Be careful where and what you use to charge your very trusting iPhone because your device could get infected with malicious malware!
 Researchers from the Georgia Institute of Technology have created fake iPhone chargers, dubbed “Mactans,” that not only “juices up” your iPhone, but installs custom, malicious applications. Small computers are housed inside these bogus chargers, and your unsuspecting and obedient iPhone doesn’t discriminate as it treats these computers just like any other computer by responding to USB commands. If your iPhone is unlocked while attached to the USB host, the host is in control of your smartphone.
Researchers from the Georgia Institute of Technology have created fake iPhone chargers, dubbed “Mactans,” that not only “juices up” your iPhone, but installs custom, malicious applications. Small computers are housed inside these bogus chargers, and your unsuspecting and obedient iPhone doesn’t discriminate as it treats these computers just like any other computer by responding to USB commands. If your iPhone is unlocked while attached to the USB host, the host is in control of your smartphone.
So, how did these researchers do it?
Well, it sounds really simple. They just used the Mactan to install an app package onto an iPhone.
Now, here’s where it gets a bit complicated!
This app package then takes advantage of an Apple-devised system that permits developers to deploy applications to their own devices for testing purposes. This requires an Apple-generated provisioning profile to be installed over USB to identify a specific phone and application, allowing the application to run on the named device.
The malicious charger interrogates your iPhone because it wants to get your phone’s UDID, a unique ID number that identifies your particular iPhone. This vengeful charger then sends your phone’s specific UDID to Apple’s Web page which generates provisioning profiles. These profiles are then deployed to your iPhone, and the vicious malware is identified by the profile.
Once this is done, what can happen?
Researchers gave a Facebook example in which a malicious Facebook app replaced a real app with a trojaned version. This enabled the malware to take screenshots of the iPhone wherever passwords were being entered.
This type of attack does have limitations, though, including:
- The iPhone’s screen must be unlocked;
- Generating a provisioning profile requires the attacker to have a valid developer account;
- A valid developer account can only generate profiles for 100 different phones; and
- There’s no facility to remove the UDID that associated with the developer’s account.
What has Apple done in response to this discovery?
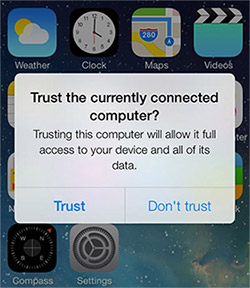 They have made the iPhone a little less trusting. iOS 7 will ask users if they want to trust the currently connected device, indicating that it could be a Mactan-like device.
They have made the iPhone a little less trusting. iOS 7 will ask users if they want to trust the currently connected device, indicating that it could be a Mactan-like device.
Note: I'd be sure NOT to use those "free" charging stations in airports or any other location, for that matter. I'm sure hackers will soon be swarming to them...especially after this discovery.
Source: http://arstechnica.com/security/2013/07/trusting-iphones-plugged-into-bogus-chargers-get-a-dose-of-malware/