PHOTO: AMAZON
Security Companies Partner with Amazon to Introduce Key
Kwikset and Yale Partner with Amazon Key to let services and couriers into your home.
- By Sydny Shepard
- Oct 25, 2017
Amazon has been changing the game for a long time. From one-click purchases to two-day free shipping, the company has evolved in ways no one thought possible, including integrating with home security systems to allow services and couriers inside your door - when you are not home.
Amazon Key was announced on Wednesday as a "In-Home Kit" for those of use who are tired of receiving the "You've got a package!" email only to learn it has been swiped off your front porch. It also markets itself as a way to let "people you trust, like your family, friends, dog walker or house cleaner" into your home without having to leave a key under the mat.
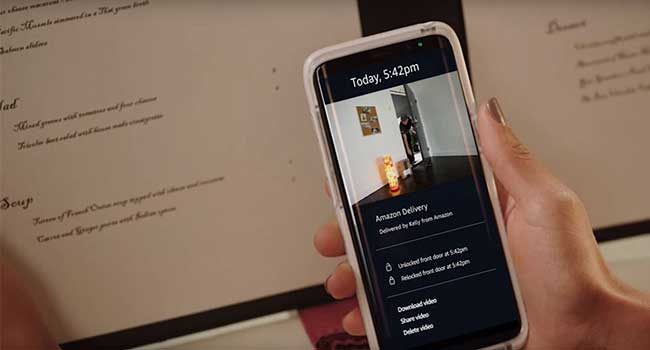
Exclusively for Prime members in "select cities and surrounding areas," Amazon Key works by integrating with smart locks from security companies such as Kwikset and Yale as well as the Amazon Cloud Cam.
In order to use the system, Amazon Prime members will select "free in-home delivery" at checkout and on delivery day, the user will receive a notification in the morning and another just before the delivery arrives at the address.
The courier will always knock first, and then request access. Amazon says it verifies with the delivery driver through an authentication process, turns on Cloud Cam to record, then grants access for the driver to deliver the package just inside the front door.
After the package is in place, the door is locked and a notification is sent to the user to inform them the deed is done. If for whatever reason, you don't want the delivery inside your home, you can "Block Access" up until the delivery time and the couriers will follow standard delivery procedures.
For the security industry, the partnership is huge. While smart homes, locks and DIY cameras are on the rise, this can only help companies like Kwikset and Yale expand their businesses.
"We are excited to provide our smart locks as an integral part of the new Amazon Key program," said Keith Brandon, Divisional Vice President - Residential Access Solutions (RAS) Sales and Marketing for Kwikset. "Clearly, the security that the smart locks deliver will play a critical role in the success of this innovative program, and we are confident that our locks will supply the highest level of security possible. We view Amazon’s choice of Kwikset as an affirmation of our smart locks’ capabilities.”
For Yale, its all about convenience for the customer.
“We’re thrilled to be a part of this new innovation from Amazon,” said Jason Williams, President, ASSA ABLOY U.S. Residential Group, which includes Yale Residential. “Yale’s years of expertise in security and smart lock technology and the new Amazon Key service will give Prime members peace of mind and provide a new level of convenience.”
About the Author
Sydny Shepard is the Executive Editor of Campus Security & Life Safety.