 Let’s face it, cyber criminals are getting smarter about manipulating, stealing and profiting off of others’ identities. Medical identity theft is on the rise. Tax return fraud is higher than ever. Children are being targeted for identity theft, and large corporations are being compromised more frequently for their customer and employee data. As technology has become cheaper and is more accessible, cyber criminals are engineering new ways to steal personal information and use it for financial gain.
Let’s face it, cyber criminals are getting smarter about manipulating, stealing and profiting off of others’ identities. Medical identity theft is on the rise. Tax return fraud is higher than ever. Children are being targeted for identity theft, and large corporations are being compromised more frequently for their customer and employee data. As technology has become cheaper and is more accessible, cyber criminals are engineering new ways to steal personal information and use it for financial gain.
Before diving into how identity management has evolved over time, let’s take a look at what identity management actually means.
Managing your identity has become more than safeguarding your credit data, financial information and Social Security Number (SSN). Today’s increasingly digital world means traces of your identity are everywhere – on social networks, in government and retailer online databases, on the cloud at work and in your mobile devices. Now, in addition to keeping your financial information, banking data and SSN out of reach of identity thieves, you must protect every digital facet that cyber criminals could use to gain more information about you. Sounds near impossible, right?
Actually, with more consumer awareness about the importance of identity management, a change in online habits and with the right tools, protecting your identity is feasible. Let’s take a look at how identity management has evolved over time and where it is headed in the near future.
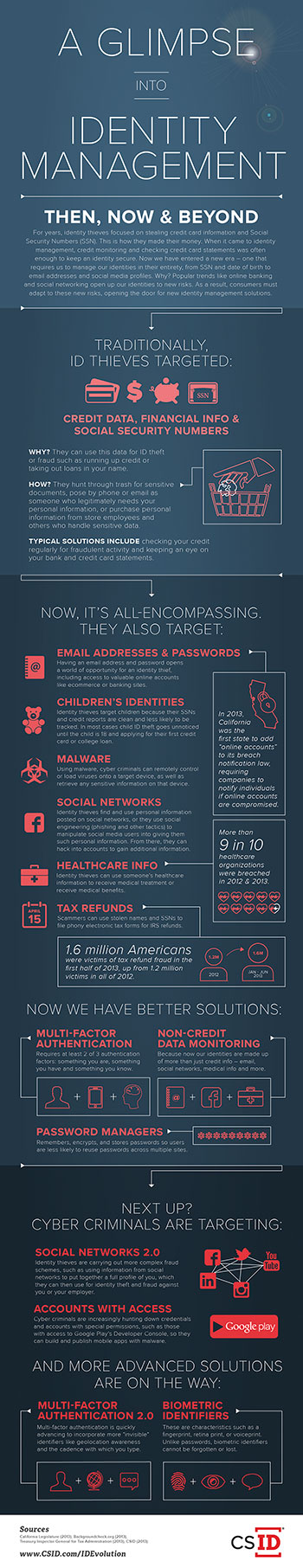
Identity Theft, Then and Now
Prior to the digital age we live in today, identity thieves would gather personal information by hunting through trash for sensitive documents, calling and posing as someone needing your personal information for legitimate reasons or even purchasing personal information from store employees or others with access to files. Thieves continue to use those tactics, but have added an array of technical tools to the lineup, for example, malware. Cyber criminals employ malware to collect personal information from desktop and mobile devices. The Juniper Networks Mobile Threat Center released a report in 2013 showing a 600 percent increase in malicious app growth from 2011 to 2012.
In addition to malware, social networks have become an important tool for identity thieves. Social networks offer a gold mine of readily available personal data for cyber criminals. Criminals can manipulate users into giving them personal information via phishing schemes on social media networks or simply by looking up personal data that is public. Social network privacy policies change frequently, leaving users unaware that their personal information is readily viewable to prying eyes. In many cases, however, users simply have not set up their privacy settings to protect against identity theft risks.
Social networks and online gaming sites are also a hotspot to collect personal data from minors. Cyber criminals are targeting children’s identities more frequently as fraudulent activity can go unchecked for years until they turn 18. In CSID’s 2013 Child Identity Theft survey, we found that while 76 percent of parents are concerned that their child’s identity may be stolen and, 52 percent of them are not currently taking any action to prevent the misuse of their child’s online information, giving identity thieves an open opportunity to prey on minors’ clean credit reports.
Tax and healthcare identity fraud have also seen increases. According to the Ponemon Institute’s Study on Patient Privacy & Data Security, more than 90 percent of healthcare organizations were breached in 2011 and 2012. Identity thieves use stolen healthcare information to receive medical treatment or benefits. Tax fraud affected 1.6 million Americans in the first half of 2013, up from 1.2 million victims in all of 2012.
Identity Theft in 2014 and Beyond
Identity thieves will continue to engineer new tactics to steal personal information. Based on the trends CSID has seen in cyber-criminal activity. Here are three predictions on what to expect of identity thieves this year and in the near future:
- Sophisticated marketplaces for stolen data have become more commercial and will continue to develop as digital currencies, such as Bitcoin and Litecoin, fuel their growth. These currencies offer identity thieves a way to conduct business transactions online and anonymously.
- Expect to see increases in credential theft from app developers with special permissions, such as those with access to Google Play’s Developer Console. These credentials are particularly valuable to cyber criminals because they allow them to build and publish mobile apps infected with malware that can gather and steal valuable information like addresses, credit cards and logins from a user’s mobile device.
- Complex social network fraud schemes will continue to increase. In addition to social media phishing attempts where an identity thief will pose as someone you may know in order to extract personal information from you via personal messages or chats, cyber criminals are starting to put together full profiles from data on social networking sites to use for identity theft purposes. For example, most social media users do not think twice about posting a mother’s maiden name, a pet’s name or a school mascot which are common password reset questions as well as credit authentication questions. Identity thieves can piece together personal information from your social media posts to impersonate you for identity theft and fraudulent purposes.
Identity Management Solutions that are in Place and Coming Soon
Despite the overwhelming statistics and state of identity theft, companies like CSID have created and continue to develop advanced solutions to help consumers better manage and protect their identities. Here’s a look at a few solutions that are currently in place and continue to be developed by companies to better protect consumers’ personal information:
Multi-factor authentication: This extra layer of security requires at least two of three authentication factors when logging into an account: something you are, something you have and something you know. Technology companies are quickly advancing this solution to create more “invisible” identifiers – like geolocation awareness or cadence with which you type – to make multi-factor authentication less of a hassle for consumers.
Non-credit data monitoring: Because identities are made up of more than just credit information, monitoring solutions now include email addresses, social networks, medical information and more. Consumer, employee and customer monitoring services send an alert when a piece of your identity has been compromised in real time. Consumers can become aware of the problem when it happens, rather than find out months after the fact when the damage has already been done.
Biometric identifiers: Voiceprints, fingerprints and retina scans are all examples of biometric characteristics that can be used in place of or in addition to a password. Unlike passwords, these identifiers cannot be lost, forgotten or stolen.
Identity theft is not going away any time soon, but advances in technology can lead to better identity protection and management. Stay aware, stay educated, and most of all, make identity management a priority in your personal and professional life.