In 2010, the Newark Liberty International Airport (EWR) had to shut down all three of its terminals for six hours after a Rutgers graduate student ducked under a rope undetected to say goodbye to his girlfriend. Nearly 200 flights were delayed or cancelled, and thousands of passengers were inconvenienced while security officials searched for the man.
 The breach occurred in Terminal C, when a TSA officer left his exit lane post for 85 seconds. The airport drew an additional round of criticism when TSA officials acknowledged that investigators had to use footage from an airline's security system because surveillance cameras at the checkpoint had failed to record the incident.
The breach occurred in Terminal C, when a TSA officer left his exit lane post for 85 seconds. The airport drew an additional round of criticism when TSA officials acknowledged that investigators had to use footage from an airline's security system because surveillance cameras at the checkpoint had failed to record the incident.
The disruption at EWR prompted U.S. Senator Frank Lautenberg to add provisions to the 2011 Homeland Security Appropriations Bill to increase civil and criminal penalties for knowingly circumventing airport security.
Two years later, the airport found itself in a similar situation when a 64-year-old British national entered the secure side of Terminal B through a security checkpoint exit. This time, the TSA agent involved was giving directions to another passenger when the man slipped past the guard. The incident came to light when the man approached an airline agent for assistance, prompting local and national critics to ask how many other undetected breaches have occurred at EWR and other airports.
Today, TSA agents guard over 2100 exit lanes in airports across the U.S., not to mention over 850 non-co-located ones that the TSA is in the process of transferring responsibility, including financial burden, to airport owners. When you consider how many passengers cross those lanes every minute, every hour, every day, the sheer number of opportunities for incidents to occur is almost overwhelming.
Using Surveillance Technology to Tighten Exit Lane Security
With federal budget cuts and the expected transfer of security responsibilities looming in early 2014, airport operators across the country are feeling the urgency to assess the best way to secure their checkpoint exits. Some have already mobilized resources to meet the anticipated hand-off. Some are taking a "wait-and-see" stance, banking on the possibility that some type of industry or legislative intervention will delay or eliminate the need for investments in new equipment or additional personnel. Others are clearly embracing technology and innovation to augment existing security staff in watching for any wrong direction flow of passengers.
Most of the more forward-thinking solutions incorporate video surveillance as part of the security strategy. For instance, some airports have eliminated doors at checkpoints and instead have adopted an open configuration. To counter the possibility of unauthorized passage, multiple network surveillance cameras have been mounted in the area – some to serve as “watchers” that merely observe crowd movement and others to serve as “detectors.” The detectors incorporate a layer of intelligence on the camera to identify anyone moving in the wrong direction, trigger an alarm and send an alert to security officials while continuing to record the breach. This intelligence, also referred to as video analytics, is often a third-party application designed to sit on the cameras in much the same way as apps sit on your smartphone.
How do detection analytics work? Wrong direction analytics can be standalone, one-way passageway control systems sitting on ceiling-mounted cameras powered by state-of-the-art processing software. Or, they can be integrated into a larger, enterprise-wide surveillance network. The analytics-enhanced camera detects in real time when someone moves in the opposite direction of normal traffic flow. The detected event can automatically trigger a number of actions such as sending a video clip of the incident to a security station, sending a short text message alert to security, sounding a siren or broadcasting a warning message over the public address system. The software manages alarms using standard protocols and performs data storage and management by pushing video and analytics data automatically to the server and/or a web report.
Installation is as easy as attaching an IP camera to the network by plugging it into the nearest network switch, just like you would any other peripheral device. Because the camera is network-based, it can be custom programmed and maintained remotely from a central security station or IT department or even an authorized mobile device with a network browser. The cost-efficiencies and scalability of the network-based solution make it ideal for fluid environments like airports.
A number of airports throughout the country have already implemented automated exit systems, including Atlantic City International Airport and Kalamazoo/Battle Creek International Airport.
Using Surveillance Video to Manage Queues
Managing the flow of travelers through the various airport queues is another area of concern. Airports are like cities and city transportation networks as the demand for real estate is insatiable, forcing operators to figure out ways to optimize the ever-increasing flow of traffic. Because airport terminal space is always at a premium, the best way to increase efficiency while operating within security constraints is to measure the flow of people in real-time and adjust operations on the fly.
As an extreme frequent flyer, I can attest to the fact that we spend an inordinate amount of time in line waiting for customer service, check-in, luggage inspection, and to go through security and customs control. Managing passengers’ wait time is important to business performance. The quicker the lines flow, the more time and money travelers can spend in retail stores and the fewer costly delays in plane departures. And, perhaps most importantly, it’s just good PR. With so many airlines and airports competing for business, it pays to keep travelers happy because the more happy travelers, the more repeat customers.
Like the analytics used to augment security in exit lanes, airports are starting to examine third-party applications that can reside on network cameras to assist in queue management. There are a number of developers on the market today offering advanced analytics to measure everything from the number of people standing in line to estimated wait-time at checkpoints, and then report those metrics in real time to airport staff directly from the camera or through a data server.
Having real-time data at one’s fingertips is crucial to deploying appropriate staff efficiently. With timely information, airport managers can react quickly to changing conditions and make instant decisions to address any bottlenecks. Over the long term, managers can compare the performance of different queues and use the historical data as an aid to future resource planning by the hour, day, week and month.
IP video cameras equipped with queue management software can measure a host of key performance indicators in real time which can ultimately enhance the passenger experience. The analysis that can be gleaned from these applications includes such things as: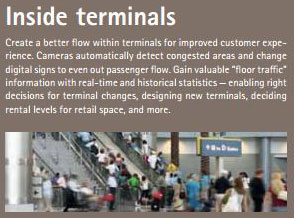
- Predicted waiting time in minutes;
- Number of passengers in each queue line;
- Number of passengers being processed at the gate per minute;
- Detection of overcrowded environment and abnormal situations; and
- Heat map of the terminal to ascertain the distribution of passengers and occupancy of specific space.
Open Application Platforms Make It All Possible
What makes this all possible is that manufacturers are now designing their network cameras on open platform standards. This allows third-party developers to create analytics applications that can be downloaded right onto the camera. As unique challenges arise, developers can devise intelligent capabilities such as recognition, counting, detection and tracking to meet the changing needs of the airport.
There are dozens of third-party applications to enhance the functionality of network cameras. But like the apps for smartphones, I expect that number to grow exponentially in the coming years. With the ever-increasing processing power residing on network video cameras, the possibilities for these “computers with a lens” to support more sophisticated, bleeding edge analytic technology is only bounded by developers’ imagination.