Photo ID cards have come a long way in the past two decades, especially those prevalent in the K12 school segment. In fact, based on a recent survey conducted by our organization of K12 education customers across the United States, more than 94% of schools responded that they use ID cards. The vast majority also print their cards in-house versus outsourcing them to a third-party service bureau. Survey results confirm the top three uses for ID badges are building and facility access, visual identity, and lunch programs, a reinforcing fact that schools are making the most out of their ID card printer investment.
Although there is no question that student and faculty safety in schools is a top priority, IDs can be used for much more than just access control and visual identification purposes. Using badges for a variety of functions not only defrays the initial investment of the printer or system, it leverages the technology to serve multiple purposes.
Because the budget is likely one of the primary deciding factors when it comes to the printer model a school will ultimately purchase, it's important to understand the many ways IDs can improve processes and maximize resources. By expanding the use of ID badges throughout a school's campus with some (or all) the following applications, the efficiencies in other vital facets of academia can also be optimized.
Access control and visitor management: Monitoring who is entering and exiting school facilities each day with an ID badge is the foundation of a safer school environment. The leading means for tracking this kind of information with badges include the use of magnetic stripe, proximity and smart card technologies. When these are integrated with an automated access control system, all traffic into and out of school facilities is tracked and recorded, as well as the length of time each individual spends within the building.
Color-coding badges is a popular method to easily differentiate the faculty, staff and student body. With color-coding, an area of the ID badges are printed in a color that represents a group of people: red for administration, green for teachers, blue for students, and so on. Temporary-expiring badges expire gradually and reveal a distinctive color change that's highly noticeable from a distance and are an inexpensive solution to monitoring short-term visitors.
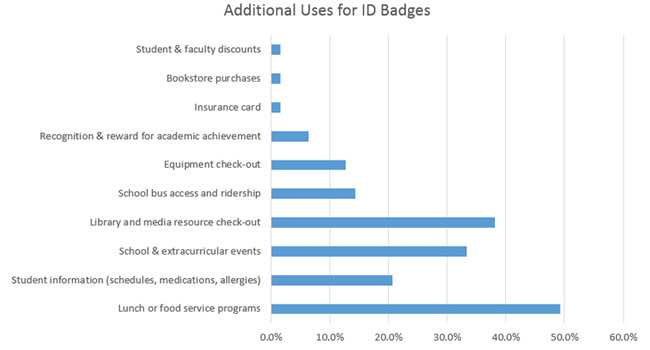
Maximize the real estate on ID cards: Most IDs feature a student's name, photo, the school's name, and a grade level. However, more than 60% of schools indicated they only print information on one side of a student ID card. By taking advantage of both sides of an ID card and supplementing the basic details with class schedule information, medical or allergy details, or emergency contacts, school IDs become exponentially more beneficial, especially if a crisis arises. Additional data that can be used on IDs includes emergency preparedness instructions, bus stop information and graduation year.
Remove cash from the school lunch equation: Using school ID cards for school lunch programs has gained steady momentum over the past five years, because it eliminates the need for students to carry cash. Barcodes tend to be the most frequently used technology option as they do not require any special equipment beyond a standard ID card printer and barcode reader. Magnetic stripe cards may store value, and when swiped, automatically deduct the cost of lunch when used. Both technologies are easily integrated with automated point-of-sale systems allowing more accurate transactions and account management.
Track school bus access and ridership: Approximately 15% of survey participants use school ID cards as part of a student transportation program. Adding a bus number to an ID improves the level of the student's security by safeguarding that the correct bus is boarded. It also ensures that unauthorized riders are not allowed on the school bus without the proper credentials.
Monitor classroom attendance: Implementing software into a student ID card program can substantially improve the effectiveness of tracking classroom attendance. Software records tardiness or absence information, allowing teachers to notify parents via email if warnings or after-school detention are issued. Attendance data can then be used for timely reporting at the end of the month, semester and school year.
Manage library and technology assets: A common use of school IDs with barcodes or magnetic stripes includes the management of library, media, and technology resources like computers, tablets, and other devices. In fact, nearly 40% of those surveyed indicated they use their student ID cards to track and protect these educational assets.
Motivate students to achieve their goals: A little creativity can go a long way when it comes to ID cards. A school in Kentucky recognizes academic achievement and classroom attendance with rewards cards. At the end of each quarter, students receive a card that reflects their performance with coupons printed on the back of cards that can be redeemed at local businesses. A local bank even supports the school's efforts by depositing $1 into a savings account for students for each "A" they receive.
Partner with a trusted provider: School ID cards are an invaluable asset not only to student identification but to safety and security, access control, asset management and much more.
Ensuring the most cost-effective and substantial return on your investment starts with using the technology across multiple platforms. The key is finding a reputable provider who understands the ABCs of ID cards. A retailer specializing in photo ID – not only ID printers but also printer supplies, software and badge accessories – will have the above-average expertise to guide your purchasing decisions based on your needs, goals and budget.