Strategies To Safeguard Data
Industrial networks see advances in security and surveillance
- By Jim Krachenfels
- Sep 01, 2011
Industrial security has always been a challenge, with often vast areas needing coverage that is effective—and efficient. As with many other technologies, advances in electronic security and surveillance, both physical and cyber, have created new challenges as they have addressed and conquered earlier problems.
IP networks fall into this pattern: They increase protection but also trigger new security challenges. The huge quantity of sensitive data moving across large network “pipes” provides a target for cyber attack, from inside or outside the facility, that adds an additional layer of complexity to surveillance and security strategies.
With the recent proliferation of such cyber threats, it has become increasingly clear that no business or industry is completely safe from attacks. The Ponemon Institute released a survey in June of almost 600 U.S. IT and IT security practitioners that provided some sobering statistics:
- 90 percent of organizations surveyed have had at least one breach.
- 59 percent say they have had two or more breaches in the past year.
- 48 percent of respondents identified complexity as one of their biggest challenges to improving network security, with the same percentage citing resource constraints.
- 75 percent believe their effectiveness would increase by developing end-to-end solutions.
Integrated Networks and Multiple Layers of Defense
Digital access control devices have dramatically increased the effectiveness of access control strategies. Today, sophisticated scanners of irises, fingerprints or other identifying biometrics can instantly authenticate a person by matching his or her information with data in a server running Radius or another type of authentication application. New data can be updated within seconds.
In the IP age, many organizations are finding it effective to allow security and surveillance data to coexist on the same network as other operational and nonoperational data. Fiber solutions offer high-bandwidth, low-cost sharing of data transport inside a single facility, throughout a campus or even across town to a corporate data processing center. Integrated data transport and management reduce both hardware and staff costs, but they also add challenges.
Distributed networks, where data is entered, acted upon and/or transported from various locations in the network, hold new potential for those looking to breach security perimeters, both the old-fashioned physical kind and the new cybersecurity perimeters. Defense-in-depth, as it applies to IP networks, is an adaptation of a military strategy: Use a layered defense that provides multiple and varied defense strategies against any attack vector rather than relying on a single line of defense.
A strategic defense of an industrial site will include measures designed to protect and support both physical security data and other data that coexist in the same physical network infrastructure.
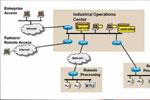
General Industrial Network Topology
Here is a simplified look at a general-purpose industrial network, where the key network components include:
- Main industrial campus and/or facility control center;
- One or more remote locations;
- Enterprise access portal;
- Partners and remote access portal; and
- Multiple public and private transit networks, including the intranet and Internet.
With multiple access points and multiple network hops—private and public— the following rundown illustrates a network that is wide-open to abuse from cyber or physical attacks.
Firewalls are a first line of defense, and they are usually an option on network routers. Typically located at the entry points to the core network and to all remote facilities, a firewall acts as a gate would, ensuring that nothing private goes out and nothing malicious comes in. Its value is in its ability to regulate the flow of traffic between computer networks of different trust levels, such as the Internet, an internal network and possibly a perimeter network. Thus, it inspects network traffic passing through and denies or permits passage based on a set of rules. Modern firewalls target packet information for Layers 3 and 4 (transport and link layer), providing an additional level of security by examining the state of the connection as well as the packet itself.
Virtual Private Networks (VPNs) make sure that the connections going outside of the firewall are protected. Non-secure VPNs are used to transport, prioritize and allocate bandwidth for various customers over a multi-purpose transport network, while secure VPNs should be used whenever control messaging, protection messaging, configuration sessions, SCADA traffic or other sensitive data will traverse networks where security could be compromised. VPN sessions are tunneled across the transport network in an encapsulated, typically encrypted and secure format, making them “invisible” for all practical purposes. This creates a secure path between two devices or applications or establishes a secure tunnel between two locations that can be used by many devices or end points.
Virtual LANs make it possible to segregate the different traffic flows—such as VoIP, video, management and control applications—into separate broadcast/multicast domains. If one of the applications is compromised, the VLANs keep the other applications isolated and safe.
