How to Protect Yourself From WannaCry
The WannaCry attack started last Friday and has affected 200,000 computers in almost 150 countries around the world.
- By Peter Butler
- May 18, 2017
Recently reported immense ransomware attack has created havoc among netizens, government organization, companies and every single person related to the internet world. WannaCry 2.0 or WannaDecrypt0r 2.0 ransomware was slowed down on Monday when cyber security experts struggled to track the attacker and shield against any of the possible variants that could appear afterward. Shortly after that, the attack was decelerated with the discovery of a kill switch through its code.
The WannaCry attack started last Friday and has affected 200,000 computers in almost 150 countries around the world. The attackers of this ransomware had demanded $300 in bitcoin within the time period of three days which should be deposited in an anonymous account. Yet, the amount is doubled to $600 if the victim is unable to pay it within three days and after one week the data will be deleted by the hackers without any notification.
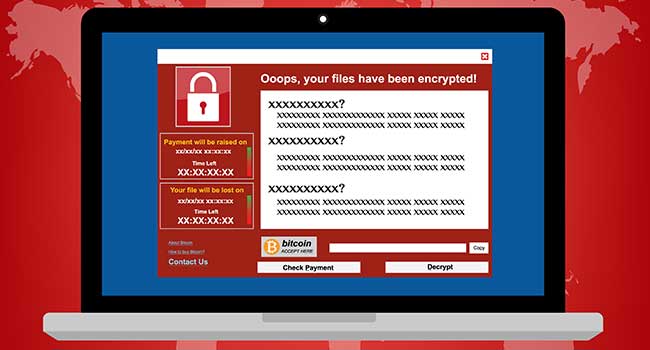
What is WannaCry?
WannaCry is a ransomware that seizes your computer activity and takes control of your system containing all your personal data. Through a screen display, it demands a ransom amount and threatens to hold the system hostage until the demands are unpaid.
The attack was first exposed last week from the UK health service that was one of the most dominant computer hacks. It has also affected the multinationals such as FedEx and shuttered Renault SA car factories. Also, the Tokyo-based company Hitachi Ltd, on Monday reported some vulnerabilities in their system on locations including Japan and others. The security experts are linking this cyber-attack to be generated from North Korea. This is assumed because of the fact that this particular code in the earlier version of the ransomware was used by another group in their programs as pointed by Symantec and Kaspersky Lab.
Also, the Shadow Brokers hacker group on Tuesday has threatened to release further information to cater the ransomware attack in Windows 10 operating systems, network routers, and phones. Yet, the group has accepted the claim of exposing Window’s vulnerability details that have made the attack attainable.
Who Is Prone To WannaCry
WannaCry ransomware is targeting the Windows operating systems especially those versions which are outdated and Microsoft has halted their support to such XP windows in 2014. However, if you are on one of the latest versions of Microsoft and does not have updated those then you are also vulnerable to WannaCry attack.
Here’s how you could protect yourself from ransomware attack according to the Windows operating system you are using.
Update Your Windows System As Soon As Possible
If you are using the new versions of Windows i.e. from Windows Vista to Windows 10 then you could update it from the patches Windows had issued in March for the EternalBlue attack.
However, after the recent extensive WannaCry attack, Microsoft has issued a set of security patches for its older versions which it does not support for protecting against such malware. Here are those links which could help you;
Windows 8 x86
Windows 8 x64
Windows XP SP2 x64
Windows XP SP3 x86
Windows XP Embedded SP3 x86
Windows Server 2003 SP2 x64
Windows Server 2003 SP2 x86
Turn On the Auto Update
Most of the time users turn off the auto-update system due to varying reasons such as memory conservation. Also, the users disable this function because it causes interruption even if you are currently operating the Microsoft system which eventually struck their work on between. However, this issue has now been resolved by the Microsoft in their latest version, Windows 10.
So, if you are also one of those users who have disabled auto-update than going back to Window’s Control Panel and turn on it.
Avoid Opening Unauthentic Attachment
The ransomware spread is most often by the bogus E-mails. To remain unaffected from such vulnerability you should be vigilant especially if you receive an E-mail with an attachment from a sender unknown to you. However, sometimes malware sender poses to be a trusted source by pretending a person you are familiar with or if the mail seems doubtful. You could avoid such vulnerable E-mails and check their authenticity through backing them up on a protected device.
What Could I do If I Am Already Infected
Unfortunately, there is no way out to get rid of such ransomware and decrypt your files without paying the demanded ransom amount. This is the reason many of the organizations have paid the ransom amount if their computers had been attacked and they haven’t backed up their devices.
Yet, Bleeping computer guide could help you to remove WannaCry ransomware. However, it is not confirmed that you would get positive results from it.
Many security researchers and analysts have predicted an increase in similar ransomware attacks in 2017, that were continuously accelerating since past few years.