Absolute Software report uncovers usage behavior and security risks of connected employees.
MyID technology allows customers to sign and encrypt email from mobile devices securely using WorxMail.

Users who have auto-reload setup on their digital card might be vulnerable.
- By Matt Holden
- May 13, 2015

The hotel & casino says hackers may have access to information about credit and debit cards.
- By Matt Holden
- May 05, 2015

Hopefully, hackers have heart not to launch nuclear weapons.

The changes would be made to confront new security risks in many different areas.
- By Matt Holden
- Apr 28, 2015

The 2015 edition of the DBIR provides insight into the state of cyber-security in 2014.
- By Matt Holden
- Apr 22, 2015

With so many business functions becoming integrated through networked devices or systems, it is no wonder that one of the newly re-introduced buzzwords spreading throughout the physical security industry is integrated security services.
- By Cale Dowell
- Apr 10, 2015

An official has stated that unclassified computers at the White House are vulnerable.
- By Matt Holden
- Apr 08, 2015
Convergence of physical and cybersecurity along with information management solutions.

A cybersecurity activist developed the roster, but it has flaws.
- By Matt Holden
- Apr 01, 2015
Highly malicious strain found only takes 1 click to infect systems using DropBox.

Per Björkdahl shares his thoughts about cybersecurity, the IP video market, access control and interoperability.
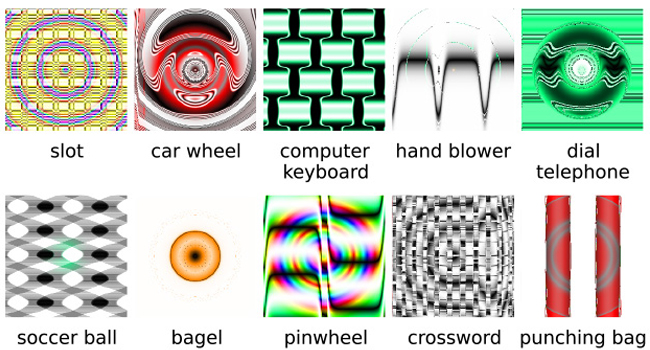
Machines learning to recognize objects with accuracy, but can also be fooled by optical illusions.
- By Ginger Hill
- Mar 25, 2015

A flaw was discovered in the Hilton HHonors program that could let anyone hijack all accounts.
- By Matt Holden
- Mar 24, 2015
Cyber security and cyber space technology has become one of Israel's most important exports.
Rewards start-ups for their innovation in the smart home vertical.

Causing fraudulent charges to appear on credit cards and users being locked out of accounts.
- By Ginger Hill
- Mar 19, 2015

New Jersey recently switched to digital testing, bringing a host of new security concerns with it.
- By Matt Holden
- Mar 17, 2015

Malware activated as soon as the device is plugged in; no further action required.
- By Ginger Hill
- Mar 16, 2015