
The OSI Model and Physical Security
Momentum has shifted technology to the network
- By Michael Leary
- Mar 04, 2014
 When the IP camera was introduced to the physical security
industry in the mid-1990s, the move from analog to digital
was set in motion. Adoption of this technology began slowly
but has steadily gained momentum. Security manufacturers
with product(s) other than video have recognized the value of IP networks as
a platform to allow for the control of and communication with their systems.
IP networking is a great choice because it is extremely flexible while also being
standard-based, making it highly reliable.
When the IP camera was introduced to the physical security
industry in the mid-1990s, the move from analog to digital
was set in motion. Adoption of this technology began slowly
but has steadily gained momentum. Security manufacturers
with product(s) other than video have recognized the value of IP networks as
a platform to allow for the control of and communication with their systems.
IP networking is a great choice because it is extremely flexible while also being
standard-based, making it highly reliable.
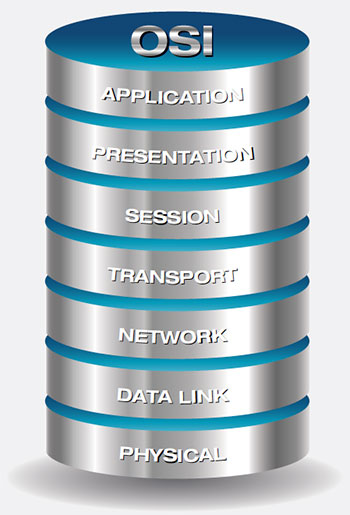
The Open Systems Interconnection Reference (OSI) Model is often mentioned
in IP-related discussions. The seven layers in the OSI stack are discussed
in order from the top of the hierarchy to the bottom, each of which
relates to a different part of the process of network communication.
The Application Layer. At the top of the stack, network-aware applications
allow users to interface with other network-based resources. There are
many protocols at work within this layer that security systems rely on to either
operate properly or offer valuable features. Many network video recorders leverage
the following protocols:
- Dynamic Host Configuration Protocol (DHCP)—Automatically configures
the IP address, subnet mask, gateway and DNS information for
enabled devices. Manufacturers may offer this feature in an effort to make
their network devices easier to deploy. (I don’t recommend using DHCP
for IP video systems. I prefer using a static addressing scheme.)
- Hyper Text Transfer Protocol (HTTP)—Browser-based clients have long
been popular for viewing and/or controlling networked video products.
- File Transfer Protocol (FTP)—Supports the transfer of data to and from a
server. It is common for video recorders to deliver snapshots or video clips
to an FTP server for storage and retrieval.
- Simple Message Transport Protocol (SMTP)—This protocol provides
support for systems that are capable of sending alerts and video attachments
via email.
- Simple Network Management Protocol (SNMP)—Used for monitoring
and reporting on the condition of a supported network device. These
messages, SNMP Traps, are sent to a management system for review. Trap
information will vary depending on the device and could include system
reboot, hard drive health, link down, link up and system temperature.
The Presentation Layer. Moving down the stack, text, graphic and audio
information is routinely transmitted over IP networks by security-related
devices. The primary function of this layer is to properly format or translate
information that will be presented to the user at the application layer or sent
to the lower layers for transmission across networks.
ASCII or EBCDIC is used for text while audio may require standards like
G.711 or WAV to achieve the desired results. A number of graphics formats
are implemented at this layer to provide the visual experience to the user:
- Bitmap (BMP);
- Graphics Interchange Format (GIF);
- Joint Photographic Experts Group (JPEG);
- Moving Picture Experts Group (MPEG); and
- Audio Video Interleave (AVI).
Many IP cameras, NVRs and networked DVRs use JPEG for snapshots
and some variant of MPEG for compression. Some applications may rely on
this layer for encryption of the data before transmission, as well.
The Session Layer. Responsible for set up and teardown of connections
between networked devices, the session layer and transport layer work handin-
hand to manage these connections.
In the event that multiple connections exist between a source and destination,
the session layer ensures the proper data gets delivered over each
connection.
The Transport Layer. The data is broken into segments, and information
about the communication protocol being used and the source and destination
ports are added. Two key protocols are commonly used to aid with the
mechanics of data transport: Transmission Control Protocol (TCP), a reliable
protocol, and User Datagram Protocol (UDP), an unreliable protocol.
