Deploying a Cloud Strategy
Why mid-market companies can—and should—deploy a video cloud strategy
- By Andreas Pettersson
- Feb 01, 2019
There’s enormous opportunity for all enterprises in the
cloud, and those in the middle market are taking note.
For mid-market businesses, the past few years have
been the dawn of a new era in cloud adoption—one
marked by significant growth in the maturity of IT
teams and a resulting push toward more sophisticated cloud deployments.
As a 2018 Techaisle report on SMB and mid-market IT maturity
segments revealed, 52 percent of mid-market enterprises can be
considered “advanced” as far as IT deployments. This means these
businesses have chosen to adopt cloud solutions. However, businesses
can face challenges in terms of platform selection, data/process management,
security and other factors that can delay deployment.
When it comes to video surveillance, there is a clear business case
for midsize businesses to migrate to the cloud. Benefits of cloudbased
video surveillance include better security, less hardware, data
redundancy, easier scalability, and perhaps most importantly, actionable
analytics. Ultimately, adopting cloud for video surveillance is a
key step for mid-market businesses toward managing their operations
like an enterprise business, but adopting video cloud technology demands
a strategic approach to avoid common hurdles.
Obstacles to Mid-market Cloud Video
Surveillance Adoption
Despite benefits of cloud-based video surveillance, many mid-market
organizations face challenges to deploying a video cloud strategy, including
prioritization and confidence in data security.
Prioritization. Mid-market businesses may not have the internal
resources compared to those of large enterprises. Whereas larger
organizations have dedicated teams focused on cloud mapping and
strategy—and actively working to identify functions, like surveillance,
that would be best served in the cloud—many mid-market
businesses do not. Instead, as the Techaisle study pointed out, a
significant percentage of mid-market enterprises approach cloud
purchasing on an ad-hoc, rather than strategic, basis. As a result,
cloud-based surveillance often takes a backseat to more immediate
business concerns.
Confidence. With mid-market organizations, there’s a widespread
lack of confidence that often accompanies a cloud move. A Deloitte
study of technology and the mid-market pointed out, this insecurity
stems from concerns that a move to the cloud represents a relinquishing
of control and a significantly heightened risk of data being compromised
or corrupted. This sense of insecurity can become even
more pronounced when it comes to surveillance footage, something
all businesses guard securely.
Business Benefits of Adopting
a Video Cloud Strategy
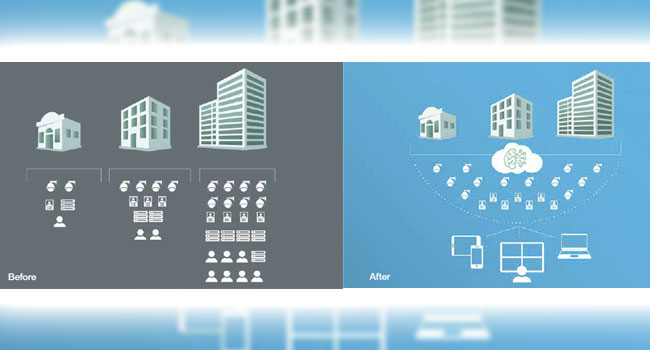
Central management of multi-site locations: On-premise video surveillance
presents a management and cost challenge for mid-market
businesses, especially as they scale. When organizations confine their video surveillance to on-prem, they must manually monitor hardware
in addition to upgrading and replacing it as needed. While this
approach works in the traditional sense, providing location-specific
video recordings to be reviewed live and at later dates, it prevents
organizations from seeing their business as one enterprise. Because
video data is siloed from site to site, mid-market businesses are unable
to correlate their data and lose out on actionable insights.
Scalability and security of cloud. In contrast to on-prem video surveillance,
a cloud-based approach is built to scale up securely and
without incurring additional technology and hardware costs. When
mid-market organizations migrate video to the cloud, they put themselves
in a flexible environment where their surveillance capabilities
can seamlessly keep pace with business growth. Software maintenance
is streamlined with automatic updates pushed out through the
cloud. Mid-market businesses migrating to cloud benefit from having
their software always up-to-date.
Machine learning and predictive analytics. By moving video to the
cloud, businesses can turn untapped surveillance data into a powerful
intelligence tool. The advancement of IoT and machine learning
enables companies to glean actionable insights from their previously
static video data. Combining video surveillance data with IoT sensor
data (such as access control and building management) within the
cloud allows businesses to identify patterns, investigate anomalies,
and optimize for efficiency.
With these benefits in mind, how can mid-market organizations set
themselves up for success by migrating video surveillance to the cloud?
Key Components for Successful Migration
Mid-market businesses pursuing cloud-based video surveillance
solutions must be careful to devise a strategy that is both realistic
for the business today and sustainable for the business in the future.
Certainly there are many factors to consider when evaluating cloudbased
surveillance providers, but three key components are critical
for successful migration to the cloud.
Identifying needs of today. There is no shortage of vendors providing
cloud-based surveillance solutions. When considering all the
various offerings, the evaluation process can be overwhelming. That’s
why it is critical to identify what your business needs today but still
keeping in mind what you may need in the future. For some, the needs
of today may simply be basic video data management. Consider this:
if a solution is unable to meet the needs of business today, how will
that solution cater to needs of the future?
One size does not fit all when it comes to cloud. Often, businesses
view cloud migration as a massive deployment that includes bulldozing
previous systems and processes. The beauty of cloud is that it
works with you. There is no right way to adopting cloud and the key
is understanding what makes sense for your business. For some organizations,
it means having a hybrid of both on-premise and cloudbased
solutions. For others, it means deploying cloud selectively at
certain sites or areas on a trial basis before having a comprehensive
migration plan.
Find a solution that add true value. There are many claims to what
cloud-based solutions can—or, more importantly, cannot—do when it
comes to video surveillance. As mid-market organizations consider solution
providers relative to the needs of their businesses today, it is important
to evaluate what vendors offer outside of the basics: security,
data redundancy, ease of scalability, and analytics.
Mid-market businesses have much to gain from
adopting cloud-based video surveillance, and the
beauty of cloud is that these organizations can
implement solutions as it best suits their business
needs.
This article originally appeared in the January/February 2019 issue of Security Today.