
A Fine Balance: Bandwidth Consumption vs Live Video Monitoring
Managing security along public transit routes comes with many challenges, particularly as more people rely on buses and trains for daily transportation. With so many commuters, and multiple vehicles moving around the clock, the risk factor for accidents, altercations and other issues remains high.
Advanced, real-time video surveillance monitoring is a critical part of protecting the public. When an incident occurs on a transit vehicle, you can immediately see what’s happening, and also share that video with police or other emergency personnel.
Most transportation agencies, however, don’t have an unlimited budget to live stream high resolution megapixel images to their command center. Streaming 1080p video over a 4G LTE network, for example, can be costly, especially when multiplied over hundreds of buses or trains each with multiple surveillance cameras.
So how can transportation agencies maintain regular live access to their mobile surveillance cameras without incurring a massive expense? Here’s some advice on managing mobile bandwidth consumption.
1. Pre-program your IP cameras
One of the most effective ways to reduce your bandwidth is to pre-program your IP surveillance cameras based on activity level. This takes a bit of time, but it’s well worth the effort. There’s no sense in capturing 1080p images inside of an empty bus, so do a thorough review of your agency’s surveillance needs. When do you absolutely need 720p or 1080p images? And when will a 2CIF or 4CIF image suffice? Remember that the amount of activity the cameras are capturing affects the bit rate, so consider the complexity of your scenes. You can maximize your bandwidth by programming your IP cameras to record at the right bit rates for your vehicles’ activity levels.
Let’s take a closer look at how to do this:
During low activity times (when fewer riders are on board a vehicle, or the vehicle is parked at a depot) you’re capturing mainly static scenes. In this scenario, capturing a 2CIF resolution image at 15 frames per second (fps) would result in a camera bit rate of 0.11 Megabits per second (Mbps).
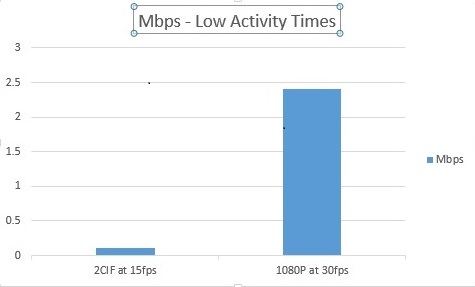
Capturing this same scene in 1080p, at 30 fps, would result in a camera bit rate of approximately 2.4 Mbps, more than 20 times the bandwidth of the 2CIF image. So you can see how a little adjustment at the right time goes a long way toward reducing your overall bandwidth consumption.
Here are a few more scenarios to consider:
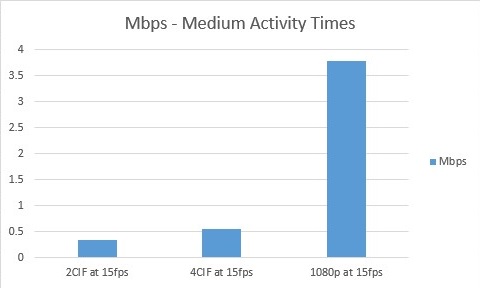
- During medium activity level times (in between peak hours, for example, when your vehicles are making frequent stops and passengers are getting on and off the vehicle) your cameras are consuming more bandwidth.
A 2CIF image captured at 15 fps would result in a camera bit rate of 0.33 Mbps. A 4CIF image, also captured at 15 fps, would result in bit rate of 0.55 Mbps. A 1080p image, also captured at 15 fps, would result in 3.78 Mbps.
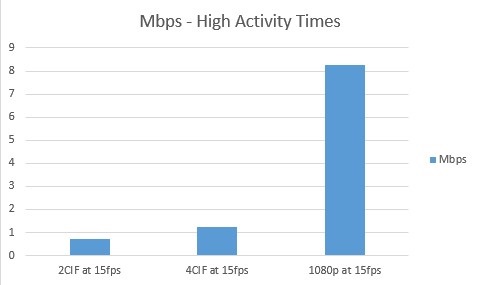
- During your highest activity times (defined as those periods where there are many passengers onboard vehicles and therefore lots of motion) you will be consuming the most bandwidth because the cameras are capturing complex scenes.
A 2CIF image captured at 15 fps results in a camera bit of 0.72 Mbps. A 4CIF image captured at 15 fps results in a camera bit rate of 1.22 Mbps while a 1080p image, also captured at 15fps, results in 8.25 Mbps.
Understanding the impact your frame rates have on bandwidth consumption during low, medium and high activity periods is key, and sets you up well for the next step in this process.
2. Strike the right balance
The key here is to find the best balance between image quality and bandwidth consumed. You don’t want to incur bandwidth costs to view high resolution images of empty buses, but you also don’t want grainy, pixelated images when you are trying to decipher important details.
The best approach is to test a few, different resolutions and frame rates at different times to find the right balance.
Remember, the numbers cited above are examples, and factors like the position of your surveillance cameras, the lighting inside your vehicles, and the type of scenes captured all play a part in bandwidth consumption.
3. Take advantage of alternate stream recording
Once you have determined the best bit rates to use throughout the day, you may be asking yourself: “What if an incident occurs on a vehicle at a time when I’ve programmed my cameras to capture only 2CIF images?”
The answer, of course, is to use alternate stream recording. Use the low resolution stream for live viewing, and then record a higher resolution stream to your network video recorder (NVR). This gives your command center the ability to see into buses or light rail trains as needed using much less bandwidth, and still ensures that the system is capturing high quality, evidentiary video that you can pull later for forensic analysis should an incident occur.