TCP’s reliability is possible due to features like acknowledgement between
the communicating devices, sequencing of data, flow control and error checking.
UDP, on the other hand, is considered unreliable because it doesn’t use
acknowledgement, flow control or error correction, so it may be better described
as “best effort.” Most of the time, UDP is successful while using a
lot less overhead—all the extra instructions and processing—than TCP. Less
overhead allows for a quicker execution and less latency (delay) related to the
processing of the data as it moves through the network. UDP is often chosen
for video transmission for this reason.
Source and destination ports are used at the transport layer to make sure
the data being sent between devices is properly handled. Protocols commonly
used with video security, like HTTP (Port 80), SMTP (Port 25) and FTP (Port
21), are associated with these specific ports.
The Network Layer. Routers and some high-level switches operate here.
While routers are used to join networks or network segments together, network
layer switches perform switching functions at the presentation layer,
and additionally, have routing capabilities. IP addresses, also known as logical
addresses, are used by network layer devices to make decisions about whether
traffic should be allowed to move from one network to another. The network
layer has had a positive impact on the physical security field with regard to
remote access.
The ability to communicate bi-directionally with different types of security
devices over the Internet is possible because of network layer devices. Being
able to view video from just about anywhere there is a network connection
on almost any type of smart phone, tablet or computer has transitioned from
being a desire to an expectation for end users.
Installers are able to configure networks so they can access devices remotely
for troubleshooting or adjustment. Remote monitoring over the Internet
and use of the “Cloud” for recording and storing video and other data off-site
are capabilities we enjoy because of routing.
This is all great but it doesn’t come without a little pain as well. Anyone
who has needed to implement some of the above solutions has likely dealt
with configuring a router. The first challenge is to get to the management interface
of the routing device. Many end users are completely unaware of the
username and password that will allow an installer access to their router. It is
not unusual to have to secure this information from the ISP.
Since there are many types of routers, once you have access, you will find
that all of the interfaces are different and each manufacturer will approach
things in their own way. End users rarely seem to have documentation for
their device, and you may find it difficult or too time consuming to work with
the ISP. The manufacturer may make their product manuals available online,
but if not, there are some sites on the Internet that deal with router configuration
and act as a clearinghouse for this type of information.
The first feature commonly used when setting up the router for remote
access is dynamic domain name service (DDNS). Frequently, the Internet
services being used will use a dynamic IP address for access to their public
network. DDNS is required to ensure the end user can reach the router over
the Internet regardless of changes to the IP address. DDNS works by replacing
the dynamic IP address with a friendly name like “mikesrouter.ddnsservice.
com,” that can be used to identify the WAN side interface of the router.
A publically available DDNS server keeps track of all IP address changes on
that WAN interface so the friendly name can be resolved and users can attach
as desired. DDNS is not needed, however, when the router has a statically assigned
IP address.
Most LANs use a private IP addressing scheme, but because it is not possible
to route to private address port forwarding is used to attach to devices
inside these networks. Tables in the router interface allow assignment of port
numbers to devices used in conjunction with the WAN IP address or friendly
name to identify the destination of inbound traffic. Using a Web browser to request
to connect might look like “http://mikesrouter.ddnsservice.com:2001,”
where port 2001 has been assigned to the target device.
It is important to remember not to use port numbers from the group of
well-known ports, 0–1023, unless instructed to do so by the manufacturer of
the device you wish to attach to because ports in this range have specific usages.
There are other features that are available on many routers: firewalls,
DHCP servers and content filters are just a few. Whether or not these services
are used is largely dependent on the LAN user’s requirements.
The Data Link Layer. The next to last layer relates to switching in which
the switches used in small, medium and large IP video systems are presentation
layer devices. There are also session layer switches that have IP routing
capabilities in addition to standard switching features.
These high-level devices are often called multilayer switches because they
can function at both layers.
When looking at a switch, its apparent use is to physically connect network
devices to each other, yet delving a little deeper, they do much more. Switches
are “smart,” meaning they learn about the devices that are attached to them
via a network adapter, identified with a unique media access control (MAC)
address, also known as physical addresses because this identification is permanently
assigned to the hardware at the factory.
When a switch discovers a new device, it includes its MAC address and
associated port to a list that it maintains. This table of information allows the
switch to make decisions about efficiently directing the frames that arrive at
its ports.
