Safe City initiatives are one of the best ways to build an efficient, proactive security posture that strives to enhance safety and propel increased collaboration between city officials, security leaders, law enforcement and first responders.
- By Kevin Wine
- Apr 01, 2017
A study commissioned by Intel found that roughly 16 percent of Americans now own at least one smart home device, but nearly 70 percent of those surveyed believe smart homes will be as commonplace as smartphones in the next 10 years.
- By Jay Darfler
- Apr 01, 2017
As a provider of storage for video surveillance systems, the hardest part of my job is educating end-users, integrators and consultants on the best way to purchase storage for their systems.
- By Scott Seraboff
- Apr 01, 2017
The thought of a network or individual cameras getting hacked brought cybersecurity into the security picture pretty quickly. Cyber questions also arise when discussing cameras being manufactured in China.
- By Ralph C. Jensen
- Apr 01, 2017
Three years ago, Shrader Engineering had the privilege of designing one of the most unique security concepts in the region for the city of Sugar Land, Texas, Police Department. The security system forms a “virtual gateway” throughout the city.
- By Mark H. Friday
- Apr 01, 2017

The large geographical area and variety of locations and assets to protect make municipal video surveillance particularly challenging.
- By Ken LaMarca
- Apr 01, 2017

Glendale and Phoenix security officials feel confident in the security plan that will form around the men’s basketball tournament.
Clay Solutions B.V. has announced the release of Clay Locking Platform – the only API that makes it possible to integrate cloud-based access control to existing businesses and product portfolios.
SALTO Systems, a leading manufacturer of electronic access control solutions, has appointed Adam Reed to the commercial sales team position of Western Regional Sales Manager.
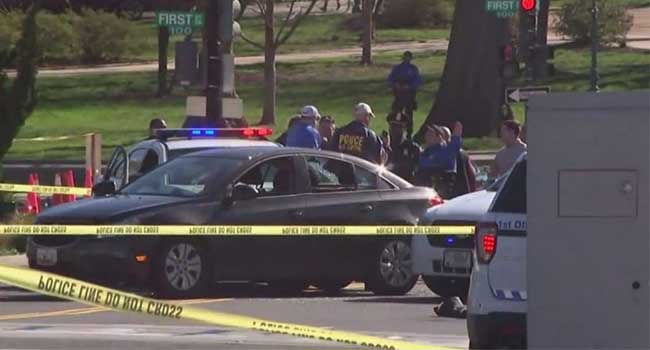
Shots were fired when U.S. Capitol Police tried to stop an erratic driver on Wednesday morning.