
McAfee’s survey of 13 states considered “critical” in the presidential election found that 83 percent lacked .GOV validation, which verifies websites as being run by official local governments.
- By Haley Samsel
- Feb 05, 2020

The two men, who worked for Coalfire Labs, were caught up in a miscommunication between local law enforcement and the Iowa judicial branch, which hired the security firm to conduct testing.
- By Haley Samsel
- Feb 04, 2020

In 2019, TSA officers detected 4,432 firearms in carry-on baggage or on passengers, breaking the record set in 2018.
- By Haley Samsel
- Feb 03, 2020
Lupo comes to DICE Corporation from Kent Technologies in Miami, Florida
The award recognizes individuals for excellence in leading SIA committees and advancing member objectives
For organizations that wish to monitor their premises, video surveillance is most often the first solution they think of.
- By Chris Wildfoerster
- Feb 01, 2020
Today’s airports are bigger and more inviting than ever before. With so many people moving through them as well as an increasingly wide array of services on offer, they can start to feel like miniature cities.
- By David Lenot
- Feb 01, 2020

The new IEEE802.3bt PoE standard, also often referred to as PPoE or 4-Pair PoE, is a game-changing solution for powering 12VDC and 24VDC access control and related devices.
- By Ronnie Pennington
- Feb 01, 2020
One thing for certain this new year will be the advancement of technology. This is an ongoing phenomenon that brings new developments and solutions, and introduces completely new additions to the security industry.
- By Ralph C. Jensen
- Feb 01, 2020
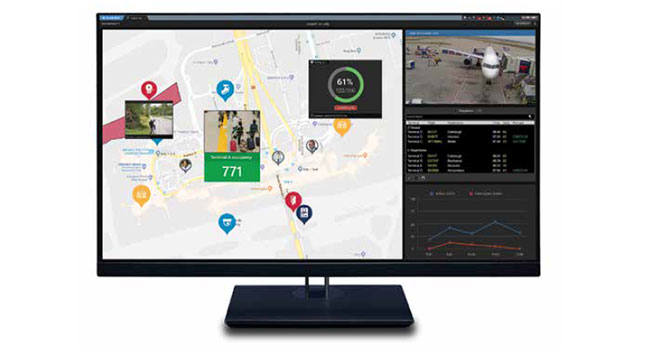
Artificial Intelligence (AI) continues to be a hot topic in the security industry. While true AI (a computer’s ability to think and act like a human) is still decades away, subsets of AI such as deep learning and machine learning have enabled computers to make significant strides.
- By Thomas Cook
- Feb 01, 2020

The security industry is being pressed to do more with less while dealing with the compounded issue of managing new internal and external threats on a daily basis.
- By Alex Asnovich
- Feb 01, 2020

For the sake of argument, let’s say you have a massive facility in a remote location that needs security.
- By Ralph C. Jensen
- Feb 01, 2020

The interconnectivity and integrations created by the Internet of Things (IoT) deliver many benefits, but because all devices and systems can be vulnerable to breaches, this hypoconnectivity can also have a major downside.
- By Ryan Zatolokin
- Feb 01, 2020

The threat landscape continues to evolve for every business. But banks and financial services companies face especially urgent demands.
- By Bill Wayland
- Feb 01, 2020

The interactive self-service kiosk has become a valuable, steadily growing commercial and informational tool since the launch of the first banking ATM in the 1980s. It is an essential part of our modern-day digital landscape.
- By Steve Spatig
- Feb 01, 2020

As every security professional knows well, the sector is changing rapidly thanks to emerging developments in artificial intelligence and the migration from traditional systems to integrated cyber and physical security operations.
- By Haley Samsel
- Feb 01, 2020

Access control advancements over the years have been notable: transitioning from keys and locksets, to cards and card readers, to the sophisticated access control management systems of today.
- By Kevin Anderson
- Feb 01, 2020

Thanks to an Illinois privacy law, eligible users will soon be able to apply for payments from Facebook for using facial scans without permission.
- By Haley Samsel
- Jan 31, 2020
Physical security and access control provider adds new member to top leadership team

The report, prepared by the National Institute of Standards and Technology, tested a variety of cybersecurity solutions in different IT environments to find out which methods were most effective in fighting ransomware.
- By Haley Samsel
- Jan 29, 2020

Over 40 groups sent a letter to the Privacy and Civil Liberties Oversight Board on Monday asking the agency to recommend that the executive branch put a moratorium on facial recognition.
- By Haley Samsel
- Jan 29, 2020

New Jersey police are banned from using Clearview AI’s app, and Twitter has demanded that the small company delete any photos collected from its website.
- By Haley Samsel
- Jan 28, 2020

Seventeen companies, including Microsoft and Cloudflare, are offering security assistance to federal campaigns that often cannot afford the services themselves.
- By Haley Samsel
- Jan 27, 2020

Lidefelt was previously CCO at ASSA ABLOY

Insurers have made “dramatic” increases in premiums for cyber-insurance and are considering lowering the ransom amounts they will pay.
- By Haley Samsel
- Jan 24, 2020

The agency says that the privacy risks to travelers will actually be lower with the facial scans, since they will no longer have to offer fingerprint data in order to enter the U.S.
- By Haley Samsel
- Jan 23, 2020

The regulations originally required gun retailers to have a backup of all video surveillance feeds, but has since been changed.
- By Haley Samsel
- Jan 22, 2020

Party leaders say they have taken steps to protect cybersecurity and that there will be paper records to verify each vote for the final results.
- By Haley Samsel
- Jan 22, 2020

While the ban is on the table, EU leadership ultimately says it would be a “far-reaching measure” with the potential to stifle the development of the technology.
- By Haley Samsel
- Jan 21, 2020

Lawmakers are trying to deter would-be hackers from carrying out cyber attacks that have paralyzed companies, hospital systems and local governments, including Baltimore’s city government.
- By Haley Samsel
- Jan 21, 2020