
Twitters Two Factor Authentication How To and Why You Should
- By Ginger Hill
- May 28, 2013
I’m sure by now you’ve heard all about Twitter introducing two-factor authentication, making it more difficult for hackers to hijack user accounts. Kudos to Twitter for that, since Syrian hackers recently hijacked The Associated Press and The Financial Times’ Twitter accounts; oh and don’t forget the break-ins of Jeep and Burger King’s accounts, too.
What exactly does this authentication do?
Two-factor authentication sends users a one-time, log-in code via a text message, so hackers are left trying to figure out not only the main password chosen, but the text message code as well, in order to successfully hack a Twitter account.
According to Mark Bower, data security expert and VP at Voltage Security, “Twitter’s move is a good one [even though] the combination of strong authentication and data-centric security is where the industry has to head to fend off the new wave of sophisticated attacks.”
“Twitter is part of the social fabric and is a hot target for malware propagation to millions of unwitting recipients. Compromised Twitter accounts are ideal to deliver malware-laced links, drop trojans and initiate data theft – potentially stealing from behind corporate firewalls and even from smartphones,” Bower continued.
So, have you set yours up yet? No!? Well, here’s how:
1. Log into your Twitter account.
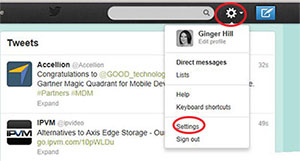
2. Go to settings.
3. Select “Require a verification code when I sign in.”
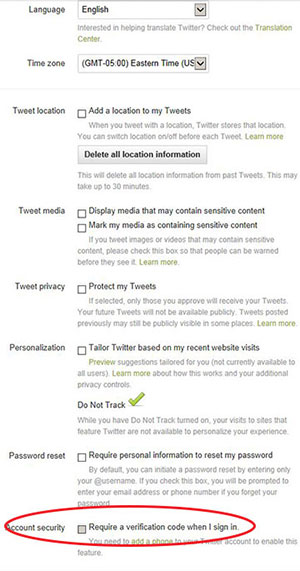
4. Confirm your email and phone number.
And, that’s it! Now, when you sign into Twitter on an unknown device or new app, you will receive a SMS with a six-digit code. Simply enter that code into your new device or app and let the tweeting begin…safely!
About the Author
Ginger Hill is Group Social Media Manager.