
Unreleased episodes of HBO shows and Game of Thrones scripts have been leaked as a result of the attack.

At the Annual Black Hat conference, Facebook Chief Security Officer Alex Stamos told the crowd that something needs to change in the security industry.

Prime Minister Stefan Lofven said the lead was a “disaster” and it exposed the nation to harm.

Televisions, fridges and other internet-connected home appliances should carry a security rating, a police chief suggested.

While flexibility is empowering the workforce, it is also complicating data security.
- By David Konetski
- Jul 20, 2017

Elon Musk commented on Tesla’s cybsersecurity during his talk at the National Governor’s Association this weekend.

Guests at 14 properties bearing the name of Trump might have their credit card information breached by hackers.

China has passed a cybersecurity law that requires foreign firms to store data within the country.
First Time Cases, Investigators Linked Globally

The government’s proposed cybersecurity legislation was necessary to take proactive measures to protect critical infrastructure.

The whole world could use a cybersecurity upgrade.

Common sense dictates that it is easier to stop something from happening in the first place than to repair the damage after it has been done.
- By Siva G. Narendra
- Jul 01, 2017
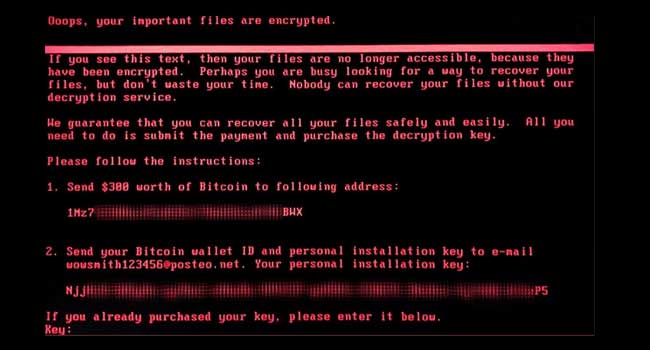
Yesterday, PC users across the world were asking for help as ransomware took data hostage and locked users out of their computers.
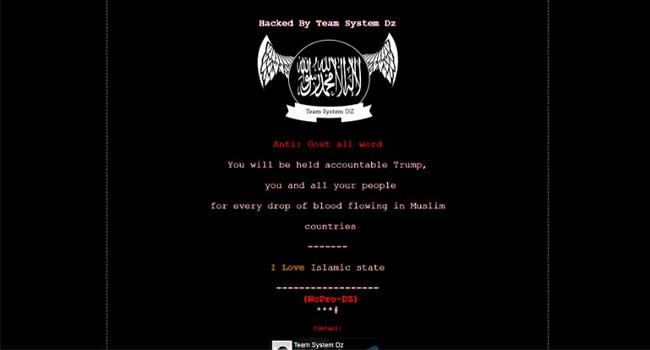
Government websites in Ohio, Maryland and New York were targeted.

Fewer than 90 email accounts with weak passwords are believed to have been hacked in “sustained” attack.

The education program is being developed in a partnership between the Girl Scouts and Palo Alto Networks.

For a relatively long time it seemed as if the password problem had been solved using SMS text messages.
- By Michael Lynch
- Jun 22, 2017

The cybersecurity arm of British intelligence services has reportedly suggested the global ransomware attack was launched from North Korea.

MacSpy is being advertised as the “most sophisticated Mac spyware ever.”

While many security teams at retailers are concerned about the potential for a big data breach, everyday security threats, like social engineering and shoplifting, are heightened in a world of omni-channel retail.
- By John Carter
- Jun 01, 2017