The second quarter statistics on cargo theft in 2014 (Q2-14) are in from the Supply Chain- Information Sharing and Analysis Center (SC-ISAC). For those unfamiliar, SC-ISAC is a liaison for information sharing between Department of Homeland Security (DHS) and the nation’s supply chain. DHS identified Transportation Systems as one of sixteen critical infrastructures to the nation’s supply chain, and cargo theft as a constant threat to stability.
Turnaround
A decrease in reported cargo theft continues! While SC-ISAC’s 140 reported incidents this quarter are up from the first, the sum total is materially down from the 194 reported Q2 of 2013. Freightwatch numbers for the same quarter are higher at 185 incidents, but still represent a slight dip from 2013. (Note: Some companies report to both SC-ISAC and Freightwatch; some only one or the other; others report to neither.)
Which States?
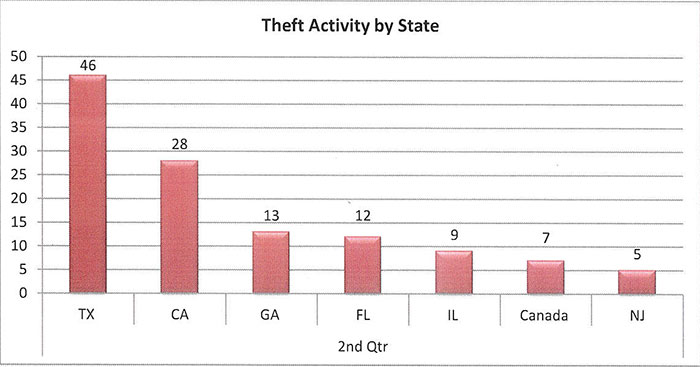
Texas continues, unfortunately, to lead the nation in cargo thefts for the third quarter in a row. California, Georgia, Illinois, Florida and NJ continue their normally high levels of activity.
For the first time, SC-ISAC includes a breakdown of cities known to be hot spots, in this quarter Dallas, the LA Basin, Atlanta, Chicago and Miami.
Where?
Truck stops and yards continue to lead the rankings with yards taking the top spot in the second quarter. Freightwatch’s analysis delved even further into this issue and produced an alarming statistic: Facility burglary increased in this quarter by 100% as compared to the second quarter of 2013, and 67% as compared to the first quarter this year.
When?
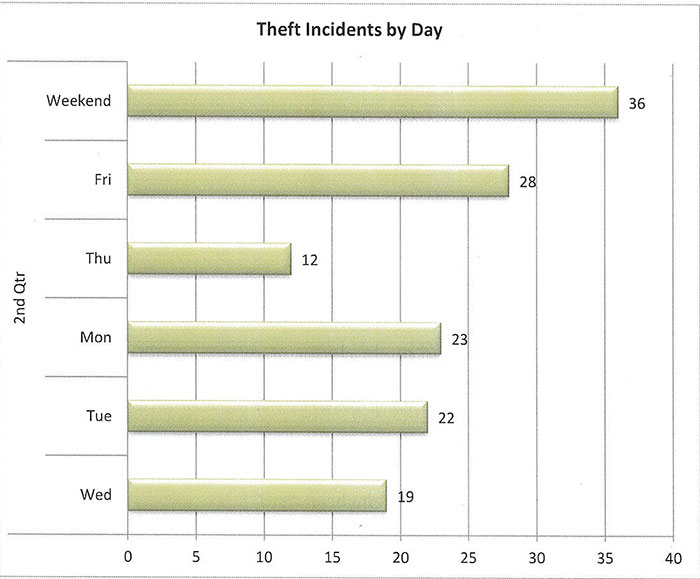
Cargo theft consistently spikes over weekends. This quarter, 63% of all cargo theft occurred over the weekend, down slightly from the 73% reported in 1st Qtr. Still, it’s overwhelmingly clear that weekends are when cargo is at its greatest risk.
What Are They Stealing?
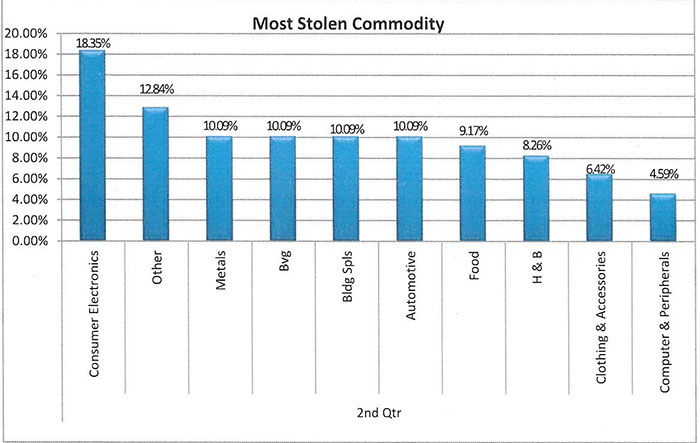
For the first time in recent reporting, food was not only eliminated as the number one target. Food actually dropped out of the top 5 most targeted products altogether. Consumer electronics took the number one spot, and that number will likely rise again in Q3 as stores stock up for the holiday season.
Looking deeper into the specific commodities stolen, construction materials, such as shingles and lumber, took the number one spot on specific items stolen. This is to be expected in the spring months.
How Much Is It Worth?
At an average per load value of $15,000, SC ISAC estimates the 2nd Qtr. losses to be worth $22 million. Freightwatch value per load is much higher, at $174,000, which is more consistent with the historical quarterly average.
New Trends in Theft:
SC-ISAC has recently shared information regarding new trends:
- Bobtail bandits: With increasing frequency, thieves are stealing bobtailed (uncoupled) tractors from freight yards and immediately driving them to truck stops and drop lots near the interstate. The thieves circle around, in search of a loaded and unattended trailer, knowing that a loaded, uncoupled trailer in this location is less likely to have hidden GPS tracking devices. Having identified a target, the thieves are able to hook up the trailer and drive away with the cargo.
- Fictitious Pickups: Deceptive pickups continue to rise – Freightwatch uses the term “surge” -- in terms of frequency and success. Several cases now include thieves stealing the identity of an existing trucking firm to better mask their efforts.
Predictions & Recommendations:
We predict Q3 will present a major spike in cargo theft, as it traditionally does. Labor Day is always the starting gun for an average 61% increase in cargo theft, because stores start stocking up for Black Friday.
Starting right now, this is high season for thieves. We strongly recommend freight and logistics companies that have security challenges review all protocols and contact security companies for assistance where they’ve detected weaknesses.
For a primer on cargo theft, SC-ISAC, and the regional cargo theft councils check out J.J. Coughlin’s book, Cargo Crime. JJ does a great job explaining how cargo theft affects the industry as a whole, the structure of the industry and what can be done to fight cargo theft.
Be safe, be vigilant.
**(Electric Guard Dog is proud to be a sponsor of the SC-ISAC database and active in regional cargo theft councils.)