
A leaked MGM Grand memo posted by Vital Vegas states that beginning Feb. 4, "All guest elevators at MGM Grand will be modified only to allow access to the floor to which the guest is registered."
- By Jessica Davis
- Feb 08, 2019

Brent Sutherland, director of facilities management for Rock Co., said that the idea of arming the guards was proposed by Global Security Services, which supplies guards for the courthouse.
- By Jessica Davis
- Feb 08, 2019

According to Renee Wynn, NASA’s Chief Information Officer, NASA’s Security Operations Center (SOC) continued to operate 24/7 during the government shutdown, fighting cybersecurity threats.
- By Jessica Davis
- Feb 07, 2019
After multiple incidents in Richmond, Kentucky, both Richmond and Eastern Kentucky University police are urging area residents to take extra caution. The warnings follow the death of a missing woman, Amanda Bailey, the ongoing search for another woman, Savannah Spurlock, and a reported sexual assault near EKU’s campus.
- By Jessica Davis
- Feb 07, 2019

Having the right cybersecurity solutions in place now will go a long way toward helping you recover from a ransomware attack later.
- By Patrick Luce
- Feb 07, 2019
David Smail Appointed Executive Vice President and Chief Legal Officer; P. Gray Finney To Retire

The city expects to share the new center with CPS Energy, San Antonio Water System and VIA Metropolitan Transit, according to the San Antonio Business Journal. For security purposes, the organizations’ data streams would be kept separate.
- By Jessica Davis
- Feb 06, 2019

In a blog post Tuesday, Google announced two new updates to help users protect their data: Password Checkup and Cross Account Protection.
- By Jessica Davis
- Feb 06, 2019

The Fort Myers City Council has begun discussion of enforcing a city ordinance requiring security guard presence at convenience stores. The ordinance is in place, but is not being enforced at this time.
- By Jessica Davis
- Feb 06, 2019

Indianapolis seeks feedback form the community, officers in newly launched study on body-worn cameras.
- By Sydny Shepard
- Feb 05, 2019

Several agencies work together to create a comprehensive security plan to protect the State of the Union.
- By Sydny Shepard
- Feb 05, 2019

Airbus has disclosed the company is the victim of a cyberattack.
- By Sydny Shepard
- Feb 04, 2019
A proposed ban in San Francisco has introduced a series of rules that could dramatically limit enhanced surveillance.
- By Sydny Shepard
- Feb 04, 2019

Problems at a downtown apartment building leads to discussions on hiring retired officers to keep the peace.
- By Sydny Shepard
- Feb 04, 2019

The government commands a lot of information in data centers, local municipalities, homeland security, health, and every touch that governments have with private citizens and companies. The data can be classified, private and public-facing as in forms.
- By Carrie Goetz
- Feb 01, 2019
As with any high-profile entertainment complex that draws more than one million visitors every year, the stadium faces complex and constantly evolving security challenges.
- By John Burke
- Feb 01, 2019
The government has its fingers in everything, and it is necessary when you think about managing the nation’s infrastructure. Think carefully about securing the nation’s transportation system.
- By Ralph C. Jensen
- Feb 01, 2019
While attending religious services during the holiday season, a local congregant asked me if I had heard about the ISIS threat to local houses of worship in East Texas. I was not aware, but I started digging.
- By Ralph C. Jensen
- Feb 01, 2019
Everyone wants a piece of Kessel Run, the Air Force’s agile software development program, and attempts to replicate its success of are already underway.
- By Lauren C. Williams
- Feb 01, 2019

With all this plus four lobbies and multiple entry points, security at American Airlines Center is a 24/7 responsibility. Finding the right camera system for such a diverse environment presented a challenge.
- By Mark McCormack
- Feb 01, 2019
The way that smart cards are issued has changed dramatically in the last several years with the advent of cloud-based systems that enable the entire process to be managed and executed remotely, and with printer/encoder breakthroughs that significantly boost throughput, reliability and energy efficiency.
- By Robin Tandon
- Feb 01, 2019

Microwave sensors, also known as Radar, RF or Doppler sensors, detect walking, running or crawling human targets in outdoor environments.
- By Courtney Dillon Pedersen
- Feb 01, 2019

The Internet of Things (IoT) promises greater connectivity, which, when properly leveraged, can provide invaluable insight into our organizations and our operational environments. In the security sector, increased connectivity between sensors and systems gives us access to more data than we thought possible even just a few years ago.
- By Jimmy Palatsoukas
- Feb 01, 2019
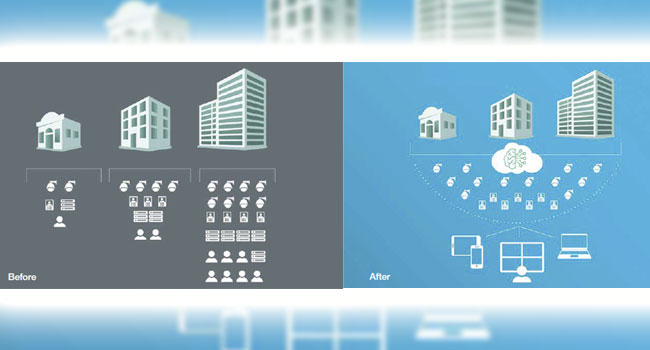
There’s enormous opportunity for all enterprises in the cloud, and those in the middle market are taking note.
- By Andreas Pettersson
- Feb 01, 2019

Originally designed as consumer devices, smartphones have become vital elements of both our personal and professional lives. Unfortunately, as sources and repositories of our most sensitive data, smartphones have quickly become a primary attack surface for hackers, cybercriminals and foreign spies.

College and university campuses aren’t immune from the same types of crime, such as burglary and assault, found in any small city where thousands of people live and work closely together. Yet overall, campuses remain a mostly safe place for young adults to learn and mature.
- By Paul Hefty
- Feb 01, 2019
When Paramount Studios, the longest operating and only remaining studio in Hollywood, wanted a preventative solution that would protect tourists and talent from car attacks, they contacted Perimeter Security Group, an integrator that has become one of the leading providers of perimeter security systems in the country.

At JFK Airport, immigration officers process hundreds of international passengers per flight. With the continual influx of people combined with limited staffing, law enforcement personnel are increasingly looking for technologies to enhance their efforts to deter illegal entry or trafficking and aid in crime investigation.
- By Richard Brent
- Feb 01, 2019

The technology behind today’s optical sensors and lenses has come a long way in trying to mimic some of the hallmark characteristics of the human visual system.

As part of the preparations for next year’s summer Olympics in Tokyo, Japan’s National Institute of Information and Communications Technology will check about 200 million internet-connected devices for potential cybersecurity vulnerabilities.
- By Jessica Davis
- Jan 31, 2019