Secure Access Management systems protect the network and sub-systems by enforcing “Triple-A” security (authentication, authorization and accounting). Only specifically authorized users are able to access the control system components or other network devices electronically. A SAM also logs all actions or changes that are made for later retrieval and analysis and circumvents “insider attacks” by enforcing security policies. While insider attacks can be malicious, they are often simply careless acts carried out by employees just trying to get their jobs done.
Any user trying to connect to a system is transparently connected to an access management system (AMS) server. An AMS server obtains credentials from the end user and then can interrogate other security systems—such as Microsoft’s Active Directory or twofactor authentication systems, such as RSA SecurID servers—as well as its own profile data base. It authenticates users for both system access and access to specific target devices.
Centralized Logging and Auditing require that all network components be able to enter comprehensive logging and reporting information into a common repository. Recording and tracking “when, where and what” in a central system supports real-time detection and correlation of security threats. When something looks wrong, the information is immediately transmitted as an alert for immediate action. The information is also useful for detecting incident trends. Protocols such as SNMP, SNTP for time synchronization and Syslog provide simple tools to support forensic research.
Secure Network Management is another aspect of securing the network. It will ensure that the networking components themselves are secure: Each network element must implement secure management interfaces requiring rigorous authentication/authorization, as well as both local logging and remote event notification. Many of the traditional access methods, such as HTTP and TELNET, have open security and passwords in plain text. These should be replaced by more-secure methods, such as SSH/SSL(HTTPS) for console access, SNMPv3, secure FTP and Syslog remote logging.
The Secure Data Network is a secure network topology that significantly reduces the risk of physical or cyber attacks, and looks much like this:
Defense-in-Depth in Action
Each industrial facility will address its own needs in its own way, and most agree that implementing a cybersecurity program with defense-in-depth is an incremental process.
In the following example, a rural electric power cooperative, “Ridgemont Utility,” underwent a security audit several years ago that convinced its administrators it was time to take security more seriously.
Ridgemont used outside security experts as well as internal teams to develop the solution. Dedicated experts provided a level of sophistication and expertise often not possible for internal employees, who often view security as only part of their job.
The utility chose to develop and maintain separate networks for corporate and SCADA, to limit the effect an incursion in one network would have on the other.
Firewalls, with hot-standby firewalls for failover protection, guard gateways between networks, and they are backed by redundant switching behind firewalls and redundant links. VLANs, which use VPNs between firewalls for double protection and use different logical and physical networks for different functionalities, make it difficult for intruders to penetrate the system. Authorized users, though, can move easily among networks to get what they need.
Ridgemont uses serial tunneling devices to run serial SCADA operations through the network, using routers designed to provide integrated support for serial and IP. The utility also defaults to blocked ports, unblocking a port only after it has been connected to a new piece of equipment. To foil intruders, Ridgemont also changes default port numbers to make it more difficult to gain unauthorized access.
Ridgemont has defined policies that determine which users will have access to which network, and to which specific resources on that network. When outside access to a network is necessary, it passes through a connection using SSL and both per-port and per-user authorization. The authentication process uses a local active directory rather than a central one. It also implements password protection with a different, randomly generated password for each piece of equipment that can be protected.
With thousands of pieces of equipment within the system, password management is difficult but deemed essential. IP addresses are removed from equipment to protect the network in case of physical breach.
A Syslog server and SNMP management allow Ridgemont to track not only who is logging into the IP-based equipment, but when the logon occurred and what was changed.
WiFi access is isolated on a separate network that links directly to the cable company and is offered only as a convenience for outside visitors. Internally, employees access the Internet through VPN appliances using SSL. Ridgemont also ensures that employees keep firmware and software up to date and have deployed the latest security patches.
Security Matters
The clock is ticking. It is practically a matter of when, not if, a physical or cyber attack will occur in any industrial facility.
Fortunately, there are off-the-shelf, industrial-strength networking equipment and cost-effective tools and systems available for deploying defensein- depth protection for any type of industrial network.
Industrial security is not a onetime goal but a continual process of assessing network vulnerabilities, updating security policies and adding emerging technologies in a continual cycle in order to protect valuable cyber and physical assets.
This article originally appeared in the September 2011 issue of Security Today.