Looking to the Future
Security tech trends to watch
- By Brian Carle
- Dec 01, 2019
Video surveillance technologies continue to
evolve. Some of the fastest-growing areas
include AI-based video analytics and cloudbased
video access and recording. Market
awareness will continue to drive interest,
which will, in turn, drive available solutions and offerings in 2020
and beyond.
Another trend to watch for is more VMS interfaces offering
greater access-to and control-of analytics information and access
control systems. This relates to the ongoing trend of consumers
moving towards unified video/access/analytics solutions.
Consumers will benefit in the coming years from simplified
offsite access, automated analysis of security events, and better
presentation and reporting of security information.
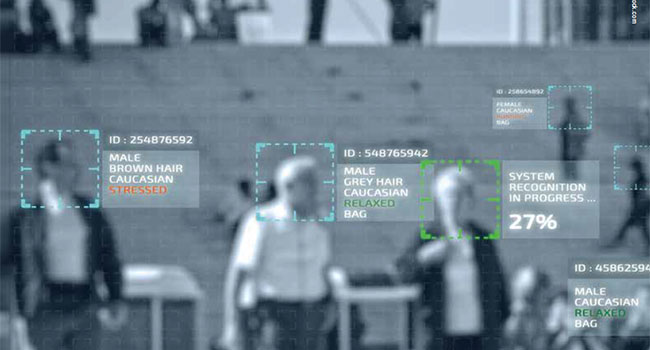
Cloud-based AI Analytics
The number of video analytics companies that have come into
being over the past three years is tremendous. The growth has
accelerated over that time due in great part to the popularity of
GPU hardware for applications beyond video games or CAD/
CAM, such as deep learning, computer vision and AI. However,
with more sophisticated analytics comes significant processing
requirements and high server hardware costs.
This high hardware cost puts analytics out of reach to most
video surveillance consumers. Depending on the analytic being
used, how many cameras are analyzed, camera resolution, etc.,
the upfront hardware cost of a deployment designed for processing
under a dozen cameras could easily exceed $10,000. As
a result, more analytics companies this year have begun offering cloud-based AI analytics.
The premise is simple: instead of deploying hardware onsite
for processing the analytics, video is streamed to the cloud,
where servers with the analytics software are hosted. The analytics
software is configured to provide alerts when detection
occurs. Upfront hardware costs are replaced with ongoing
monthly fees, making the acquisition cost of the technology
much more affordable.
The downside of this model includes lower scalability and
higher ongoing costs.
Scalability is limited by the consumer’s internet connection
speed, due to the need to upload video to the cloud for processing.
This is not likely to limit adoption for many consumers, because
it is not uncommon for only a subset of cameras at a site
to require analytics processing. In the event a high number of
cameras need to be analyzed, many cloud-based analytic solutions
can process video at a lower resolution and/or frame rate
while still achieving accurate detection.
Unified GUIs from VMS Platforms
Several prominent security product manufacturers have been
moving toward providing unified solutions, as opposed to focusing
on a single product area to develop a “best of breed” offering.
This move is driving a shift in thinking with consumers, putting
more emphasis towards deeper integration of complementary security
technologies, and a corresponding need to easily associate
security data.
As such, consumers today want access to all the information
in a single interface, which allows for the association of complementary
security data. As an example, if a cardholder presents an
access control credential to enter an area, the access control system
would show the name of the individual associated with the
credential that had unlocked the door. The video system would
display the person walking through the door. If the live video
and the access control records are presented together in the same
interface, a security officer would be able to see the person who
walked through the door was not the person associated with the
access credential.
Traditionally, most integrations occurred between video and
access control systems. Users would view the integrated video
and access data in the access control system interface. Technologies
such as point-of-sale integration, license plate recognition
and video analytics have become more widely used over the past
several years. Data from those technologies are best presented
within the video surveillance system, and as such, it makes sense
for video management platforms to move towards becoming a
unified interface.
Several VMS providers have already taken steps in this direction.
Either data from a complementary security system can
be presented alongside video and other data directly, or add-on
components for LPR, Analytics, and the like are purchasable
options from such vendors.
Hybrid Cloud VMS Functionality
Interest in cloud-based video surveillance deployments continues
to grow. Market awareness and education is high, due in
great part to the growing number of available solutions, including
those from mainstream VMS Platform providers. However,
full Cloud VMS deployments in the professional market are not
yet widely utilized as a result of high bandwidth costs, which
limits scalability.
Bandwidth costs disproportionally affect mid-sized to enterprise-
scale consumers, as a result of those consumers having
more cameras and therefore requiring more bandwidth. Even so,
benefits such as simplified remote access, which is discussed below,
and the ability to scale video retention without adding onpremise
storage may drive hybrid cloud features in traditional
VMS platforms.
Traditional deployments utilize on-premise servers with fixed
amounts of storage. This traditional model lacks flexibility many
users seek. As an organization’s requirements evolve, their video
retention requirements may also change.
A cloud-archiving service built into a VMS would allow the
VMS user to leverage cloud storage for long-term archiving on selected
cameras. This capability would remove the need to add additional
on-premise storage as retention requirements change. Using
cloud storage would allow the user to extend their storage capacity
at any time, by simply making configuration changes in the VMS
that would correspond to a monthly fee for cloud storage.
Another cloud feature that would benefit users of traditional
VMS systems is simplified remote access. Today, users of traditional
VMS deployments can set up remote access via the internet
using a VPN connection or by making the VMS server available
via port forwarding on an internet-connected router. Those configurations
may involve additional cost, configuration complexity
or security risks. A VMS-supporting, cloud-based video sharing
may allow an administrator to configure remote access by simply
checking a few boxes during configuration, causing the VMS to
connect securely to a cloud-based server where users can log-in to
view selected cameras. This setup removes the need for complex
configuration, which would need to be maintained every time
there are network changes affecting the VMS servers.
Staying Ahead of the Curve
Keeping an eye out for new technologies allows system designers
and consumers to identify those which may provide a cost benefit
or strategic advantage. With cloud offerings becoming more
mainstream, new uses for cloud architecture are coming to light
in video surveillance. Finally, with technology integrations and
video management interface development growing
more sophisticated, live monitoring practices
and security operations center design may be
affected in the coming years.
This article originally appeared in the November/December 2019 issue of Security Today.