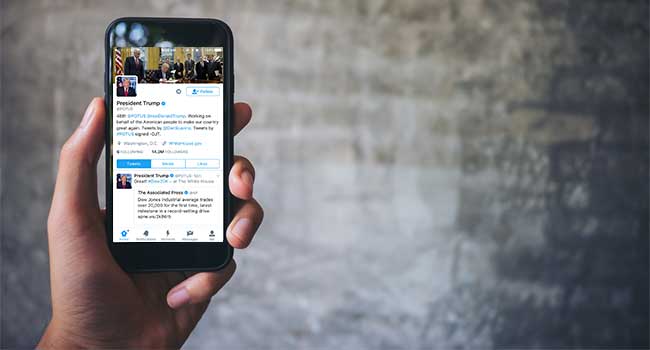
A hacker just wants President Trump to change his security settings on Twitter.
IDIS will mark two decades of innovation with customer, partner, and media events and recognitions across the globe in 2017
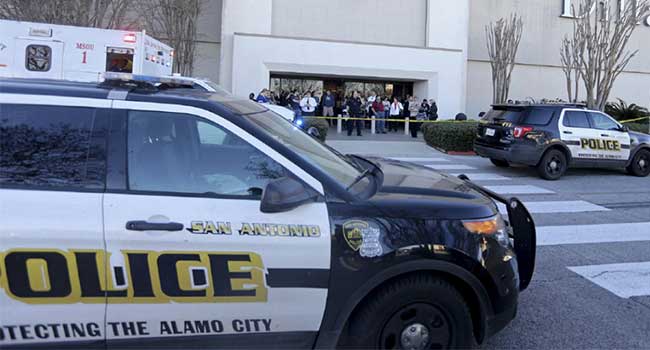
San Antonio police describe the event as a robbery gone, “really wrong.”

Security for the Inauguration is tight as protests swarm and a new president is sworn in.

Washington D.C. Police along with Secret Service and the FBI have been working to secure the Presidential Inauguration for over a year.
Premier provider of integrated Security, Fire, A/V and Electrical and Data Cabling/IT Infrastructures expands executive team & appoints veteran security industry expert to grow company and expand geographical reach
Feenics appointed Paul Cohn as Western Regional Business Development Manager.

A 15-year-old shot a teacher, three students and himself.

An officer in Little Elm, Texas was killed in a standoff with a gunman.
Here’s a little more detail about SDC’s new hires.
Bridge Safety and Security Bolstered with Key Management System

Houston and Miami saw a violent close to Martian Luther King Jr. Day when gunfire erupted injuring 12 people in all.
Hikvision provided cameras used for instruction and security at Kids World in Utah

4 people were killed in the gunfire and 1 was killed in the stampede as people attempted to leave the nightclub.

Essential questions you must ask a private security company to ensure that you have picked a right team for your property and workplace.
- By Ahmad Hamidi
- Jan 13, 2017

President-Elect chooses Rudy Giuliani to hold private industry meetings on cybersecurity.

Following two shooting incidents that killed one and injured nine more, the city is planning new security measures on Bourbon Street.
Hyperconverged infrastructure technology leader hires two seasoned industry professionals with deep experience in the region.
Bucks County becomes first agency in the State of Pennsylvania to implement ASAP; Alarm users to benefit from faster, more accurate emergency response.
Powerful access and control solution gives customers complete site control

Maybe it’s time for a different (and maybe more affordably efficient) approach.
- By Mike McCamon
- Jan 11, 2017
Vicon Valerus is built on open standards
More than $800K Raised in 2016 for Children and Families in Crisis Across the U.S.

Tuscaloosa police confirm a hostage situation at Alabama Credit Union.
Growth from 2016 carries over to 2017 with the addition of Mike Botten to the LVC sales team.
The addition of Charlie Johnson to the LVC sales team is an exciting one.

Markeith Loyd was captured on Tuesday, January 17.

A gunman opened fire, shooting at least 12 people and killing five of them.

While these topics may seem somewhat disparate, there is actually a common thread among them: They all have security officers and end users concerned.
- By Dean Wiech
- Jan 06, 2017

Security firm LogRhythm has predicted the internet will shut down for 24 hours in 2017 due to a massive DDoS attack.