 For all passengers, airport security is that part of the journey where they - and the contents of their pockets - are checked through x-rays. In reality, of course, airport security is much more extensive and complex, especially as the number of people traveling continues to rise.
For all passengers, airport security is that part of the journey where they - and the contents of their pockets - are checked through x-rays. In reality, of course, airport security is much more extensive and complex, especially as the number of people traveling continues to rise.
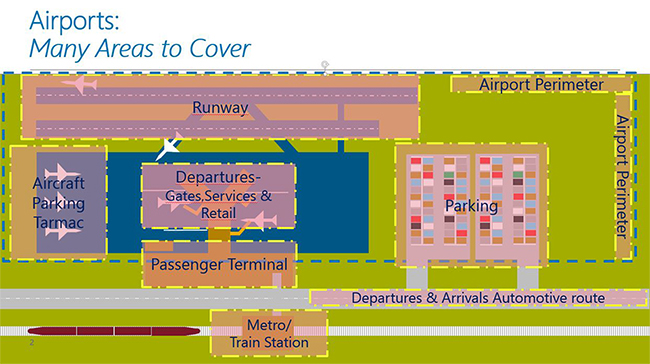
Airports face unique challenges, as they must ensure the safety and security of the public and their employees without impacting travel times, especially during busy travel seasons and periods of volatile weather. Add to this the continued awareness of global events and the growing trend of publicly accessible shopping areas, and we understand why airport security is so vital. In order to mitigate incidents before they result in unnecessary delays, costly shutdowns, or threaten public safety, these environments require physical security systems that are capable of detecting events and reducing response times.
There are multiple layers to airport security. Most passengers wouldn’t know that security is engaged as soon as they turn onto the roads that service the airport. Using a video surveillance system to monitor vehicular traffic, airport security is able to significantly improve public safety and operational efficiency by detecting vehicles traveling in lanes restricted for public transportation, blocking emergency lanes, or stopped in restricted areas. Combining video surveillance with video analytics makes it possible to measures traffic activity and obtain data and information vital for avoiding congestion, improving traffic flow during peak hours and maintaining clear access paths at all times.
Parking
Airport parking, ranging from departure drop-off lanes and passenger pick-up to short, term, long term, and rental parking, requires careful planning and the right technology. Otherwise, it can become a frustrating experience that requires extra time and energy to navigate.
To help keep track of all the vehicles coming and going at all hours of the day, airports use access control systems (ACS) to manage access to approved parking areas and automatic license plate recognition (ALPR) systems to manage their pay-by-plate parking service. In fact, using fixed ALPR cameras at public parking lots and garages allows for unmanned, 24/7 parking with automatic citation issuance by other LEP technologies.
When integrated with video surveillance, these same technologies also have a role to play in improving car park efficiency and passengers’ experiences. Some airports use data from the video management software (VMS) and ALPR to indicate the location of empty spots, assist car owners in locating their parked cars, prevent illegal parking, improve traffic flow by allowing automatic entry to authorized vehicles and ensure the smooth flow of traffic at peak hours.
The Terminal
Airport terminals require large numbers of personnel to run smoothly. From ticket agents to custodial staff, everyone has a job to do and an area in which to do it. It is important to provide personnel with the right access to perform their tasks and to ensure that all areas are appropriately monitored and protected.
Access control and video surveillance are key for promoting public security and safety inside airport terminals. By keeping records of personnel movement throughout the terminal and making it easy to manage access rights, an ACS allows airport security to effectively monitor and control access to hundreds of doors.
When unified with video surveillance, an ACS can also display cardholder pictures and credentials directly within video tiles, thereby allowing security to quickly verify cardholder information from one central application. And, to further secure highly-sensitive areas in the terminal, an airport can integrate biometrics, including retina scan and fingerprint readers, as part of its ACS.
With cameras spread throughout the terminal, passengers and restricted areas can be continuously monitored, allowing security to detect unattended objects, resolve instances of theft, detect loitering and motion in sensitive zones and track the movements of suspicious people in the terminal using pan-tilt-zoom (PTZ) cameras. Video surveillance can also be used by other groups at the airport to streamline operations throughout the terminal. For instance, customs and security groups can dispatch more agents when above average passenger congestion is detected and baggage handling can adjust carousel designations when planes are delayed.
Working with an advanced video management system (VMS), video analytics software can also process the data contained in real-time video streams to improve queue and crowd management by determining the number of people in a line, queues for ticketing, the flow of passengers exiting a certain area and the number of opened positions. This data can then be used to determine average waiting times at important locations and help managers make appropriate decisions about staffing and resource allocation.
The Perimeter
Although passengers generally access the airport’s perimeter only while on an aircraft, expanding security measures outside the terminal to the tarmac, aircraft taxi-ways, and the extended airport property is also important when it comes to ensuring public safety.
To secure its perimeter, airports use intrusion and perimeter protection technologies including microwave, fence detection and buried cable detection sensors, as well as trip-wire analytics, and strategically placed long-range, high-resolution cameras. With this unified approach, intrusion and perimeter detection devices trigger cameras to automatically pan-tilt-zoom into the target area for visual identification.  Video surveillance is then sent directly to the security monitoring center, or even as a mobile alert to the security director's smart phone, for immediate verification and response.
Video surveillance is then sent directly to the security monitoring center, or even as a mobile alert to the security director's smart phone, for immediate verification and response.
By deploying perimeter detection and long-range, high-resolution cameras, together with location-mapping tools, airports can minimize the risk of breaches going undetected and reduce response time when they do. Managing these devices and alarms directly from an integrated mapping system also helps operators quickly pinpoint other nearby cameras to get a broader view of the situation and confirmed location.
A Unified, IP-based, Security Solution
Due to the number of layers involved, ensuring the safety and security of the public at airports requires using multiple technologies and systems, from IP-based video cameras, advanced VMS, and video analytics to ACS, biometric locks, and perimeter intrusion technology. For airports, an IP-based platform is the most efficient and extensible way to deploy these systems, and the resulting integration and unification of these technologies ensures better collaboration for faster response times in the event of threats to public safety and security.
By standardizing security operations including monitoring, reporting and alarm management, into a single platform, a unified, IP-based, security solution can make operators more productive and reduce operational costs. Working with a unified, IP platform, like Genetec Security Center, an airport can manage its fixed and on-board systems under one platform and have a complete picture of all aspects of operations without having to switch between different applications.