
While many security teams at retailers are concerned about the potential for a big data breach, everyday security threats, like social engineering and shoplifting, are heightened in a world of omni-channel retail.
- By John Carter
- Jun 01, 2017
The risk posed by hackers to the Internet of Things (IoT) is a hot topic and there have already been some serious real-world attacks.
- By Christopher Camejo
- Jun 01, 2017
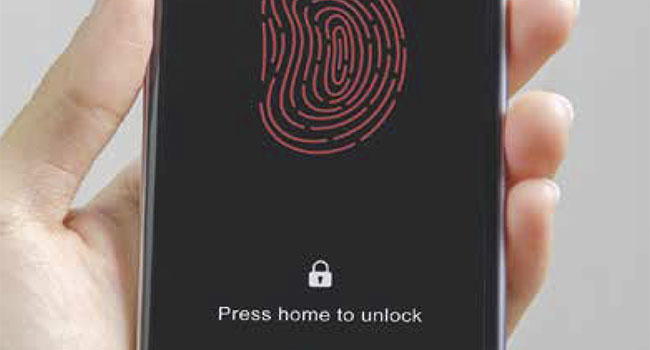
When used effectively, biometrics can contribute to safer cybersecurity practices.
- By Alisdair Faulkner
- Jun 01, 2017

Chipotle has released a nationwide list of stores that were targeted in the security breach between March and April of 2017.

Companies are asking China to delay the implementation of a new cybersecurity law amid concerns of how the legislation will affect personal information and cloud computing.
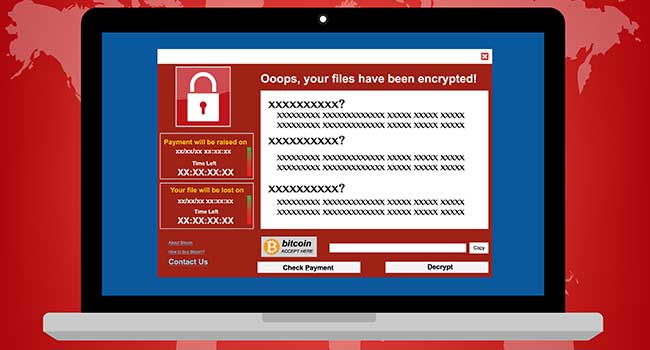
The WannaCry attack started last Friday and has affected 200,000 computers in almost 150 countries around the world.
- By Peter Butler
- May 18, 2017

What's next for agencies under the new executive order?
- By Mike Shultz
- May 16, 2017

Cybersecurity experts expect there will be more people falling victim to the worldwide cyberattack that hit on Friday.

Several British Hospitals say they are experiencing major computer problems as the result of a breach in cybersecurity.

President Trump has signed an executive order to strengthen the government’s cybersecurity.

Just days ahead of the French Presidential Election, candidate and now France’s president-elect announced his campaign had been hacked.

It’s time to take the pledge to improve your password habits.

Don't edit that Google Doc, at least not today.
In Kaua’i County, Hawaii, grants management has long been an important part of local government operations. It’s also been handled using paper.
- By Stephanie Kanowitz
- May 01, 2017

While the technology can add an effective, additional layer of cybersecurity, it’s not a catch-all. In fact, the very nature of biometric technology can introduce additional security gaps.
- By Alisdair Faulkner
- May 01, 2017
The IT approach to layered security for systems, infrastructure and data is increasingly impacting the security department, and with good reason.
- By Jeff Whitney
- May 01, 2017

Chipotle customers may have more to complain about than just an extra cost for guacamole.
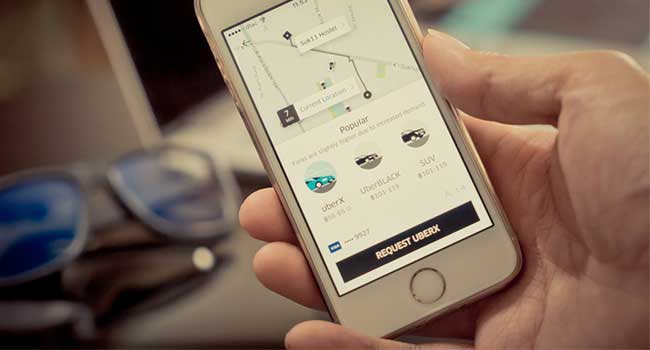
Uber knows where to find you even if you do delete the app.

In recent years a disturbing new trend is on the rise – cybercrime relating to tax returns and tax-related data. For its victims, Tax Day represents inconvenience and loss.
- By Ebba Blitz
- Apr 18, 2017

This age of connectivity is the age of possibility, and millions of people all over the world are taking advantage of the wonderful benefits these devices have to offer.