A frame is a container that holds the data and instructions required to get
it to its destination. Before it can be transmitted, the data must be broken into
manageable pieces known as payload that is encapsulated with information
for proper handling as it travels from the sending to the receiving device. This
occurs for the first time at the transport layer, but at the data link layer, added
information is about the protocol and ports used, which is combined with the
payload and placed in a package called a segment.
At the session layer, the segment and the IP addresses of the sending
and receiving devices are encapsulated in a packet that is handed down to
the presentation layer where it is combined with the MAC addresses of the
sending and receiving devices. The packet and MAC address information is placed inside a frame.
The switch examines each frame as it enters
one of its ports. The MAC address information is
compared against the information in the switches’
MAC address table.
If the destination MAC address is in the table,
the frame is sent out through the corresponding
port. If the destination MAC is not in the table, the
switch must continue “learning.” To learn it sends
a single frame out of every port, expect the originating
one. When the destination device receives
the frame, it will send a response back to the sending
device. When that frame enters the switch,
the MAC address is associated with that port and
the MAC table is populated with the information.
Now, all the remaining frames for communication
between these devices will be sent through the
validated ports.
The efficiency of switched communication may
not be appreciated when traffic on the network is
light; however, when higher bit rate devices, like
megapixel and HD cameras, are in use on the network,
efficiency is a primary concern.
The Physical Layer. At the bottom of the OSI
stack is where the data moves in the form of zeroes
and ones, and the actual transmission of data between
devices occurs. The use of IP devices in physical
security applications continues to grow rapidly.
The frequency with which these devices need to be
placed outside of the 100 meter limitation of UTP
and standard switching also has increased.
Fiber optic cable can allow users to extend well
beyond that distance limitation, but there are other
media types that can, too.
Coaxial cable was used for early networks prior
to UTP. There are many manufacturers that have
developed transceivers to transmit Ethernet over
Coax (EoC). In fact, recent statistics indicate that
there are well over 250 million analog cameras attached
to coax in North America.
EoC products vary in their capabilities, and
many can transmit Ethernet and inject power over
hundreds of meters. Installers updating an analog
system to IP may choose to reuse the coax cabling
infrastructure that is already in place. Keep this solution
in mind when upgrading in environments
that could be too dangerous, difficult or expensive
to re-cable such as prisons, hospitals, casinos or other
environments with toxic materials, like asbestos.
There are transceiver products that can be used
with shielded twisted pair, UTP and even 18/2 wire.
This wire may not provide quite the range of coax,
but it still can exceed 100 meters and allow for more
flexibility when dealing with existing cable.
Air is used for wireless transmission, an option
that is frequently used in applications where running
cable is too difficult or costly. It is a solution
that is finding its way into many IP projects. Most
of us are familiar with Ethernet wireless because
Wi-Fi is used with smart phones, tablets and laptops
on a daily basis. This same technology can be
leveraged for use with wireless security cameras.
When using Wi-Fi, consider installing an access
point exclusively for the security cameras
so other non-security devices won’t compete for
bandwidth and priority. If this is not possible, use
an access point that supports Quality of Service
(QoS) so the camera can be given priority over
non-critical devices. Most outdoor IP cameras are
not wireless, so for these devices, wireless clients
can be used to transmit their data streams. On the
other end, the data stream is received by an access
point called a host. There are several licensed and
unlicensed frequencies that may be used.
One commonly-used, unlicensed frequency is
5.8GHz. It is attractive due to its ability to support
high throughput over long distances at a reasonable
cost, but it does require clear line-of-sight between
the client and host for best performance. 4.9GHz
frequency works in a similar fashion to 5.8GHz, but
is licensed and reserved for public safety use, while
2.4GHz frequency is commonly used for Wi-Fi and
other wireless devices. (I recommend avoiding this
portion of the wireless spectrum due to its heavy
use and the interference that can be found there.)
A lower, unlicensed frequency is 900MHz, which
is used by wireless products, sometimes referred to
as near-line-of-sight because it’s able to penetrate
some clutter, normally trees or foliage. However, the
ability to penetrate obstructions is offset by a sharp
decline in throughput, when compared to 5.8 and
4.9GHz products.
UTP is the most cost-efficient and widely-used
cable for networking, but it’s nice to know that there
are additional options like fiber, coax and wireless
available to help solve the environmental and distance
challenges many projects can present.
This article originally appeared in the March 2014 issue of Security Today.