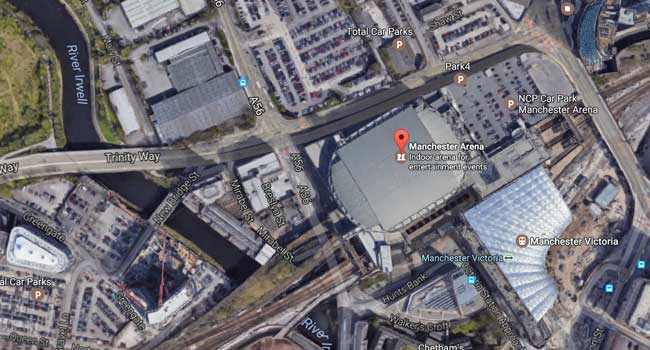
Concert-goers have slammed “lax security” at the Ariana Grande show that was targeted this week in a terrorist attack
KeyWatcher Touch Hardware and TrueTouch Software Add Network Convenience
Introduces Port Guardian Physical Port Lockout
FLIR Systems, Inc. (NASDAQ: FLIR) today announced that James J. (“Jim”) Cannon has been appointed President and Chief Executive Officer, effective June 19, 2017.

An explosion at Manchester’s popular arena after an Ariana Grande concert killed 22 people and injured more than 50 others.
Total Recall Corporation will showcase its video surveillance and citywide safety solutions at ASIS NYC Security Conference and Expo.
Audio company is available in MegaLab
Value-added distributor to sell Razberi video surveillance appliances to resellers in North America

An explosion happened in a waiting room inside a military hospital in the Thai capital.

The city of New Orleans will take down a prominent statue of Confederate Gen. Robert E. Lee.
SALTO Systems will showcase its latest products and a new showroom at the 27th annual ASIS NYC Security Conference and Expo next month.

At least 19 people were injured and one was killed when a vehicle crashed through pedestrians at Times Square in New York City.