
Higher education leaders are asking the state for more money to help protect universities from IT security threats.
- By Matt Holden
- Mar 03, 2015

Criminals are using the platform to buy goods with stolen identities and credit cards
- By Matt Holden
- Mar 03, 2015

When selecting a PoE switch for an IP surveillance network, system integrators should be aware that not all switches are created equal. PoE switch manufacturers offer a variety of different features that can impact functionality and pricing.
- By Steven Olen
- Mar 01, 2015

Just how safe will the "Internet of Toys" be for your children?
- By Ginger Hill
- Feb 24, 2015
If cyber crime and identity theft isn't taken into consideration.

The search phrase was giving people advice for joining the radical group.
- By Matt Holden
- Feb 20, 2015

The United States may have permanently embedded surveillance and sabotage tools in a variety of networks.
- By Matt Holden
- Feb 18, 2015
Cloud-based service loads applications into the cryptographically-secured Trusted Execution Environment, embedded in the majority of leading Android smartphones.
KnowBe4 urges US institutions to take effective action to train employees before they fall victim to phishing attacks.

Executive actions aim to increase information sharing among private sector companies and federal law enforcement.
- By Matt Holden
- Feb 13, 2015

A line in the privacy policy states the television may record conversation and send it to a third party.
- By Matt Holden
- Feb 10, 2015

A report by U.S. Senator Edward Markey finds that most automakers don’t have the ability to find security breaches.
- By Matt Holden
- Feb 09, 2015

The President’s second, and final, national security strategy focuses on limiting how much the United States can shape world events.
- By Matt Holden
- Feb 06, 2015

The health insurance company is working with the FBI to come to a solution.
- By Matt Holden
- Feb 05, 2015

Paid out more than $1.5 million in 2014.
- By Ginger Hill
- Feb 03, 2015

The flaw could have potentially allowed hackers to open car doors.
- By Matt Holden
- Feb 02, 2015
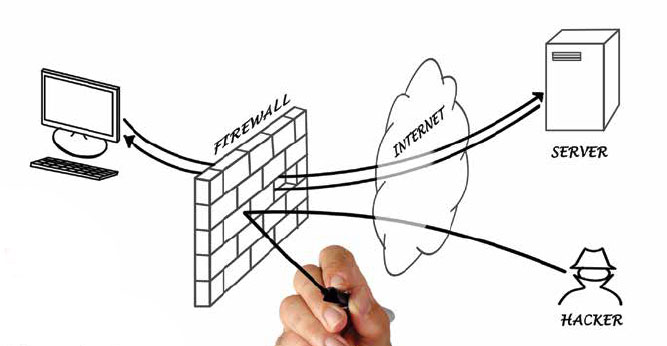
Money Movers Inc. is a fully PCI DSS compliant Electronic Funds Transfer Gateway processor. In plain English, that means we move a lot of data over a network.
- By Patrick E. Craig
- Feb 01, 2015

In a recent Hollywood comedy, Jason Segel’s character uttered the famous line, “Nobody understands the cloud. It’s a mystery.” And yet, all of us have been using the cloud for years: for online banking, online shopping, social media, email, sharing family photos and a host of other activities.
- By Jennifer Bruce
- Feb 01, 2015

The network-based physical security industry has matured rapidly over the past few years. As the technology and other components of security solutions have advanced, so too have the customer’s expectations.
- By Keven Marier
- Feb 01, 2015

Three strategies to keep you and your children safe from the prying eyes and ears of hackers.
- By Ginger Hill
- Jan 29, 2015