
As shoppers try to find deals in time to put presents under the tree, phishing campaigns are making it more difficult for consumers to tell if a website is naughty or nice.
- By Tyler Reguly
- Dec 18, 2019

The foundation has reported at least 30 incidents that targeted their Twitter account and followers last month with GIFs and videos of harmful strobe lights.
- By Haley Samsel
- Dec 18, 2019

The travel companies were fined for lax data security practices that potentially led to a breach affecting 880,000 payment cards globally.
- By Haley Samsel
- Dec 17, 2019

The cyberattack caused the city to completely shut down its network for several days, but did not affect emergency services.
- By Haley Samsel
- Dec 16, 2019

The ongoing debate over Apple and Facebook’s decision to not build “backdoors” for law enforcement to obtain encrypted messages continued to rage during a Senate hearing on Tuesday.
- By Haley Samsel
- Dec 12, 2019

The government has not linked the attack to the shooting, which is being investigated as an act of terrorism.
- By Haley Samsel
- Dec 11, 2019

After the FCC voted to ban telecommunications companies from using subsidies to buy equipment from Huawei, the Chinese company filed suit.
- By Haley Samsel
- Dec 10, 2019
This evolution not only keeps the IT department in a constant state of change, but also dramatically changes the way the overall business must adapt to stay competitive.
- By Jorge Del Prado Lera
- Dec 01, 2019
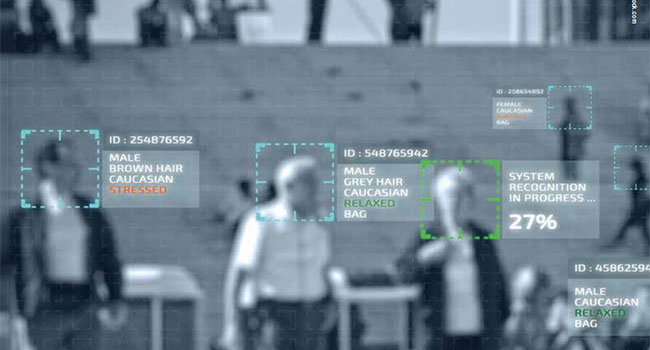
Video surveillance technologies continue to evolve. Some of the fastest-growing areas include AI-based video analytics and cloudbased video access and recording.
- By Brian Carle
- Dec 01, 2019
Not only does modern software architecture create a broader attack surface area, the accelerated DevOps methodology makes it harder to detect and remediate vulnerabilities.
- By Felicia Haggarty
- Dec 01, 2019

A cyber attack on an IT services provider has had major consequences for nursing homes, some of which may have to close down if they do not gain access to crucial patient data.
- By Haley Samsel
- Nov 27, 2019

The debate is raging over whether privacy is dead. But data security and privacy is what you make of it.
- By Tyler Reguly
- Nov 27, 2019

Huawei has started granting licenses to companies, including Microsoft, hoping to sell products to the Chinese tech giant.
- By Haley Samsel
- Nov 25, 2019

Malicious actors and state-sponsored hacking operations are expanding in countries outside of the “Big Four,” a new report finds.
- By Haley Samsel
- Nov 25, 2019

Auto companies are set to face a wider range of threats thanks to the rise of internet-connected vehicles, the FBI said in a recent report.
- By Haley Samsel
- Nov 22, 2019

The department store chain is notifying customers that hackers were able to scrape credit card data from online purchases for about a week.
- By Haley Samsel
- Nov 21, 2019

The Coalition Against Stalkerware hopes to be a resource for abuse victims and a pathway for security companies and advocacy organizations to work together.
- By Haley Samsel
- Nov 21, 2019

The company says there is no evidence of a security breach, but researchers suspect that account information was stolen using lists of previously hacked emails and passwords.
- By Haley Samsel
- Nov 20, 2019

Several services were shut down on Monday, but the governor says that it was a pre-emptive measure and that the ransomware did not infect all government servers.
- By Haley Samsel
- Nov 19, 2019

Authorities have arrested seven men across the U.S. who were part of the money laundering fraud scheme.
- By Haley Samsel
- Nov 15, 2019