
Based on a recommendation by DHS and its intergovernmental partners, such as the Centers for Disease Control, President Trump has signed a proclamation on May 24 and amended on May 25 suspending the entry into the United States of any foreign nationals who were present in Brazil during the 14-day period preceding their entry or attempted entry into the United States.
Camden is introducing a new 36-inch tall stainless-steel model to their extensive line of aluminum, dark bronze and blue CM-75 Series ‘Column push plate switches.
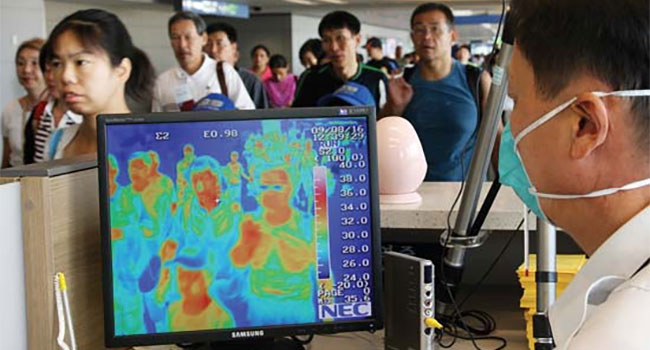
After TSA rolled out a series of new measures May 21, meant to encourage social distancing and stop the spread of COVID-19, the agency also is thinking about checking temperatures and thermal imaging to help screen for the virus.
- By Ralph C. Jensen
- May 27, 2020

13,720 cloud-managed cameras deployed in a cyber-secure city-wide surveillance program using 4G connectivity
Immix has announced today that Chris Brown will take over as CEO and will oversee the global business from end-to-end.

Experiencing an exponential rise of COVID-19 related security cases during the pandemic, International SOS sheds light on three emerging security challenges. These are alongside underlying security issues that the pandemic environment has and will continue to exacerbate.
- By Ralph C. Jensen
- May 26, 2020

Rep. Buddy Carter (R-Ga.) recently introduced H.R. 6929, the Advancing Facial Recognition Act, which requires the Federal Trade Commission, the U.S. Department of Commerce and other appropriate agencies
- By Joe Hollered
- May 26, 2020

An unidentified shooter has injured on security guard at Naval Air Station Corpus Christi, TX, today. It has been determined that the shooting is terrorism related, according to the FBI.
- By Ralph C. Jensen
- May 21, 2020

The legislation addresses the purchase of airport equipment, particularly passenger boarding bridges, from countries that are known for IP theft or national security threats.
- By Haley Samsel
- May 21, 2020
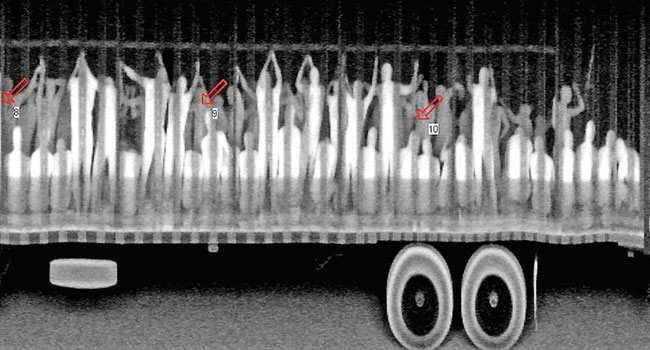
Human smugglers continue to plague law enforcement and society at large, despite the COVID-19 pandemic and without regards to several Customs and Border Protection policies and travel restrictions aimed at preventing the spread of the disease. Smugglers continue to place migrants in harm’s way.
- By Ralph C. Jensen
- May 20, 2020

Moran, who was president and COO of the company, died on May 14
Jay Geldmacher was most recently president and CEO of Electro Rent Corp.

Adapting thermography machines to address COVID-19 issues qualifies them as medical devices, which can pose unique challenges for businesses that are unfamiliar with the FDA.
- By Susan Kohn Ross
- May 19, 2020

A number of companies are either adding new features in response to the COVID-19 threat or developing new systems to identify if individuals are obeying guidelines.
- By Haley Samsel
- May 19, 2020

Not all internet users are careless about their online security. But many are still victims of cybercriminals and stalkers due to mistakes online.
- By Waqas Baig
- May 18, 2020

Organizers cite health and travel concerns for canceling the international show in Germany, which is held every two years.
- By Haley Samsel
- May 14, 2020

Industry associations keeping members informed about how the coronavirus crisis is affecting security businesses.
- By Ralph C. Jensen
- May 14, 2020

Man on Austin runway killed as Southwest Airlines plane lands.
- By Ralph C. Jensen
- May 14, 2020

The agents searched a trailer on May 9 and discovered 25 individuals attempting to enter the U.S.
- By Ralph C. Jensen
- May 13, 2020

TSA officer spent her stimulus check to support and thank front-line workers.
- By Ralph C. Jensen
- May 13, 2020
VRx leverages deep learning and native NetBox ecosystem integration for a unified security management experience

Businesses should switch their efforts towards an inbound marketing/communications strategy and manage relationships with existing customers during the pandemic.
- By Julian Arcila
- May 12, 2020
Computer Vision and LiDAR Motion Analytics Technologies Combined for Optimized Environments in Today’s Crowded World

With growing number of breaches, there is a huge need for more advanced measures to protect public sector data.
- By Warren Poschman
- May 12, 2020
Gunfire detection system manufacturer is hiring for several other positions
Building management can now install a free smart device that communicates with the SALTO controller and Amazon