White House Blames North Korea for WannaCry Attacks
The White House has publicly blamed North Korea for the WannaCry ransomware attack earlier this year that locked more than 300,000 computers in 150 countries.
- By Jessica Davis
- Dec 20, 2017
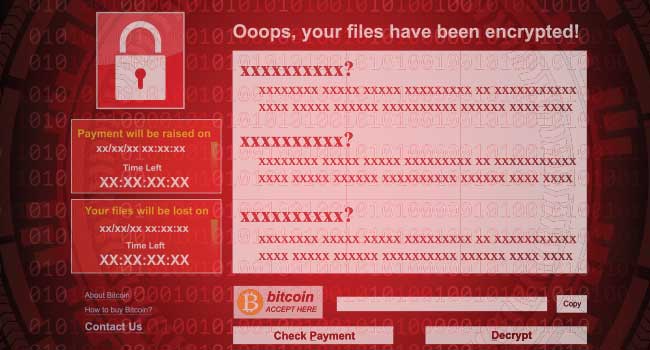
The White House has publicly blamed North Korea for the WannaCry ransomware attack earlier this year that locked more than 300,000 computers in 150 countries. White House Homeland Security Advisor Tom Bossert said Tuesday that the attack was ordered by North Korean leader Kim Jong Un.
Bossert formally announced the blame in an op-ed in the Wall Street Journal on Monday night and followed the statement with a White House press conference Tuesday. At the press conference, Bossert said that other nations, including Australia, Canada, Japan and the United Kingdom as well as private sector partners including Microsoft had agreed with the U.S. assessment that North Korea was responsible for the attack, which was “widespread and cost billions”.
“We do not make this allegation lightly. We do this with evidence. We do so with partners,” Bossert said.
The WannaCry attack was considered unprecedented in scale at the time, locking computers at hospitals, universities and businesses and demanding ransom payments and deletion of victims’ data if they didn’t pay. The ransomware was made possible by a flaw in Windows software that was discovered by the U.S. National Security Agency and made publicly available online in an NSA security breach.
Security researchers believe the notorious North Korean hacking entity known as Lazarus Group carried out the attack on behalf of the North Korean government. Bossert said the goal of the announcement was to “name and shame” the North Korean actors.
“North Korea has acted especially badly, largely unchecked, for more than a decade, and its malicious behavior is growing more egregious,” Bossert said. “WannaCry was indiscriminately reckless.”
The attribution represents a move by the Trump administration to work against malicious cyber activity. Last month, the White House published a document about its Vulnerabilities Equities Process in an effort to increase transparency about how it decides whether and when to disclose cybersecurity flaws.
“Stopping malicious behavior like this starts with accountability,” Bossert said. “It also requires governments and businesses to cooperate to mitigate cyber risk and increase the cost to hackers. The U.S. must lead this effort, rallying allies and responsible tech companies throughout the free world to increase the security and resilience of the internet.”
North Korea has repeatedly denied responsibility for WannaCry and called other allegations about cyberattacks a smear campaign. The White House’s accusation comes as worries increase about North Korea’s hacking abilities and nuclear weapons program.
About the Author
Jessica Davis is the Associate Content Editor for 1105 Media.