
When it comes to cybersecurity, many organizations overlook IoT devices; but it is imperative that they are given equal consideration, as these devices are connected to the internet (i.e. printers, security cameras and smart home hubs) and can serve as an open door for cyber criminals.
- By Mark Sinanian
- Nov 04, 2022

SonicWall recently released new threat data through the third quarter of 2022. SonicWall recorded more than 4 billion malware attempts globally while year-to-date ransomware attempts in 2022 have already exceeded full-year totals from four of the last five years. In the recent 2022 SonicWall Cyber Threat Mindset Survey, 91% of organizations reported that they are most concerned about ransomware attacks, indicating a rise of anxiety among security professionals.

As cybersecurity awareness month continues to be a focus of discussion in October, new research conducted by Genetec, technology provider of unified security, public safety, operations, and business intelligence solutions, shows that cybersecurity remains a top concern for physical security professionals going into 2023.

Cloud data security is a serious challenge most organizations face today. The cloud was designed for collaboration where every file or data element can be shared with anyone halfway around the globe. Cloud data can also be copied, duplicated, modified and passed along very easily. To illustrate the challenge, think about 100 different variations of a redlined sensitive contract that need to be protected, and consider that each variant can have different access privileges.
- By Karthik Krishnan
- Oct 27, 2022
Cyber Awareness Month is upon us and we want to share some of our best practices for what organizations can do to enhance their security posture while remaining vigilant to stay ahead of threats as best they can.
- By Chris Strand
- Oct 20, 2022

Collectively, as an industry, we need to use the month of October to kick off an ongoing campaign that demonstrates the role each individual plays in both their own and their company’s security, as well as equips them with best practices to adopt a strong security posture. Here are a few practices that will ensure good cyber hygiene.

As retailers integrate their digital and physical shopping experiences to future-proof their business models, it’s never been more important to be aware of the cybersecurity vulnerabilities that can be created by digital transformation.
- By Chad Leedy
- Oct 10, 2022

Enterprises are struggling with three key data challenges. First, there is massive growth in data, often it increases exponentially from year to year. Equally, there is massive migration of data to the cloud. And finally, the data that is worth protecting has become a very complex environment – from Intellectual Property to financial data to business confidential information to regulated PII/PCI/PHI data.
- By Karthik Krishnan
- Oct 07, 2022
Walk into any grocery store today and you’ll see shelves of products claiming to be “organic” and “natural”, but, if you carefully inspect the ingredients, it becomes evident that most of the products are neither natural nor organic. Shoppers need to do their homework and look beyond the shiny labels. Security integrators are in a similar situation when it comes to cybersecurity.
- By Hans Kahler
- Oct 07, 2022

Cybersecurity Awareness Month allows us to reflect on our progress in information security and the components that still need work. As the term “cybersecurity” has made its way into mainstream vernacular (not just in sci-fi movies but in everyday conversations in the workplace and home), it would be tough to argue that cybersecurity awareness hasn’t grown tremendously in the past few years.
- By Bill Bernard
- Oct 05, 2022
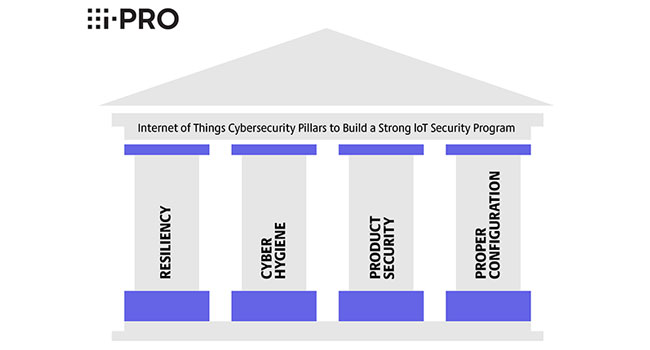
i-PRO Co., Ltd is proud to join with the Department of Homeland Security Cyber and Infrastructure Security Agency (DHS CISA) to raise awareness around cybersecurity for NCSAM (National Cyber Security Awareness Month).
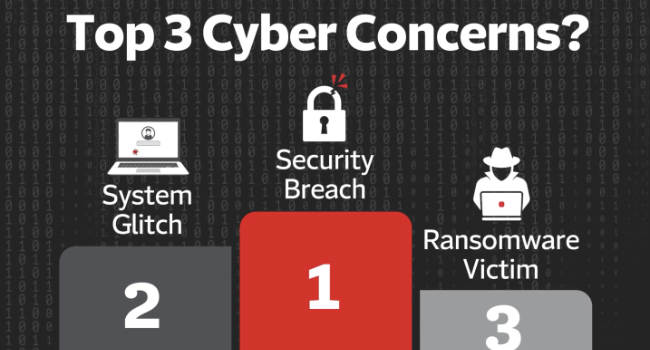
The Travelers Companies, Inc. recently released its 2022 Travelers Risk Index results, and for the third time in four years, the survey found that cyber threats were the top overall concern for business decision makers.
Commvault has announced the general availability of Metallic® ThreatWise™ an early warning system that proactively surfaces unknown and zero-day threats to minimize compromised data and business impact.
Versa Networks has announced that Gartner, a company that delivers actionable, objective insight to its executive and their teams, has given Versa Networks (Versa Operating System VOS™) the highest score for the Large Global WAN Use Case, as published in the 2022 Gartner Critical Capabilities for SD-WAN report.

We hear the term “best practices” a lot, but the truth is, there are still plenty of bad practices in use that put people and assets at risk every day. Many of those bad practices are grounded in one or more of the following myths that commonly lure people and organizations into a false sense of security.
- By Will Knehr
- Sep 19, 2022

Today’s businesses have seen increasing pressure to digitize their services, but few industries have felt this pressure more than the financial sector. Customers have grown to demand high-quality digital services, and the expectation is that these services are delivered with a high degree of security and reliability.
- By Kelly Ahuja
- Sep 09, 2022

Staring up into the sky on a clear night, you may be inclined to think that the small shining light moving gently across the black background is a shooting star or perhaps even a UFO. More likely, that tiny speck of light moving over your head is a satellite orbiting thousands of miles above the clouds
- By Patrick Shore
- Sep 09, 2022

The National Counterintelligence and Security Center (NCSC), the National Insider Threat Task Force (NITTF), the Office of the Under Secretary of Defense Intelligence and Security, the Defense Counterintelligence and Security Agency, and the Department of Homeland Security today launched the fourth-annual “National Insider Threat Awareness Month” (NITAM).

Amid increasing geopolitical tensions and consumer privacy concerns, business leaders (40%) ranked cybersecurity as the number one serious risk facing their companies. It’s not just top of mind for Chief Information Security Officers and Chief Risk Officers—executives across the entire C-suite ranked cybersecurity as a serious risk

Venafi, provider of machine identity management, today announced the findings of new research that evaluates the security impact of the increasing number of nation-state attacks and recent shifts in geopolitics. Venafi research into the methods used by nation-state threat actors shows the use of machine identities is growing in state-sponsored cyberattacks.