First Ponemon Study on Big Data Analytics in Cyber Defense is a National Wake Up Call
A study from a cyber security analyst firm, entitled “Big Data Analytics in Cyber Defense,” confirms that big data analytics offer a powerful arsenal for cyber security, but adoption is alarmingly slow. The report, released today by Teradata Corporation and the Ponemon Institute, contains several key findings:
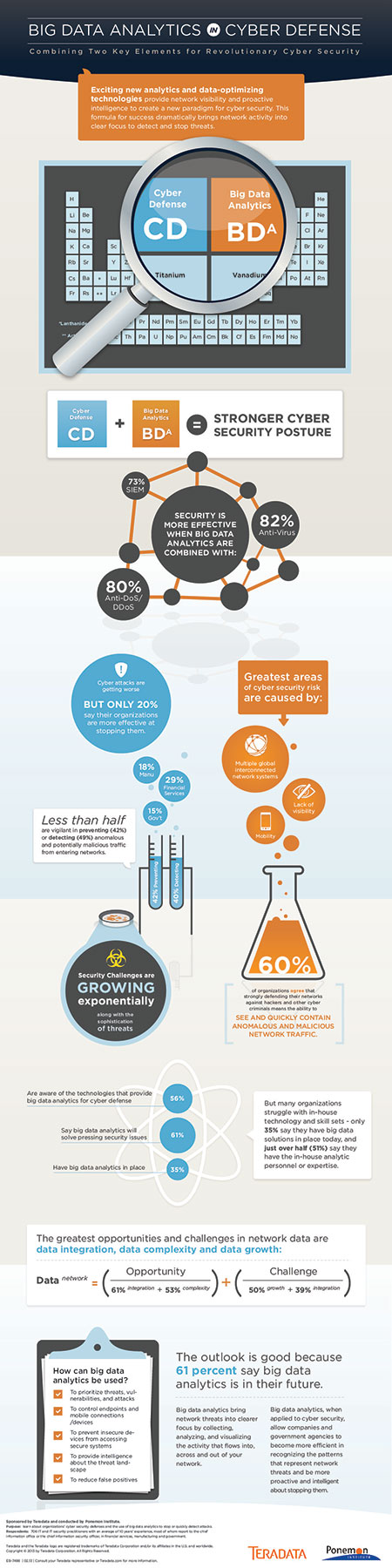
- Cyber-attacks are getting worse but only 20 percent say their organizations are more effective at stopping them. The greatest areas of cyber security risk are caused by mobility, lack of visibility and multiple, global, interconnected, network systems.
- 56 percent are aware of the technologies that provide big data analytics and 61 percent say they will solve pressing security issues.
- Less than half of organizations are vigilant in preventing (42 percent) anomalous and potentially malicious traffic from entering networks or detecting such traffic (49 percent) in their networks.
- Big data analytics, with security technologies, ensure a stronger, cyber defense. 82 percent would like big data analytics combined with anti-virus/anti-malware; 80 percent say anti-DoS/DDoS would make their organizations more secure.
“While data growth and complexity are explosive factors in cyber defense, new big data tools and data management techniques are emerging that can efficiently handle the volume and complexity of IP network data,” said Larry Ponemon, chairman and founder of the Ponemon Institute, a research “think tank” dedicated to advancing privacy and data protection practices. “These new, database analytic tools can bring more power and precision to an enterprise, cyber-defense strategy, and will help organizations rise to meet the demands of complex, large-scale analytic and data environments.”

Today’s IT security practitioners consider network data to present both an opportunity (data integration 61%, data complexity 53%) and a challenge (data growth 50%, data integration 39%). While many organizations struggle with in-house technology and skill sets, only 35% say they have big data solutions in place today, and just over half (51%) say they have the in-house analytic personnel or expertise, the study showed.
Big data analytics can bridge the existing gap between technology and people in cyber defense through big data tools and techniques which capture, process and refine network activity data and apply algorithms for near-real-time review of every network node. A benefit of big data analytics in cyber defense is the ability to more easily recognize patterns of activity that represent network threats for faster response to anomalous activity.
“The Ponemon study is a wakeup call,” said Sam Harris, director of enterprise risk management for Teradata. “Enterprises must act immediately to add big data capabilities to their cyber-defense programs to close the gap between intrusion, detection, compromise and containment. When multi-structured data from many sources is exploited, organizations gain a very effective weapon against cyber-crimes.”
Harris said that in the cyber security realm, effective defense means managing and analyzing unimaginable volumes of network transaction data in near-real-time. “Many security teams have realized that it is no small feat to quickly sift through all of their network data to identify the 0.1 percent of data indicating anomalous behavior and potential network threats. Cyber security and network visibility have become a big data problem. Organizations entrusted with personal, sensitive and consequential data need to effectively augment their security systems now, or they are putting their companies, clients, customers and citizens at risk.”
The Ponemon Institute surveyed more than 700 Information Technologists (IT) and IT security practitioners across the United States about the new data management and analytic technologies available to help organizations become more proactive and intelligent about detecting and stopping cyber threats. The study covered experts with an average of 10 years of experience in the financial services, manufacturing and government industries. All respondents were familiar with their organization’s defense against cyber security attacks and have some level of responsibility for managing the cyber security activities within their organization.
To access, read, and share the study please visit: http://www.teradata.com/cybersecurity-threat/.
Infographic revealing survey's big data and cyber security results: